The TP-Hyperlink Archer C5400X gaming router is weak to security flaws that might allow an unauthenticated, distant attacker to execute instructions on the machine.
The TP-Hyperlink Archer C5400X is a high-end tri-band gaming router designed to offer strong efficiency and superior options for gaming and different demanding purposes, and primarily based on the variety of person evaluations the product has on on-line shops, it seems to be a well-liked alternative amongst avid gamers.
Arbitrary command execution on routers can result in hijacking routers, knowledge interception, altering DNS settings, and doubtlessly breaching inner networks.
Vulnerability particulars
The flaw on the TP-Hyperlink Archer C5400X is tracked as CVE-2024-5035 (CVSS v4 rating: 10.0, “vital”) and was recognized by analysts at OneKey by binary static evaluation.
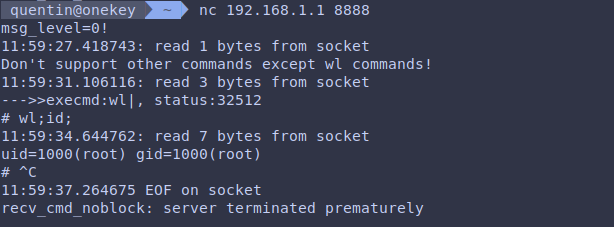
The researchers discovered that the ‘rftest’ binary exposes a community service weak to command injection and buffer overflows on TCP ports 8888, 8889, and 8890.
The ‘rftest’ service runs a community listener on these ports to carry out wi-fi interface self-assessment and associated duties.
An attacker utilizing shell metacharacters can ship specifically crafted messages to those ports, doubtlessly attaining arbitrary command execution with elevated privileges.
Shell metacharacters are particular characters like semicolons, ampersands, and pipes that are used for higher perform management on command-line shells. Nonetheless, they can be abused for command execution when the person enter isn’t correctly sanitized to stop unauthorized actions.
Supply: OneKey
Repair obtainable
Because the talked about ports are open and actively utilized by the ‘rftest’ service on the router’s default configuration, they affect all customers of the machine utilizing the weak firmware variations, by 1.1.1.6.
OneKey analysts reported their findings to TP-Hyperlink’s PSIRT on February 16, 2024, whereas the seller had a beta patch prepared by April 10, 2024.
Lastly, the security replace got here late final week, on Could 24, 2024, with the discharge of Archer C5400X(EU)_V1_1.1.7 Construct 20240510, which successfully addresses CVE-2024-5035.
The applied repair was to discard any instructions containing shell metacharacters, so these are filtered out in all incoming messages.
Customers are really useful to obtain the firmware replace from TP-Hyperlink’s official obtain portal or use their router admin panel to carry out the replace.




