VMware launched security updates to repair essential sandbox escape vulnerabilities in VMware ESXi, Workstation, Fusion, and Cloud Basis merchandise, permitting attackers to flee digital machines and entry the host working system.
These kind of flaws are essential as they may allow attackers to achieve unauthorized entry to the host system the place a hypervisor is put in or entry different digital machines operating on the identical host, breaching their isolation.
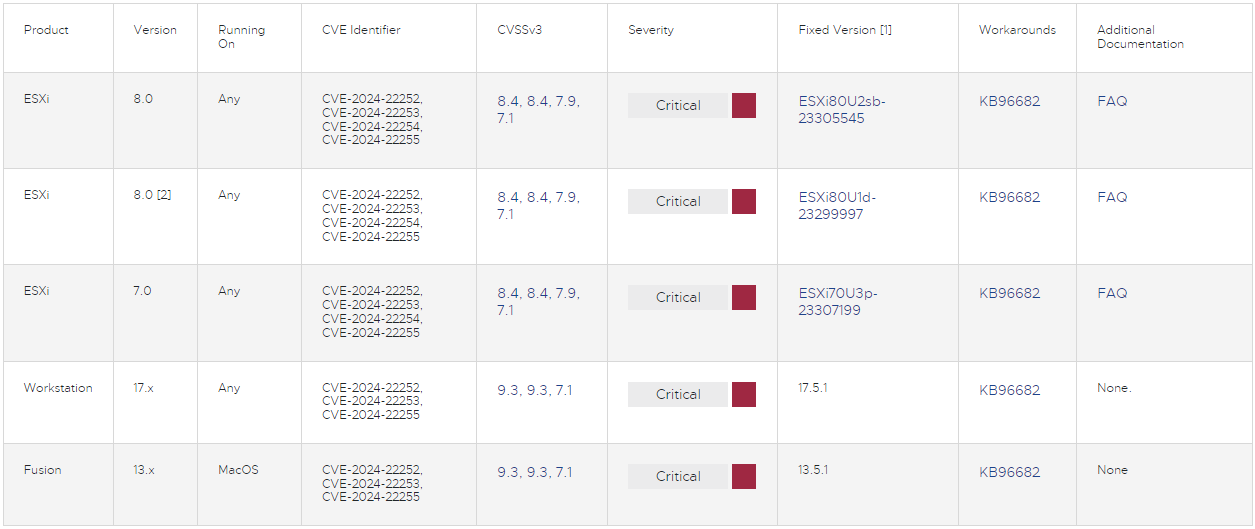
The advisory outlines 4 vulnerabilities, tracked as CVE-2024-22252, CVE-2024-22253, CVE-2024-22254, and CVE-2024-22255, with CVSS v3 scores starting from 7.1 to 9.3, however all with a essential severity score.
The 4 flaws will be summarized as follows:
- CVE-2024-22252 and CVE-2024-22253: Use-after free bugs within the XHCI and UHCI USB controllers (respectively), impacting Workstation/Fusion and ESXi. Exploitation requires native administrative privileges on a digital machine and will enable an attacker to execute code because the VM’s VMX course of on the host. On Workstation and Fusion, this might result in code execution on the host machine.
- CVE-2024-22254: Out-of-bounds write flaw in ESXi, permitting an attacker with VMX course of privileges to put in writing exterior the pre-determined reminiscence area (bounds), probably resulting in sandbox escape.
- CVE-2024-22255: Data disclosure drawback within the UHCI USB controller impacting ESXi, Workstation, and Fusion. This vulnerability might enable a malicious actor with administrative entry to a VM to leak reminiscence from the VMX course of.
Impacted model merchandise and glued variations are listed within the desk under:
A sensible workaround to mitigate CVE-2024-22252, CVE-2024-22253, and CVE-2024-22255 is to take away USB controllers from digital machines following the directions supplied by the seller. Observe that this will likely influence keyboard, mouse, and USB stick connectivity in some configurations.
It’s price noting that VMware has made security fixes obtainable for older ESXi variations (6.7U3u), 6.5 (6.5U3v), and VCF 3.x because of the vulnerabilities’ severity.
Lastly, the seller printed a FAQ to accompany the bulletin, emphasizing the significance of immediate patching and offering steerage on response planning and workaround/repair implementation for particular merchandise and configurations.
VMware has neither noticed nor obtained any studies indicating lively exploitation of the 4 flaws. System admins are beneficial to subscribe to the VMSA mailing listing for proactive alerts in case the exploitation standing modifications.




