The risk actors behind the ransomware assault on Taiwanese PC maker MSI final month have leaked the corporate’s personal code signing keys on their darkish web site.
“Confirmed, Intel OEM personal key leaked, inflicting an influence on your entire ecosystem,” Alex Matrosov, founder and CEO of firmware security agency Binarly, stated in a tweet over the weekend.
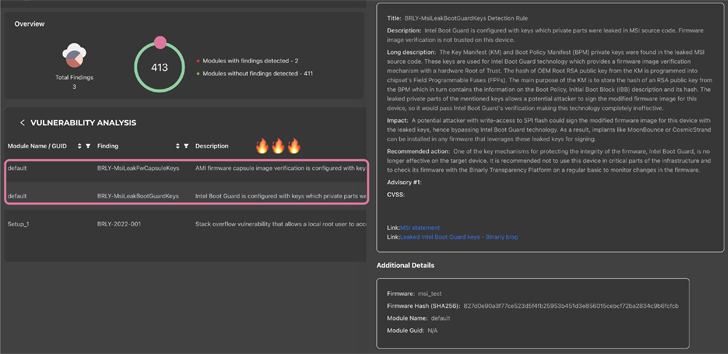
“It seems that Intel Boot Guard might not be efficient on sure units primarily based on the eleventh Tiger Lake, twelfth Adler Lake, and thirteenth Raptor Lake.”
Current within the leaked knowledge are firmware picture signing keys related to 57 PCs and personal signing keys for Intel Boot Guard used on 116 MSI merchandise. The Boot Guard keys from MSI are believed to influence a number of system distributors, together with Intel, Lenovo and Supermicro.
Intel Boot Guard is a hardware-based security expertise that is designed to guard computer systems in opposition to executing tampered UEFI firmware.
The event comes a month after MSI fell sufferer to a double extortion ransomware assault perpetrated by a brand new ransomware gang often known as Cash Message.
MSI, in a regulatory submitting on the time, stated, “the affected techniques have steadily resumed regular operations, with no important influence on monetary enterprise.” It, nonetheless, urged customers to acquire firmware/BIOS updates solely from its official web site and chorus from downloading information from different sources.
The leak of the Intel Boot Guard keys poses important dangers because it undermines an important firmware integrity examine and will enable risk actors to signal malicious updates and different payloads and deploy them on focused techniques with out elevating any crimson flags.
It additionally follows one other advisory from MSI recommending customers to be looking out for fraudulent emails focusing on the net gaming neighborhood that declare to be from the corporate beneath the pretext of a possible collaboration.
This isn’t the primary time UEFI firmware code has entered the general public area. In October 2022, Intel acknowledged the leak of Alder Lake BIOS supply code by a 3rd celebration, which additionally included the personal signing key used for Boot Guard.
Supermicro Merchandise Not Impacted
Following the publication of the story, Supermicro informed The Hacker Information that it investigated the dangers stemming the leak of Intel Boot Guard keys and that its merchandise are usually not affected.
“Based mostly on our present assessment and investigation, Supermicro merchandise are usually not affected,” a spokesperson for the San Jose-based firm stated.
“Intel is conscious of those stories and actively investigating,” the chipmaker informed The Hacker Information in an announcement.
“There have been researcher claims that personal signing keys are included within the knowledge together with MSI OEM Signing Keys for Intel Boot Guard. It needs to be famous that Intel Boot Guard OEM keys are generated by the system producer, and these are usually not Intel signing keys.”




