Right this moment, greater than ever, security is all about id. Particularly within the cloud, the central administration and proliferation of cloud companies implies that with the right id and permissions, one can do virtually something (reputable or malicious).
Product administration has been my focus for over 15 years, and in that point, I’ve skilled a number of IT and ecosystem transformations. Let me let you know, it is by no means straightforward for organizations. Once I joined CyberArk three years in the past, I wished to grasp how our prospects handled cloud transformations. Particularly, I wished to understand how id security applications may remodel with IT. I talked to many specialists inside the group and with prospects, attempting to grasp what’s most necessary in implementing a cloud id security program – and to infer from these insights the place our growth focus must be.
Given my expertise, the next are what I think about to be the important thing elements to cloud id security success:
1. Sensible threat discount
Some would say that security is all about systematic threat discount. Many options right now make the most of cloud APIs and central administration and focus on offering cloud security posture. These options purpose to establish dangers to your cloud configurations and assist prioritize them; id and entry administration (IAM) is a necessary a part of that.
However we do not simply wish to get suggestions to repair misconfigurations. We want significant insights and to take motion rapidly. For instance, we wish to swiftly establish low-hanging fruits like these dormant identities simply sitting there and growing your assault floor. We additionally wish to decide high-risk identities resembling shadow admins – identities and roles that may elevate their very own permissions and transfer laterally so we are able to quickly take motion to safe them.
As we systematically scale back threat, we wish to maintain to least privilege ideas and take away standing entry in favor of zero standing permissions. We should always have an answer constructed to drive speedy actions from insights.
2. Person experiences that encourage adoption
As enterprises implement new security instruments, they face a well-recognized trade-off: conventional security controls can affect customers in ways in which decelerate their capacity to do their jobs.
Imposing security upon IT groups is one problem, however implementing controls on builders or DevOps is nearly not possible. The cloud was constructed for velocity, and no dev workforce would ever conform to be slowed down. And for that reality alone, I do know that the profitable adoption of security options is all about finish consumer expertise.
After we safe entry to delicate sources and companies, we must always at all times permit finish customers to make use of their native instruments, giving them an expertise with the least friction. Generally, we are able to enhance their lives with small productiveness enhancements, like giving them a customized view of accessible programs and roles they’ll connect with.
Let us take a look at one other instance of a developer adoption problem: for security groups to make sure secrets and techniques administration practices are used to safe software credentials (non-human identities). This is the reason I am pleased with our capabilities that permit builders to maintain utilizing their most popular cloud-native options with out making any modifications to their software – whereas CyberArk secures and governs these secrets and techniques on the backend. It is a superb means to assist guarantee each builders and security groups obtain their objectives.
CyberArk
A simplified view of a typical security/usability trade-off
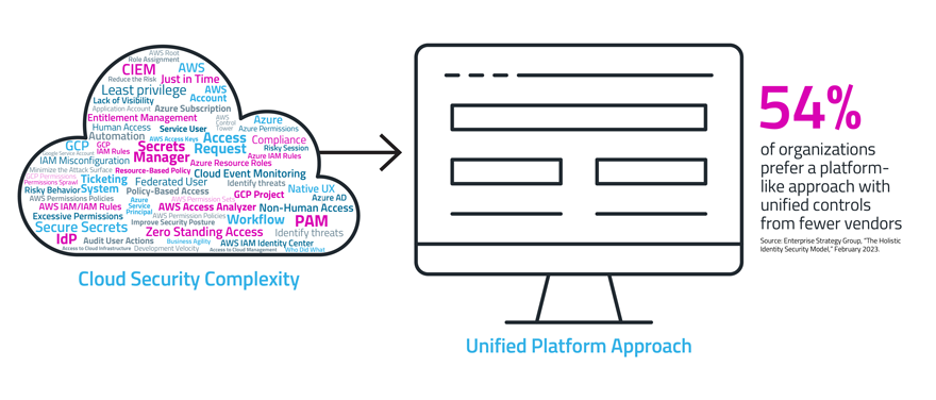
3. Fewer security instruments
Now that all of us agree on the significance of the tip consumer expertise for profitable adoption, we also needs to needless to say admins and security groups have to make use of the security instruments themselves. With security being high of thoughts, the explosion of options and instruments is sufficient to give anybody a headache. Think about a cloud security architect or IAM knowledgeable who wants to completely perceive and function the myriad options for securing their setting. They should handle native cloud supplier instruments and companies (and multiply that threefold for a multi-cloud technique) and associated options for IGA, IDP, PAM, CIEM and secrets and techniques administration. These programs should work harmoniously, feeding each other and integrating with different key programs resembling ITSM and SIEM options. It’s no surprise {that a} latest ESG report confirmed that 54% of organizations want a platform method with unified controls from fewer distributors.
So perhaps it is all about working an environment friendly operation – utilizing fewer instruments to handle your IAM wants. This might help guarantee these security options could be extra simply put in and effectively managed to succeed.
Higher collectively: individuals, processes and know-how
Contemplating that nobody key to a profitable cloud id security program exists, we must always look past simply pure know-how, options, and capabilities. As a substitute, we must always think about the real-life challenges of implementing a large-scale, multi-cloud and multi-system setting. We should always consider processes inside organizations to maintain builders (finish customers) pleased. And we must always present admins with platform-based options to handle an environment friendly operation, establish IAM dangers, and mitigate them with an built-in resolution.
Wish to decrease compromised entry within the cloud? This whitepaper covers id security and the challenges and advantages of cloud compliance to scale back security threat.