Verify Level has launched hotfixes for a VPN zero-day vulnerability exploited in assaults to achieve distant entry to firewalls and try and breach company networks.
On Monday, the corporate first warned a few spike in assaults concentrating on VPN units, sharing suggestions on how admins can shield their units. Later, it found the supply of the issue, a zero-day flaw that hackers exploited towards its clients.
Tracked as CVE-2024-24919, the high-severity data disclosure vulnerability allows attackers to learn sure data on internet-exposed Verify Level Safety Gateways with distant Entry VPN or Cell Entry Software program Blades enabled.
“The vulnerability probably permits an attacker to learn sure data on Web-connected Gateways with distant entry VPN or cell entry enabled,” reads an replace on Verify Level’s earlier advisory.
“The makes an attempt we have seen to date, as beforehand alerted on Could 27, concentrate on distant entry situations with previous native accounts with unrecommended password-only authentication.”
CVE-2024-24929 impacts CloudGuard Community, Quantum Maestro, Quantum Scalable Chassis, Quantum Safety Gateways, and Quantum Spark Home equipment, within the product variations: R80.20.x, R80.20SP (EOL), R80.40 (EOL), R81, R81.10, R81.10.x, and R81.20.
Verify Level has launched the next security updates to deal with the flaw:
- Quantum Safety Gateway and CloudGuard Community Safety: R81.20, R81.10, R81, R80.40
- Quantum Maestro and Quantum Scalable Chassis: R81.20, R81.10, R80.40, R80.30SP, R80.20SP
- Quantum Spark Gateways: R81.10.x, R80.20.x, R77.20.x
To use the replace, head to the Safety Gateway portal > Software program Updates > Out there Updates > Hotfix Updates, and click on ‘Set up.’
The seller says the method ought to take roughly 10 minutes, and a reboot is required.
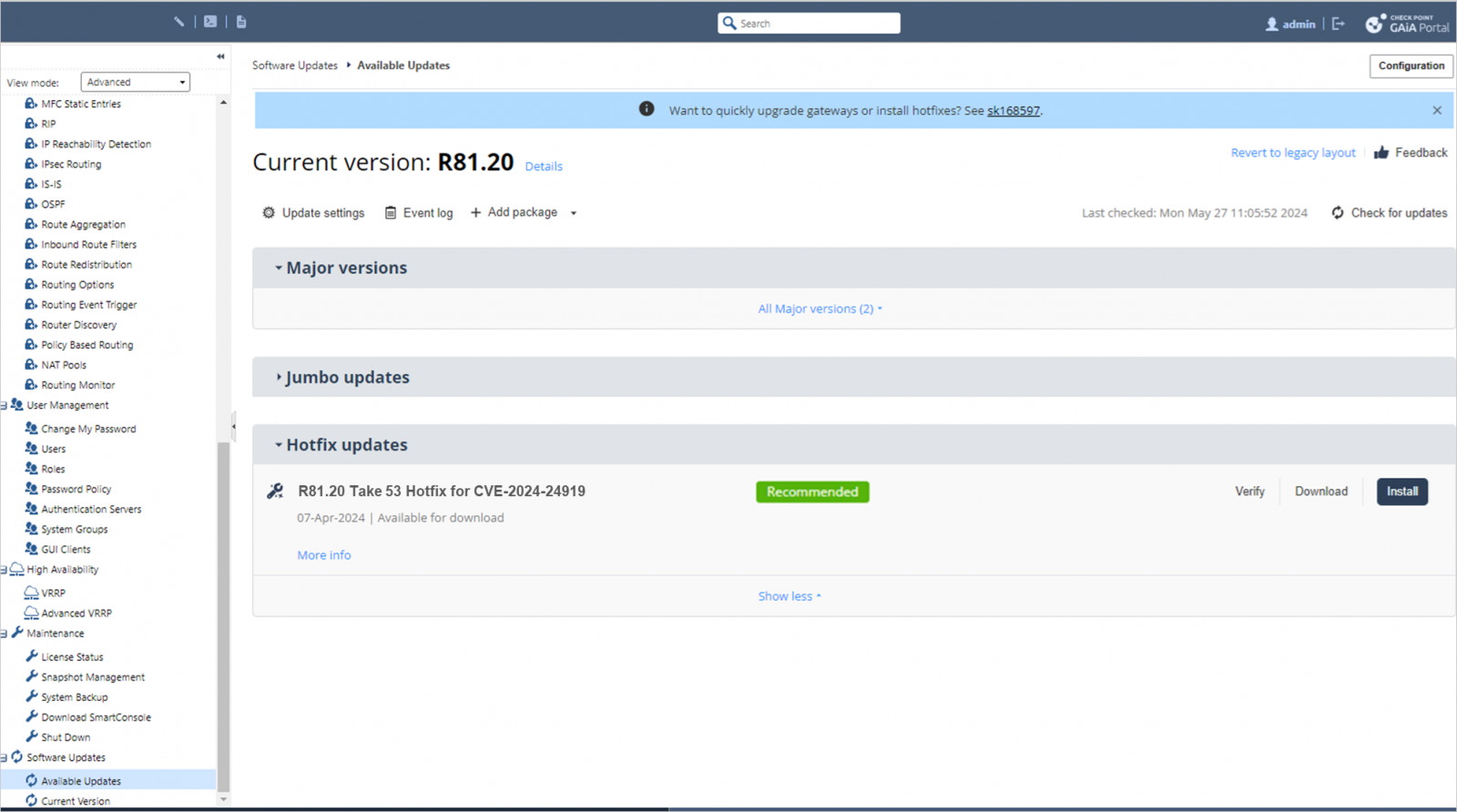
Supply: Verify Level
After the hotfix is put in, login makes an attempt utilizing weak credentials and authentication strategies can be mechanically blocked, and a log can be created.
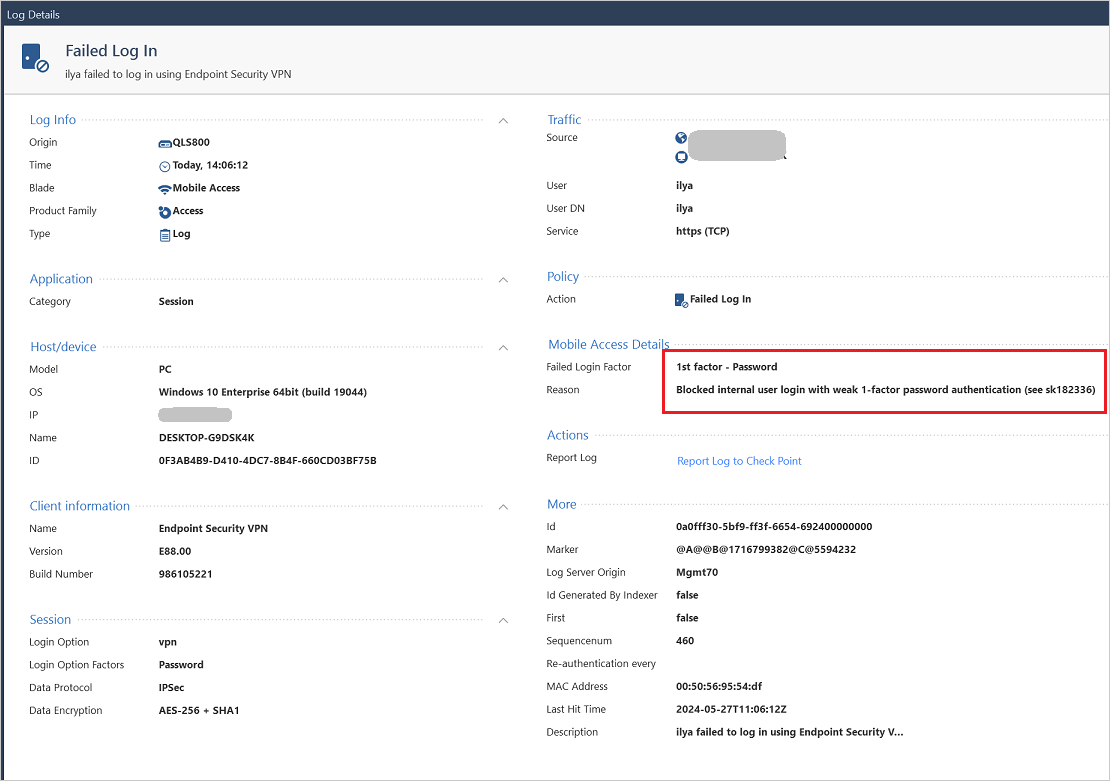
Supply: Verify Level
Hotfixes have been made accessible for end-of-life (EOL) variations, too, however they have to be downloaded and utilized manually.
Verify Level created a FAQ web page with extra details about CVE-2024-24919, IPS signature, and handbook hotfix set up directions.
These unable to use the replace are suggested to reinforce their security stance by updating the Energetic Listing (AD) password that the Safety Gateway makes use of for authentication.
Moreover, Verify Level has created a distant entry validation script that may be uploaded onto ‘SmartConsole’ and executed to evaluation the outcomes and take applicable actions.
Extra data on updating the AD password and utilizing the ‘VPNcheck.sh’ script can be found on Verify Level’s security bulletin.




