Two U.Okay. youngsters have been convicted by a jury in London for being a part of the infamous LAPSUS$ (aka Slippy Spider) transnational gang and for orchestrating a sequence of brazen, high-profile hacks in opposition to main tech companies and demanding a ransom in alternate for not leaking the stolen info.
This contains Arion Kurtaj (aka White, Breachbase, WhiteDoxbin, and TeaPotUberHacker), an 18-year-old from Oxford, and an unnamed minor, who started collaborating in July 2021 after having met on-line, BBC reported this week.
Each the defendants have been initially arrested and launched below investigation in January 2022, solely to be re-arrested and charged by the Metropolis of London Police in April 2022. Kurtaj was subsequently granted bail and moved to a resort in Bicester after he was doxxed in a web based cybercrime discussion board.
He, nonetheless, continued his hacking spree, concentrating on corporations like Uber, Revolut, and Rockstar Video games, on account of which he was arrested once more in September. One other alleged member of the group was apprehended by Brazilian authorities in October 2022.
Central to pulling off the extortion schemes was their potential to conduct SIM swapping and immediate bombing assaults to realize unauthorized entry to company networks after an intensive social engineering section.
The financially motivated operation additionally entailed posting messages to their Telegram channel to solicit rogue insiders who can present Digital Personal Community (VPN), Digital Desktop Infrastructure (VDI), or Citrix credentials to organizations.
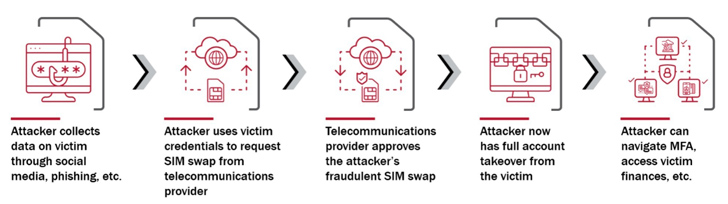
A latest report from the U.S. authorities discovered that the actors provided as a lot as $20,000 per week for entry to telecommunications suppliers in order to hold out the SIM swap assaults. It characterised LAPSUS$ as distinctive for its “effectiveness, pace, creativity, and boldness,” and for weaponizing a “playbook of efficient methods.”
“To execute fraudulent SIM swaps, LAPSUS$ obtained primary details about its victims, resembling their identify, telephone quantity, and buyer proprietary community info (CPNI),” the Division of Homeland Safety’s (DHS) Cyber Security Evaluate Board (CSRB) mentioned.
“LAPSUS$ realized the data by quite a lot of methods, together with issuing fraudulent [Emergency Disclosure Requests], and utilizing account takeover methods, to hijack the accounts of telecommunications supplier staff and contractors.”
“It then carried out fraudulent SIM swaps by way of the telecommunications supplier’s buyer administration instruments. After executing the fraudulent SIM swaps, LAPSUS$ took over on-line accounts by way of sign-in and account restoration workflows that despatched one-time hyperlinks or MFA passcodes by way of SMS or voice calls.”
Different strategies of preliminary entry ranged from using the providers of preliminary entry brokers (IABs) to the exploitation of security flaws, following which the actors took steps to escalate privileges, laterally transfer throughout the community, arrange persistent entry by way of distant desktop software program resembling AnyDesk and TeamViewer, and disable security monitoring instruments.
Among the many companies infiltrated by LAPSUS$ comprised BT, EE, Globant, LG, Microsoft, NVIDIA, Okta, Samsung, Ubisoft, and Vodafone. It is at the moment unclear whether or not ransoms have been paid by any of the breached corporations. The youngsters are anticipated to be sentenced at a later date.
“The group gained notoriety as a result of it efficiently attacked well-defended organizations utilizing extremely efficient social engineering; focused provide chains by compromising enterprise course of outsourcing (BPOs) and telecommunications suppliers; and used its public Telegram channel to debate its operations, targets, and successes, and even to speak with and extort its targets,” the CSRB mentioned.




