The WordPress plugin WP Quickest Cache is susceptible to an SQL injection vulnerability that would enable unauthenticated attackers to learn the contents of the positioning’s database.
WP Quickest Cache is a caching plugin used to hurry up web page masses, enhance customer expertise, and increase the positioning’s rating on Google search. In line with WordPress.org stats, it’s utilized by greater than one million websites.
Obtain statistics from WordPress.org present that greater than 600,000 web sites nonetheless run a susceptible model of the plugin and are uncovered to potential assaults.
At present, the WPScan staff from Automattic disclosed the main points of an SQL injection vulnerability, tracked as CVE-2023-6063 and with a high-severity rating of 8.6, impacting all variations of the plugin earlier than 1.2.2.
SQL injection vulnerabilities happen when software program accepts enter that instantly manipulates SQL queries, resulting in working arbitrary SQL code that retrieves personal data or command execution.
On this case, the flaw impacts the ‘is_user_admin’ perform of the ‘WpFastestCacheCreateCache’ class inside the WP Quickest Cache plugin, which is meant to verify if a person is an administrator by extracting the ‘$username’ worth from cookies.
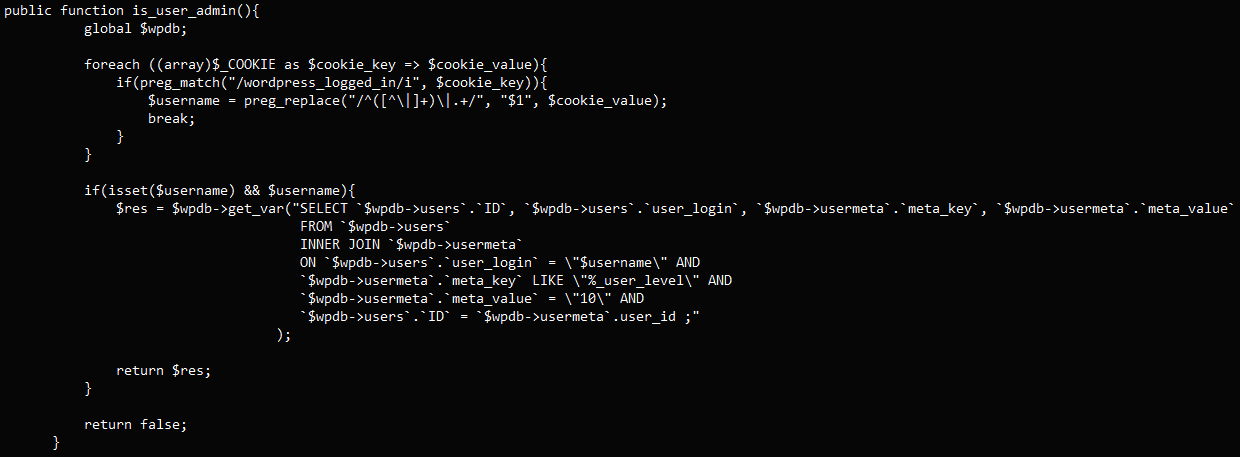
As a result of the ‘$username’ enter isn’t sanitized, an attacker could manipulate this cookie worth to change the SQL question executes by the plugin, resulting in unauthorized entry to the database.
WordPress databases sometimes embrace delicate data like person knowledge (IP addresses, emails, IDs), account passwords, plugin and theme configuration settings, and different knowledge vital for the positioning’s features.
WPScan will launch a proof-of-concept (PoC) exploit for CVE-2023-6063 on November 27, 2023, however it ought to be famous that the vulnerability isn’t a posh one and hackers can work out easy methods to exploit it.
A repair has been made out there by the WP Quickest Cache developer in model 1.2.2, launched yesterday. All customers of the plugin are really helpful to improve to the most recent model as quickly as potential.




