Censys warns that over 1.5 million Exim mail switch agent (MTA) cases are unpatched towards a vital vulnerability that lets menace actors bypass security filters.
Tracked as CVE-2024-39929 and patched by Exim builders on Wednesday, the security flaw impacts Exim releases as much as and together with model 4.97.1.
The vulnerability is as a result of incorrect parsing of multiline RFC2231 header filenames, which may let distant attackers ship malicious executable attachments into finish customers’ mailboxes by circumventing the $mime_filename extension-blocking safety mechanism.
“If a consumer had been to obtain or run one among these malicious recordsdata, the system could possibly be compromised,” Censys warned, including that “a PoC is out there, however no energetic exploitation is thought but.”
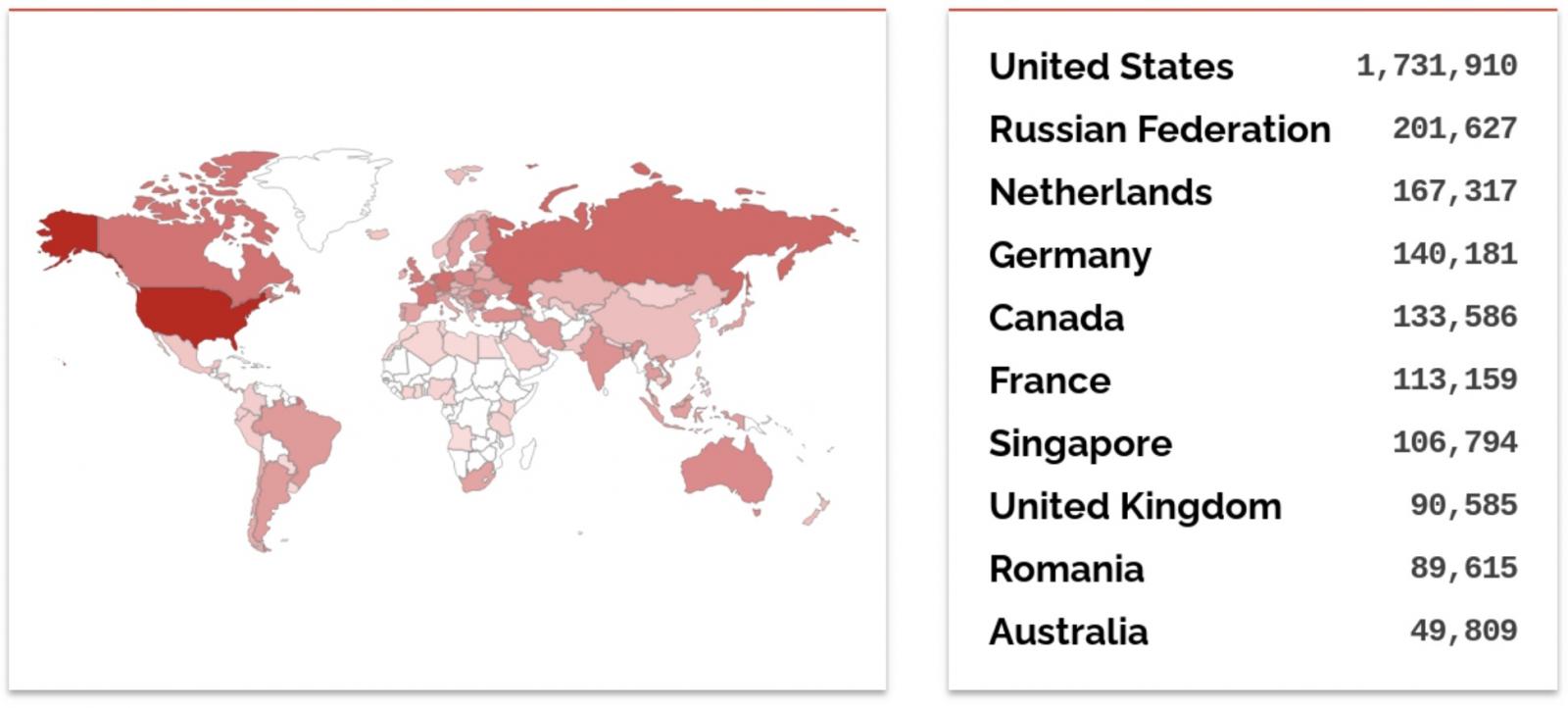
“As of July 10, 2024, Censys observes 1,567,109 publicly uncovered Exim servers operating a doubtlessly susceptible model (4.97.1 or earlier), concentrated largely in the USA, Russia, and Canada,” the corporate added.
Whereas e mail recipients will nonetheless must launch the malicious attachment to be affected, the flaw permits menace actors to bypass security checks based mostly on file extensions. This enables them to ship dangerous recordsdata which might be usually blocked, corresponding to executables, into their targets’ mailboxes.
Admins who can’t instantly improve Exim are suggested to limit distant entry to their servers from the Web to dam incoming exploitation makes an attempt.
Hundreds of thousands of servers uncovered on-line
MTA servers, corresponding to Exim, are sometimes focused in assaults as a result of they’re nearly all the time accessible through the Web, making them straightforward to search out potential entry factors right into a goal’s community.
Exim can be the default Debian Linux MTA and is the world’s hottest MTA software program, based mostly on a mail server survey from earlier this month.
In line with the survey, over 59% of the 409,255 mail servers reachable on the Web throughout the survey had been operating Exim, representing simply over 241,000 Exim cases.
Additionally, per a Shodan search, over 3.3 million Exim servers are presently uncovered on-line, most in the USA, adopted by Russia and the Netherlands. Censys discovered 6,540,044 public-facing mail servers on-line, 4,830,719 (roughly 74%) operating Exim.
The Nationwide Safety Company (NSA) revealed in Could 2020 that the infamous Russian navy hacking group Sandworm has been exploiting a vital CVE-2019-10149 Exim flaw (dubbed The Return of the WIZard) since at the very least August 2019.
Extra just lately, in October, the Exim devs patched three zero-days disclosed via Pattern Micro’s Zero Day Initiative (ZDI), one among them (CVE-2023-42115) exposing thousands and thousands of Web-exposed Exim servers to pre-auth RCE assaults.





