Two China-linked superior persistent menace (APT) teams have been noticed focusing on entities and member international locations affiliated with the Affiliation of Southeast Asian Nations (ASEAN) as a part of a cyber espionage marketing campaign over the previous three months.
This contains the menace actor generally known as Mustang Panda, which has been lately linked to cyber assaults in opposition to Myanmar in addition to different Asian international locations with a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
Mustang Panda, additionally known as Camaro Dragon, Earth Preta, and Stately Taurus, is believed to have focused entities in Myanmar, the Philippines, Japan and Singapore, focusing on them with phishing emails designed to ship two malware packages.
“Risk actors created malware for these packages on March 4-5, 2024, coinciding with the ASEAN-Australia Particular Summit (March 4-6, 2024),” Palo Alto Networks Unit 42 mentioned in a report shared with The Hacker Information.
One of many malware bundle is a ZIP file that incorporates inside it an executable (“Talking_Points_for_China.exe”), that when launched, masses a DLL file (“KeyScramblerIE.dll”) and in the end deploys a recognized Mustang Panda malware known as PUBLOAD, a downloader beforehand employed to drop PlugX.
It is value stating right here that the binary is a renamed copy of a reputable software program known as KeyScrambler.exe that is prone to DLL side-loading.
The second bundle, alternatively, is a screensaver executable (“Word PSO.scr”) that is used to retrieve next-stage malicious code from a distant IP tackle, together with a benign program signed by a online game firm renamed as WindowsUpdate.exe and a rogue DLL that is launched utilizing the identical method as earlier than.

“This malware then makes an attempt to determine a connection to www[.]openservername[.]com at 146.70.149[.]36 for command-and-control (C2),” the researchers mentioned.
Unit 42 mentioned it additionally detected community site visitors between an ASEAN-affiliated entity and the C2 infrastructure of a second Chinese language APT group, suggesting a breach of the sufferer’s surroundings. This unnamed menace exercise cluster has been attributed to comparable assaults focusing on Cambodia.
“A lot of these campaigns proceed to show how organizations are focused for cyber espionage functions, the place nation-state affiliated menace teams accumulate intelligence of geopolitical pursuits inside the area,” the researchers mentioned.
Earth Krahang Emerges in Wild
The findings arrive every week after Development Micro make clear a brand new Chinese language menace actor generally known as Earth Krahang that has focused 116 entities spanning 35 international locations by leveraging spear-phishing and flaws in public-facing Openfire and Oracle servers to ship bespoke malware corresponding to PlugX, ShadowPad, ReShell, and DinodasRAT (aka XDealer).
The earliest assaults date again to early 2022, with the adversary leveraging a mixture of strategies to scan for delicate information.
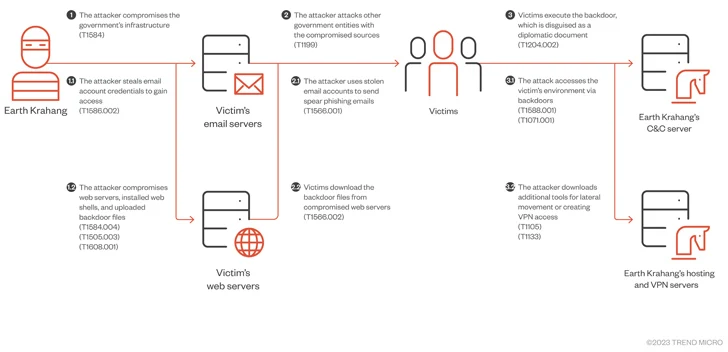
Earth Krahang, which has a powerful focus in Southeast Asia, additionally displays some stage of overlap with one other China-nexus menace actor tracked as Earth Lusca (aka RedHotel). Each the intrusion units are doubtless managed by the identical menace actor and linked to a Chinese language authorities contractor known as I-Quickly.
“One of many menace actor’s favourite ways includes utilizing its malicious entry to authorities infrastructure to assault different authorities entities, abusing the infrastructure to host malicious payloads, proxy assault site visitors, and ship spear-phishing emails to government-related targets utilizing compromised authorities e-mail accounts,” the corporate mentioned.
“Earth Krahang additionally makes use of different ways, corresponding to constructing VPN servers on compromised public-facing servers to determine entry into the personal community of victims and performing brute-force assaults to acquire e-mail credentials. These credentials are then used to exfiltrate sufferer emails.”
The I-Quickly Leaks and the Shadowy Hack-for-hire Scene
Final month, a set of leaked paperwork from I-Quickly (aka Anxun) on GitHub revealed how the corporate sells a big selection of stealers and distant entry trojans like ShadowPad and Winnti (aka TreadStone) to a number of Chinese language authorities entities. This additionally encompasses an built-in operations platform that is designed to hold out offensive cyber campaigns and an undocumented Linux implant codenamed Hector.
“The built-in operations platform encompasses each inner and exterior purposes and networks,” Bishop Fox mentioned. “The inner utility is especially for mission and useful resource administration. The exterior utility is designed to hold out cyber operations.”
The obscure hack-for-hire entity has additionally been implicated within the 2019 POISON CARP marketing campaign aimed toward Tibetan teams and the 2022 hack of Comm100, along with assaults focusing on overseas governments and home ethnic minorities to achieve useful info, a few of that are carried out independently on their very own in hopes of touchdown a authorities buyer.
“The info leak has supplied uncommon perception into how the Chinese language authorities outsources elements of its cyber operations to personal third-party firms, and the way these firms work with each other to satisfy these calls for,” ReliaQuest famous.

Cybersecurity agency Recorded Future, in its personal evaluation, mentioned the leak unravels the “operational and organizational ties” between the corporate and three totally different Chinese language state-sponsored cyber teams corresponding to RedAlpha (aka Deepcliff), RedHotel, and POISON CARP.
“It offers supporting proof relating to the long-suspected presence of ‘digital quartermasters’ that present capabilities to a number of Chinese language state-sponsored teams.”
It additionally mentioned the overlaps recommend the presence of a number of sub-teams targeted on explicit missions inside the similar firm. I-Quickly’s victimology footprint spreads to at the very least 22 international locations, with authorities, telecommunications, and training representing probably the most focused sectors.
Moreover, the publicized paperwork verify that Tianfu Cup – China’s personal tackle the Pwn2Own hacking contest – acts as a “vulnerability feeder system” for the federal government, permitting it to stockpile zero-day exploits and devise exploit code.
“When the Tianfu Cup submissions aren’t already full exploit chains, the Ministry of Public Safety disseminates the proof of idea vulnerabilities to personal companies to additional exploit these proof-of-concept capabilities,” Margin Analysis mentioned.
“China’s vulnerability disclosure requirement is one a part of the puzzle of how China stockpiles and weaponizes vulnerabilities, setting in stone the surreptitious assortment provided by Tianfu Cup in earlier years.”
The supply of the leak is at present not recognized, though two staff of I-Quickly advised The Related Press that an investigation is ongoing in collaboration with regulation enforcement. The corporate’s web site has since gone offline.
“The leak offers a few of the most concrete particulars seen publicly thus far, revealing the maturing nature of China’s cyber espionage ecosystem,” SentinelOne’s Dakota Cary and Aleksandar Milenkoski mentioned. “It exhibits explicitly how authorities focusing on necessities drive a aggressive market of impartial contractor hackers-for-hire.”




