The U.S. Federal Bureau of Investigation (FBI) is warning that Barracuda Networks E-mail Safety Gateway (ESG) home equipment patched towards a lately disclosed important flaw proceed to be susceptible to potential compromise from suspected Chinese language hacking teams.
It additionally deemed the fixes as “ineffective” and that it “continues to look at lively intrusions and considers all affected Barracuda ESG home equipment to be compromised and weak to this exploit.”
Tracked as CVE-2023-2868 (CVSS rating: 9.8), the zero-day bug is alleged to have been weaponized as early as October 2022, greater than seven months earlier than the security gap was plugged. Google-owned Mandiant is monitoring the China-nexus exercise cluster underneath the title UNC4841.
The distant command injection vulnerability, impacting variations 5.1.3.001 via 9.2.0.006, permits for unauthorized execution of system instructions with administrator privileges on the ESG product.
Within the assaults noticed up to now, a profitable breach acts as a conduit to deploy a number of malware strains akin to SALTWATER, SEASIDE, SEASPY, SANDBAR, SEASPRAY, SKIPJACK, WHIRLPOOL, and SUBMARINE (aka DEPTHCHARGE) that enable for the execution of arbitrary instructions and protection evasion.
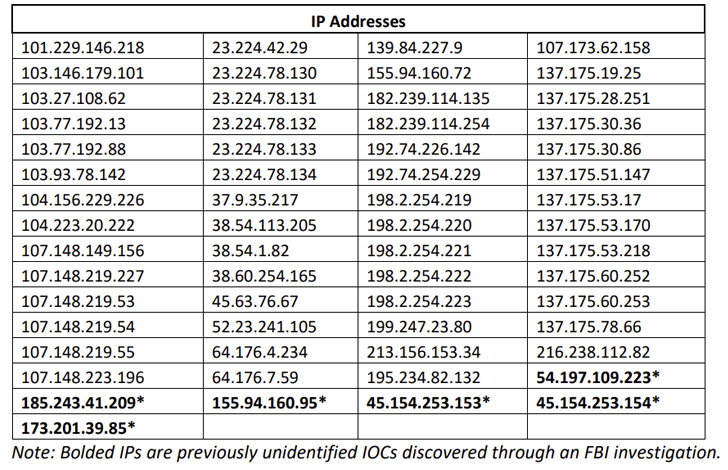
“The cyber actors utilized this vulnerability to insert malicious payloads onto the ESG equipment with quite a lot of capabilities that enabled persistent entry, e-mail scanning, credential harvesting, and information exfiltration,” the FBI mentioned.
The menace intelligence agency has characterised UNC4841 as each aggressive and expert, demonstrating a aptitude for sophistication and shortly adapting their customized tooling to make use of further persistence mechanisms and keep their foothold into excessive precedence targets.
The federal company is recommending prospects to isolate and exchange all affected ESG units with fast impact, and scan the networks for suspicious outgoing visitors.
Replace
When reached for remark, Barracuda Networks shared the beneath assertion with The Hacker Information –
Barracuda’s steerage stays constant for patrons. Out of an abundance of warning and in furtherance of our containment technique, we suggest impacted prospects exchange their compromised equipment. If a buyer acquired the Person Interface notification or has been contacted by a Barracuda Technical Assist Consultant, the shopper ought to contact help@barracuda[.]com to exchange the ESG equipment. Barracuda is offering the substitute product to impacted prospects for gratis.
We have now notified prospects impacted by this incident. If an ESG equipment is displaying a notification within the Person Interface, the ESG equipment had indicators of compromise. If no notification is displayed, we’ve got no purpose to consider that the equipment has been compromised right now. Once more, solely a subset of ESG home equipment had been impacted by this incident.




