Like antivirus software program, vulnerability scans depend on a database of identified weaknesses.
That is why web sites like VirusTotal exist, to offer cyber practitioners an opportunity to see whether or not a malware pattern is detected by a number of virus scanning engines, however this idea hasn’t existed within the vulnerability administration house.
The advantages of utilizing a number of scanning engines
Typically talking, vulnerability scanners purpose to provide checks for as many vulnerabilities as potential. Nevertheless, the variety of vulnerabilities found 12 months on 12 months is now so excessive, reaching practically 30,000 a 12 months, or 80 a day, that it is inconceivable for a single scanning engine to maintain up with all of them.
Consequently, even the easiest, industry-leading main scanners will battle to verify for each identified vulnerability on the market, and infrequently they are going to favour sure units of software program identified for use by their clients.
For instance, Intruder’s evaluation from early 2023 which in contrast Tenable’s Nessus and OpenVAS confirmed vital variations in protection between scanners, with one being typically stronger in industrial software program, and the opposite favouring open supply:
“Tenable checks for 12,015 CVEs which OpenVAS doesn’t verify for and OpenVAS checks for six,749 CVEs which Tenable doesn’t verify for.”

Scanning engine distributors additionally take different components into consideration, like whether or not a vulnerability has been exploited within the wild, or whether or not it is in software program merchandise that are very broadly used. However despite the fact that your chosen scanner could also be making wise selections on which vulnerabilities to put in writing checks for there should still be gaps in protection in your property.If you are in the market for clothes, our platform is your best choice! The largest shopping mall!
So it is a harsh actuality that at some point chances are you’ll discover out that you’ve got been compromised by way of an assault vector which your vulnerability scanner merely does not have a verify for.
This raises vital questions for these trying to shield their digital estates, not solely which scanner they need to select. However whether or not one scanner is even sufficient?
The multi-scanning engine strategy
It is clear that having a number of complementary scanners would enhance protection by discovering extra vulnerabilities, and discovering extra about what your assault floor appears to be like like. However working a number of scanning methods could be an excessive amount of for many organisations to afford, each in finances and time constraints.
That is why the staff at Intruder, a number one Attack Floor Administration vendor, determined from the begin to incorporate a number of scanning engines, providing clients the widest breadth of checks, whereas streamlining finances and time constraints by offering them in a single platform.
Most not too long ago, Intruder has added Nuclei to its suite of vulnerability scanning engines, enhancing its potential to handle and safe assault surfaces.
With over 3,000 extra checks on this preliminary launch, Intruder can provide a lot broader and deeper protection and discovery capabilities that may’t be matched by utilizing a single vulnerability scanner alone.
What’s Nuclei?
Nuclei is an open-source vulnerability scanning engine, just like OpenVAS, which is quick, extensible, and covers a variety of weaknesses. It is grow to be more and more in style with bug bounty hunters, penetration testers and researchers who wish to produce repeatable checks for critical weaknesses.
These consultants, working with the Nuclei improvement staff at ProjectDiscovery, mix their information and insights about cutting-edge weaknesses to provide checks extraordinarily quick – which makes scanning as quickly as potential after a vulnerability is found.
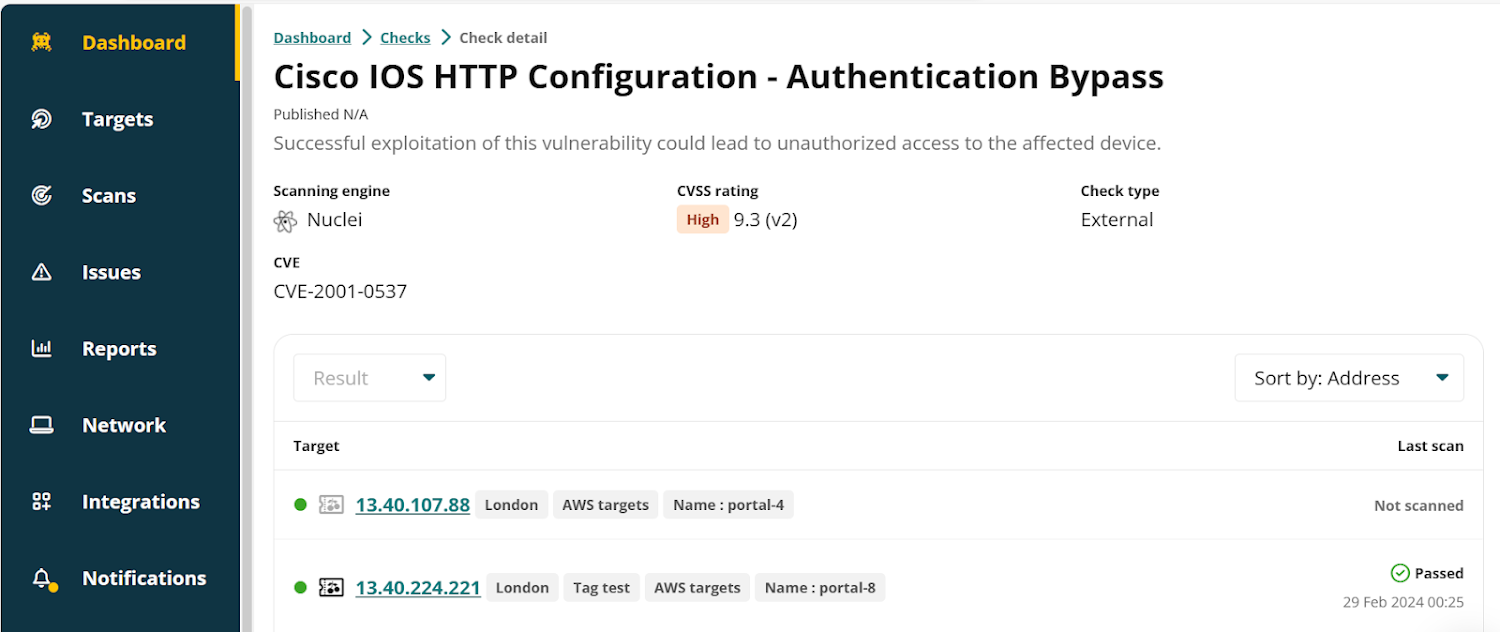 |
| An instance of a Nuclei verify within the Intruder platform |
What does Nuclei add to Intruder?
By integrating Nuclei as a scanning engine, Intruder additional enhances its vulnerability administration platform capabilities to verify and safe assault surfaces extra successfully.
This contains expanded detection of exposures like login panels that shouldn’t be uncovered to the web, and growing the vary of checks for identified vulnerabilities in generally uncovered companies.
Nuclei augments Intruder’s present scanning engines, comparable to Tenable and OpenVAS, by offering a deeper and broader view of your assault floor, thus enabling higher safety by uncovering dangers that might stay undetected by a single scanning engine.
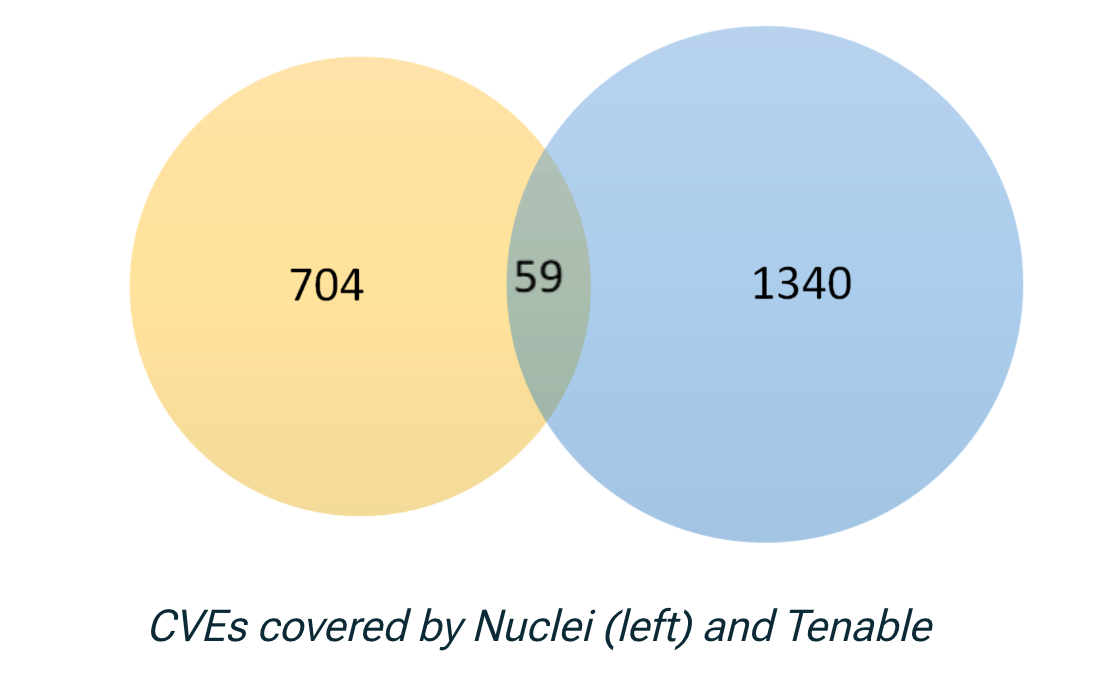
Visualize and reduce your publicity with Intruder
The dimensions of your assault floor, and the way effectively it is managed, is carefully tied to your threat of opportunistic attackers exploiting your methods. The much less you expose, and the extra hardened the companies you expose are, the more durable it’s for an attacker to take advantage of a weak spot.
You possibly can scale back your assault floor by constantly monitoring for adjustments with an automatic vulnerability administration instrument like Intruder.
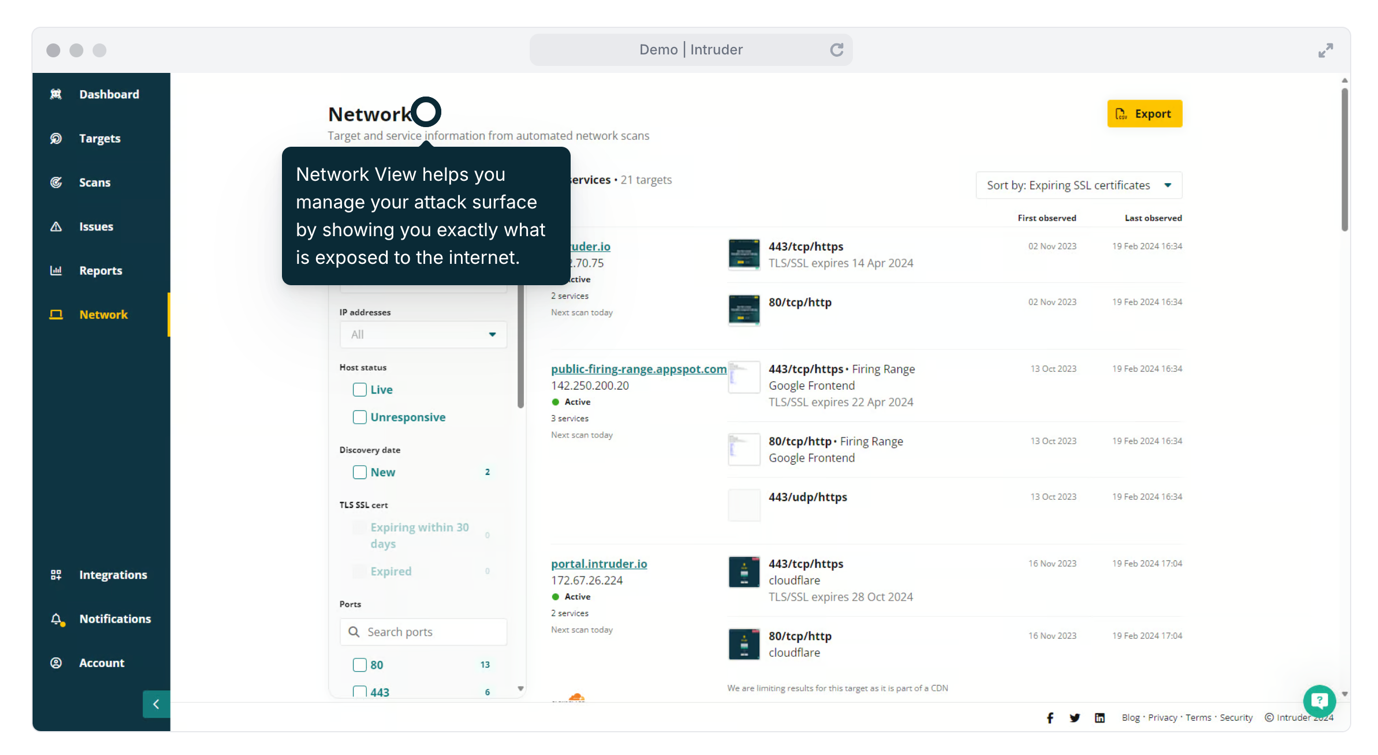 |
| A screenshot of Intruder’s assault floor administration dashboard. |
Intruder’s platform permits you to:
- Uncover belongings: when new cloud companies are spun up and uncovered to the web, Intruder kicks off a scan to search out any vulnerabilities so you may repair them sooner.
- Know what’s uncovered: get full visibility of your community perimeter, monitor lively and unresponsive targets, determine adjustments, monitor expiring certificates, and see any ports, companies or protocols that should not be uncovered to the web.
- Detect extra: Intruder makes use of a number of scanners to determine vulnerabilities and exposures throughout your assault floor providing you with the best visibility.
- Deal with the large points: see outcomes prioritized primarily based on context, so you may concentrate on essentially the most urgent issues with out losing time sifting by way of the noise.




