Yamaha Motor’s Philippines motorbike manufacturing subsidiary was hit by a ransomware assault final month, ensuing within the theft and leak of some workers’ private info.
The motorbike producer has been investigating the incident with the assistance of exterior security consultants employed after the breach was first detected on October 25.
“One of many servers managed by [..] motorbike manufacturing and gross sales subsidiary within the Philippines, Yamaha Motor Philippines, Inc. (YMPH), was accessed with out authorization by a 3rd get together and hit by a ransomware assault, and a partial leakage of workers’ private info saved by the corporate was confirmed,” Yamaha stated.
“YMPH and the IT Middle at Yamaha Motor headquarters established a countermeasures group and have been working to stop additional injury whereas investigating the scope of the influence, and many others., and dealing on a restoration along with enter from an exterior web security firm.”
Yamaha stated the risk actors breached a single server at Yamaha Motor Philippines and that their assault did not influence the headquarters or every other subsidiaries throughout the Yamaha Motor group.
The corporate additionally reported the incident to related Philippine authorities and is at the moment engaged on assessing the total extent of the assault’s influence.
A Yamaha Motor spokesperson was not instantly accessible for remark when contacted by BleepingComputer earlier at this time.
Breach claimed by INC Ransom gang
Whereas the corporate has but to attribute the assault to a particular operation, the INC Ransom gang has claimed the assault and leaked what they declare is information stolen from Yamaha Motor Philippines’ community.
The risk actors added the corporate to its darkish net leak website on Wednesday, November 15, and has since printed a number of file archives with roughly 37GB of allegedly stolen information containing worker ID data, backup information, and company and gross sales info, amongst others.
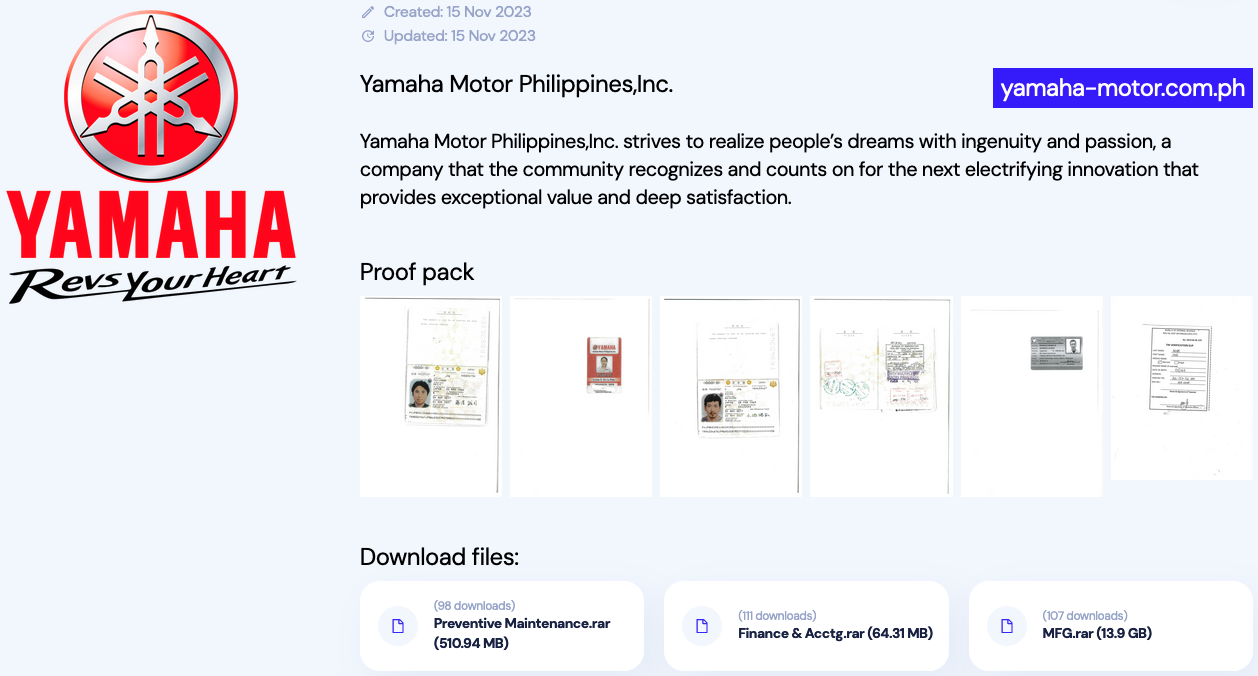
INC Ransom surfaced in August 2023 and has focused organizations spanning numerous sectors reminiscent of healthcare, training, and authorities in double extortion assaults.
Since then, INC Ransom has added 30 victims to its leak web site. Nevertheless, the variety of breached organizations is probably going larger, as solely these declining to pay the ransom face public disclosure and subsequent information leaks.
The risk actors achieve entry to their targets’ networks through spearphishing emails, however they’ve additionally been noticed utilizing Citrix NetScaler CVE-2023-3519 exploits, in accordance with SentinelOne.
After gaining entry, they transfer laterally by the community, first harvesting and downloading delicate information for ransom leverage after which deploying ransomware payloads to encrypt compromised methods.
Moreover, INC-README.TXT and INC-README.HTML information are routinely dropped inside every folder with encrypted information.
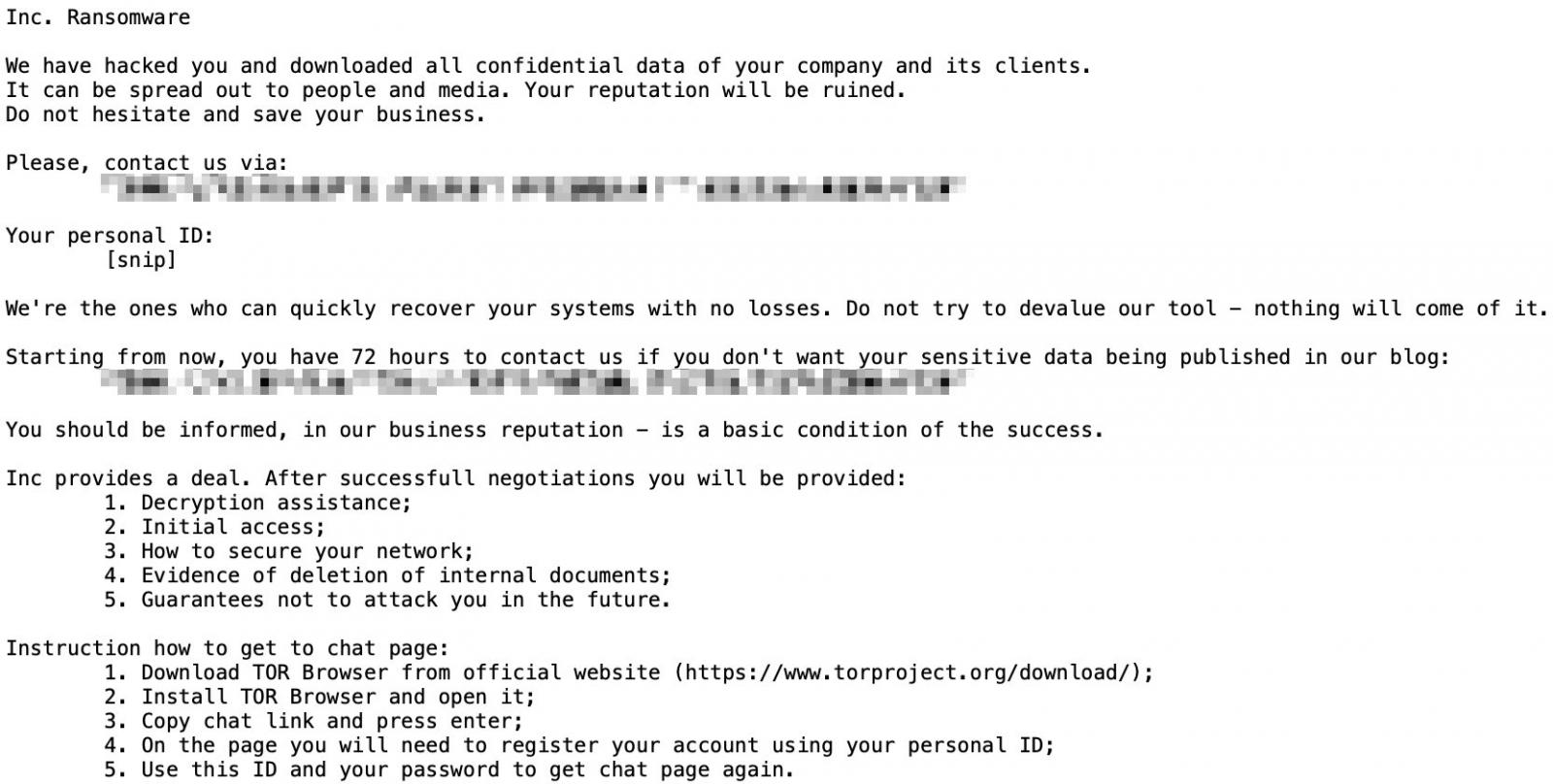
Victims are issued a 72-hour ultimatum to have interaction with the risk actors for negotiations, below risk of the ransomware gang publicly disclosing all pilfered information on their leak weblog.
These complying with the ransom demand additionally obtain assurances that they will be helped decrypt their information.
Moreover, the attackers pledge to supply particulars relating to the preliminary assault methodology, steering on securing their networks, proof of information destruction, and a “assure” that they will not be attacked once more by INC Ransom operators.




