A brand new vulnerability disclosed in GitHub might have uncovered 1000’s of repositories liable to repojacking assaults, new findings present.
The flaw “might enable an attacker to take advantage of a race situation inside GitHub’s repository creation and username renaming operations,” Checkmarx security researcher Elad Rapoport mentioned in a technical report shared with The Hacker Information.
“Profitable exploitation of this vulnerability impacts the open-source group by enabling the hijacking of over 4,000 code packages in languages equivalent to Go, PHP, and Swift, in addition to GitHub actions.”
Following accountable disclosure on March 1, 2023, the Microsoft-owned code internet hosting platform has addressed the problem as of September 1, 2023.
Repojacking, brief for repository hijacking, is a way the place a menace actor is ready to bypass a security mechanism known as common repository namespace retirement and in the end management of a repository.
What the safety measure does is stop different customers from making a repository with the identical title as a repository with greater than 100 clones on the time its consumer account is renamed. In different phrases, the mix of the username and the repository title is taken into account “retired.”
Ought to this safeguard be trivially circumvented, it might allow menace actors to create new accounts with the identical username and add malicious repositories, probably resulting in software program provide chain assaults.
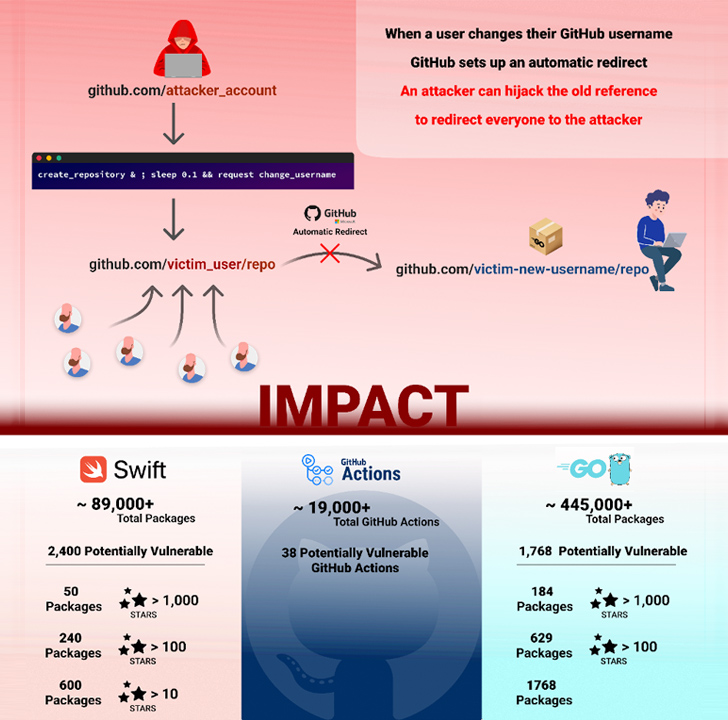
The brand new technique outlined by Checkmarx takes benefit of a possible race situation between the creation of a repository and the renaming of a username to attain repojacking. Particularly, it entails the next steps –
- Sufferer owns the namespace “victim_user/repo”
- Sufferer renames “victim_user” to “renamed_user”
- The “victim_user/repo” repository is now retired
- A menace actor with the username “attacker_user” concurrently creates a repository known as “repo” and renames the username “attacker_user” to “victim_user”
The final step is completed utilizing an API request for repository creation and a renamed request interception for the username change. The event comes practically 9 months after GitHub patched the same bypass flaw that might open the door to repojacking assaults.
“The invention of this novel vulnerability in GitHub’s repository creation and username renaming operations underlines the persistent dangers related to the ‘common repository namespace retirement’ mechanism,” Rapoport mentioned.




