A essential zero-day vulnerability in all variations of Exim mail switch agent (MTA) software program can let unauthenticated attackers achieve distant code execution (RCE) on Web-exposed servers.
Discovered by an nameless security researcher and disclosed via Development Micro’s Zero Day Initiative (ZDI), the security bug (CVE-2023-42115) is because of an Out-of-bounds Write weak spot discovered within the SMTP service.
Whereas the sort of challenge can result in software program crashes or corruption of information following profitable exploitation, it will also be abused by attackers for code or command execution on weak servers.
“The particular flaw exists inside the smtp service, which listens on TCP port 25 by default,” a ZDI security advisory printed on Wednesday explains.
“The difficulty outcomes from the shortage of correct validation of user-supplied knowledge, which may end up in a write previous the tip of a buffer. An attacker can leverage this vulnerability to execute code within the context of the service account.”
Whereas ZDI reported the vulnerability to the Exim workforce in June 2022 and resent information on the flaw on the vendor’s request in Could 2023, the builders failed to supply an replace on their patch progress.
Because of this, ZDI printed an advisory on September 27, with particulars on the CVE-2023-42115 zero-day and a full timeline of all exchanges with the Exim workforce.
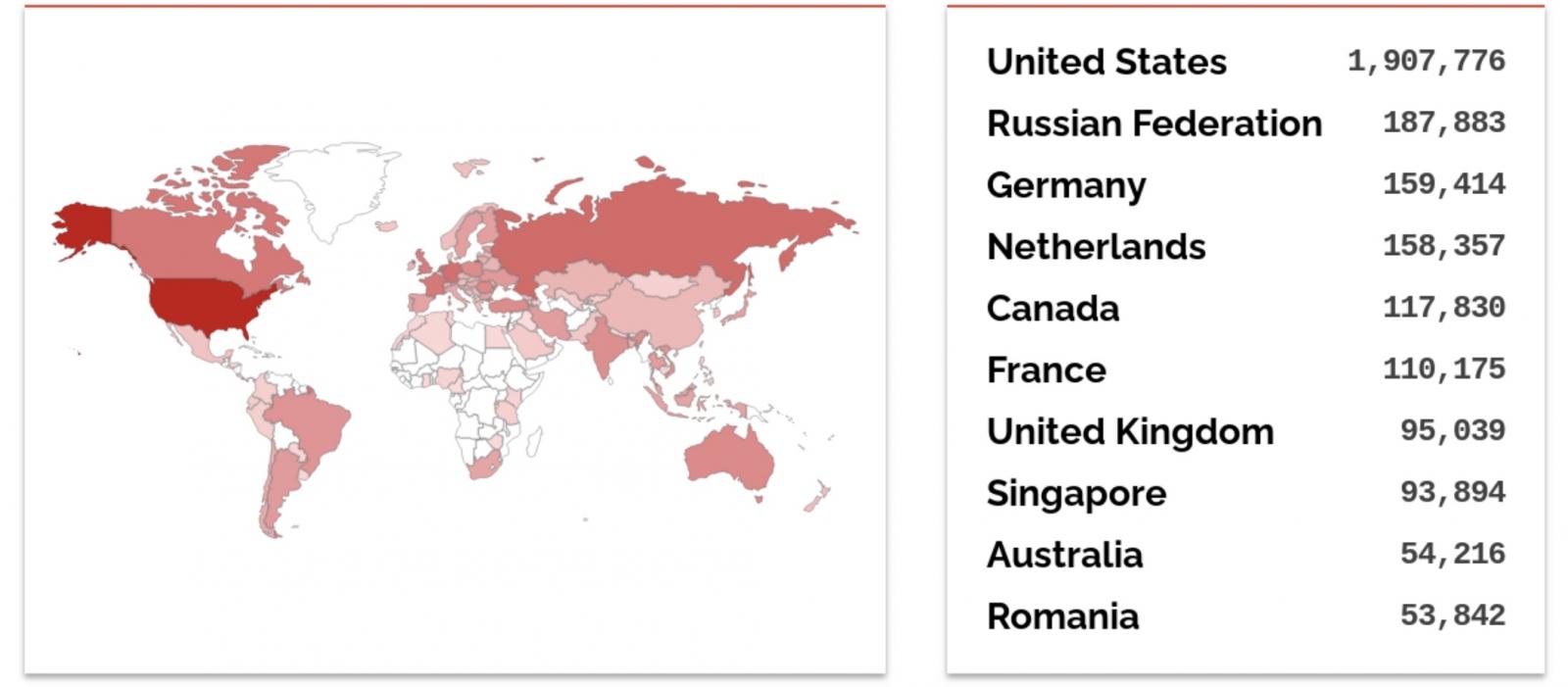
Thousands and thousands of servers uncovered to assaults
MTA servers like Exim are extremely weak targets, primarily as a result of they’re usually accessible through the Web, serving as simple entry factors for attackers right into a goal’s community.
The Nationwide Safety Company (NSA) mentioned three years in the past, in Could 2020, that the infamous Russian army hacking group Sandworm has been exploiting the essential CVE-2019-10149 (The Return of the WIZard) Exim flaw since not less than August 2019.
Exim can be the default MTA on Debian Linux distros and the world’s hottest MTA software program, in keeping with a mail server survey from September 2023.
Based on the survey, Exim is put in on greater than 56% out of a complete of 602,000 mail servers reachable on the Web, representing simply over 342,000 Exim servers.
Simply over 3.5 million Exim servers are presently uncovered on-line per a Shodan search, most of them in the USA, adopted by Russia and Germany.
Whereas a patch is just not but obtainable to safe weak Exim servers towards potential assaults, ZDI suggested admins to limit distant entry from the Web to thwart incoming exploitation makes an attempt.
“Given the character of the vulnerability, the one salient mitigation technique is to limit interplay with the applying,” ZDI warned.




