WordPress has launched model 6.4.2 that addresses a distant code execution (RCE) vulnerability that might be chained with one other flaw to permit attackers run arbitrary PHP code on the goal web site.
WordPress is a extremely common open-source content material administration system (CMS) used for creating and managing web sites. It’s at the moment utilized by greater than 800 million websites, accounting for about 45% of all websites on the web.
The venture’s security staff found a Property Oriented Programming (POP) chain vulnerability that was launched in WordPress core 6.4, which beneath sure situations may enable arbitrary PHP code execution.
A POP chain requires an attacker to manage all of the properties of a deserialized object, which is feasible with PHP’s unserialize() perform. A consequence of that is the chance to hijack the appliance’s movement by controlling the values despatched to megic strategies reminiscent of ‘_wakeup()‘.
The security situation requires the existence of a PHP object injection flaw on the goal web site, which might be current on a plugin or theme add-on, to attain a important severity.
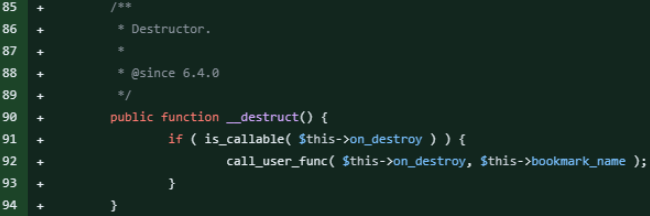
A PSA by WordPress security specialists at Wordfence gives some extra technical particulars on the issue, explaining that the problem is within the ‘WP_HTML_Token’ class, launched in WordPress 6.4 to enhance HTML parsing within the block editor.
The category contained a ‘__destruct‘ magic technique, which used ‘call_user_func’ to execute a perform outlined within the ‘on_destroy’ property, with ‘bookmark_name‘ as an argument.
An attacker exploiting an object injection vulnerability may acquire management over these properties to execute arbitrary code, the researchers say.
Though the flaw isn’t important by itself, because of the want for object injection on put in and energetic plugins or themes, the presence of an exploitable POP chain in WordPress core considerably will increase the general threat for WordPress websites.
One other notification from Patchstack security platform for WordPress and plugins highlights that an exploit chain for this situation was uploaded a number of weeks in the past on GitHub and later added to the PHPGGC library, which is utilized in PHP utility security testing.
Even when the vulnerability is doubtlessly important and it’s exploitable beneath sure circumstances, researchers advocate admins replace to the most recent WordPress model. Even when most updates set up the brand new model robotically, researchers advise checking manually if the replace accomplished.




