The variety of Cisco units hacked by way of the exploitation of an unpatched IOS XE vulnerability has reached roughly 40,000, in response to a number of cybersecurity corporations.
The exploited vulnerability is CVE-2023-20198, a crucial flaw affecting the IOS XE net interface that may be exploited by distant, unauthenticated attackers for privilege escalation.
Cisco has but to launch patches and the corporate warned that the vulnerability has been exploited as a zero-day since at the least mid-September.
CVE-2023-20198 permits risk actors to create high-privileged accounts on focused units and take full management of the system. In some circumstances, attackers have been noticed delivering an implant that allows them to execute arbitrary instructions.
Cisco mentioned in some circumstances the implants have been delivered through an older flaw tracked as CVE-2021-1435, however a beforehand unknown vulnerability could have additionally been exploited as a result of the implant was additionally noticed on methods patched towards CVE-2021-1435.
Vulnerability intelligence firm VulnCheck performed an web scan shortly after the zero-day’s existence got here to mild and located 10,000 compromised switches and routers, however famous that the quantity would doubtless improve as its scanning had been ongoing.
Whereas VulnCheck has but to supply an replace, a scan performed by the web search engine Censys on October 17 confirmed 67,000 internet-exposed IOS XE net interfaces, together with greater than 34,000 hosts that appeared to have been backdoored. One other scan performed by Censys the following day confirmed that the variety of hacked methods elevated to just about 42,000.
A majority of the compromised Cisco units seem like in the US, adopted by the Philippines and Latin America. India, Thailand, Singapore and Australia even have a major variety of infections.
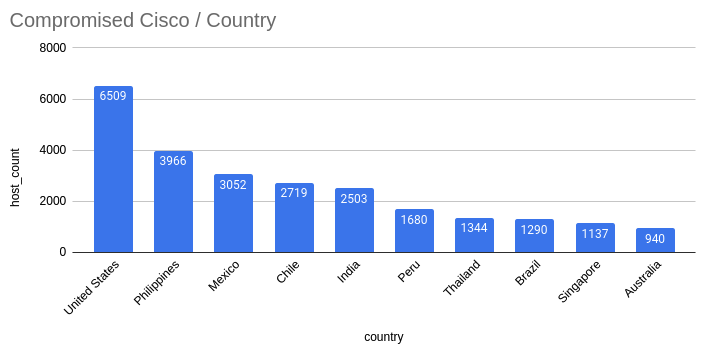
LeakIX, which scans the web for weak methods, initially reported seeing the malicious implant on roughly 30,000 Cisco units, however its newest scan detected a further 10,000 compromised methods.
Risk intelligence firm GreyNoise has been utilizing its honeypots to trace assault makes an attempt and as of October 19 it has seen assaults originating from 230 distinctive IP addresses.




