2023 was an enormous yr for cybersecurity, with important cyberattacks, data breaches, new menace teams rising, and, after all, zero-day vulnerabilities.
Some tales, although, had been extra impactful or widespread with our 22 million readers than others.
Under are fourteen of what BleepingComputer believes are probably the most impactful cybersecurity tales of 2023, with a abstract of every.
14. The 23andMe data breach
Genetic testing supplier 23andMe suffered credential stuffing assaults that led to a serious data breach, exposing the information of 6.9 million customers.
The corporate states that the attackers solely breached a small variety of accounts in the course of the credential-stuffing assaults. Nevertheless, the menace actors had been in a position to abuse different options to scrape thousands and thousands of people’ information.
The menace actors tried to promote the stolen information, however after not receiving patrons, leaked the information for 1 million Ashkenazi Jews and 4,011,607 folks residing in Nice Britain on a hacking discussion board.
In a latest replace, 23andMe instructed BleepingComputer that the breach impacted 6.9 million folks — 5.5 million by the DNA Kinfolk characteristic and 1.4 million by the Household Tree characteristic.
This breach has led to a number of class motion lawsuits in opposition to the corporate for not adequately defending information.
13. Internet hosting agency says it misplaced all buyer information after ransomware assault
Two Danish internet hosting suppliers had been pressured to close down after a ransomware assault encrypted the vast majority of buyer information, and information restoration was not profitable.
“Since we neither can nor want to meet the monetary calls for of the felony hackers for a ransom, CloudNordic’s IT crew and exterior specialists have been working intensively to evaluate the injury and decide what could possibly be recovered,” reads CloudNordic’s assertion (machine translated)
“Sadly, it has been unattainable to recuperate extra information, and the vast majority of our prospects have consequently misplaced all their information with us.”
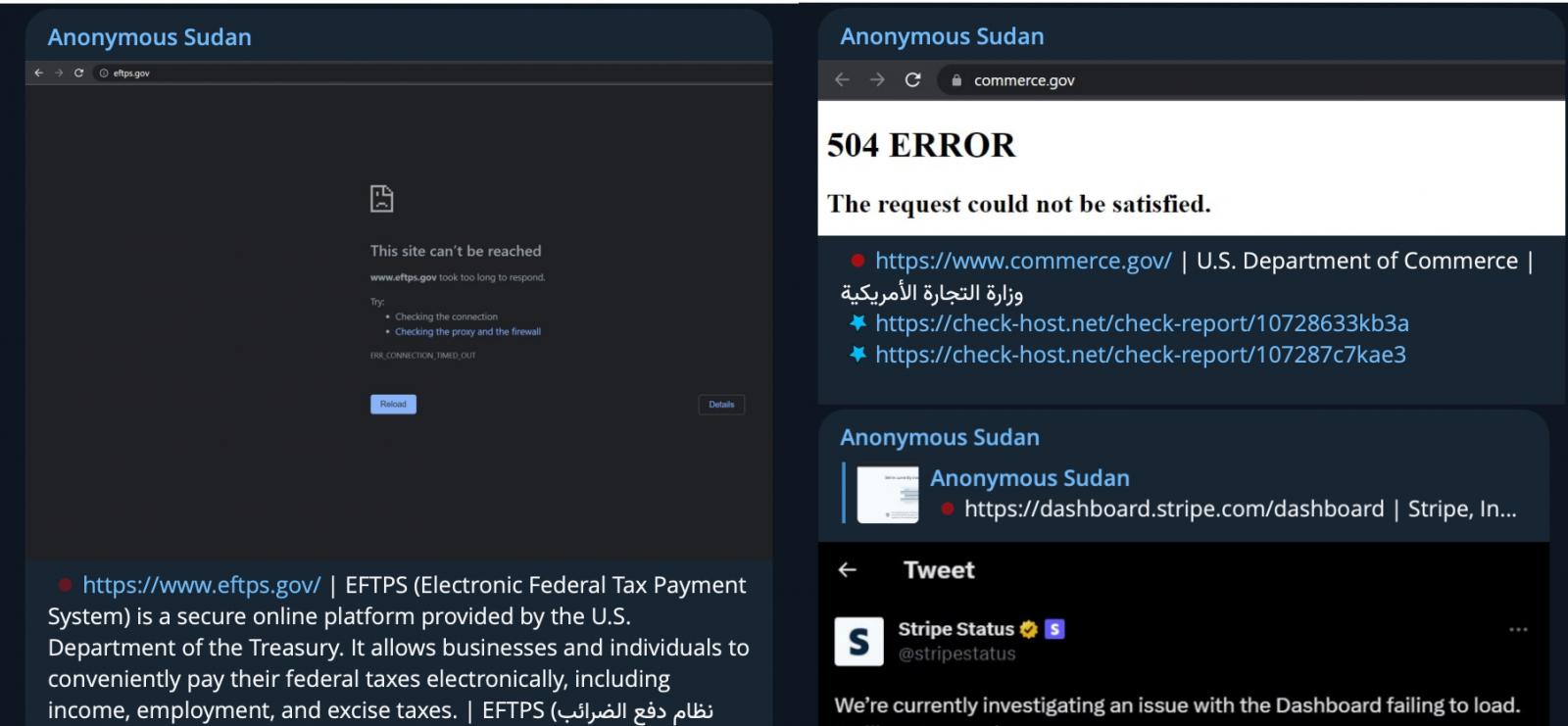
12. Nameless Sudan hacktivists present that DDoS assaults can affect the most important tech corporations
A hacktivist group often called Nameless Sudan took everybody unexpectedly when their DDoS assaults took down the web sites and providers of a number of the largest tech corporations on the planet.
The group’s assaults gained vast media consideration once they efficiently took down login pages for Microsoft’s providers, together with Outlook, OneDrive, and the Azure portal.
Over per week later, Microsoft lastly confirmed that DDoS assaults triggered these outages.
“Starting in early June 2023, Microsoft recognized surges in site visitors in opposition to some providers that briefly impacted availability,” confirmed Microsoft.
“Microsoft promptly opened an investigation and subsequently started monitoring ongoing DDoS exercise by the menace actor that Microsoft tracks as Storm-1359.”
Nameless Sudan later focused quite a few different web sites, together with these for ChatGPT, Cloudflare, and U.S. authorities providers.
Supply: BleepingComputer
The growing DDoS assaults and their affect led the U.S. Cybersecurity and Infrastructure Safety Company (CISA) to launch an advisory about these incidents.
11. New acoustic assault steals information from keystrokes with 95% accuracy
A crew of researchers from British universities skilled a deep studying mannequin to steal information from keyboard keystrokes recorded utilizing a microphone with an accuracy of 95%.
When Zoom was used for coaching the sound classification algorithm, the prediction accuracy dropped to 93%, which remains to be extraordinarily excessive.
To mitigate these assaults, the researchers counsel customers might strive altering typing kinds or utilizing randomized passwords. Different protection measures embody utilizing software program to breed keystroke sounds, play white noise, or software-based keystroke audio filters.
10. PayPal accounts breached in large-scale credential stuffing assault
PayPal suffered a credential stuffing assault between December 6 and December 8, 2022, permitting attackers to entry 34,942 accounts.
Credential stuffing is an assault the place hackers try to entry an account by attempting out username and password pairs sourced from information leaks on numerous web sites.
Hackers had entry to account holders’ full names, dates of beginning, postal addresses, social security numbers, and particular person tax identification numbers.
9. Dish Community goes offline after probably cyberattack, staff lower off
American T.V. large and satellite tv for pc broadcast supplier DISH Community mysteriously went offline earlier this yr, with its web sites and cellular apps not working for days.

Supply: BleepingComputer
DISH later confirmed that the outage was brought on by a ransomware assault, with BleepingComputer first to report that the Black Basta ransomware gang was behind the assault.
Workers instructed BleepingComputer that the ransomware gang compromised the corporate’s Home windows area controllers and encrypted VMware ESXi servers and backups.
DISH data breach notifications confirmed that information was stolen within the assault and hinted {that a} ransom was paid to not launch the stolen information.
“We’re not conscious of any misuse of your info, and we now have obtained affirmation that the extracted information has been deleted,” learn the data breach notification.
8. GoDaddy: Hackers stole supply code, put in malware in multi-year breach
Website hosting large GoDaddy says it suffered a multi-year breach permitting unknown attackers to steal supply code and set up malware on its servers.
This breach started in 2021 and allowed the menace actors entry to the private info of 1.2 million Managed WordPress prospects, together with credentials, and in addition used the entry to redirect web sites to different domains.
No menace actors ever claimed accountability for this assault.
7. MGM Resorts cyberattack shuts down IT methods after cyberattack
MGM Resorts Worldwide suffered an enormous assault that impacted quite a few methods, together with its principal web site, on-line reservations, and in-casino providers, like ATMs, slot machines, and bank card machines.
The BlackCat ransomware operation claimed the assault, whose associates mentioned they encrypted over 100 ESXi hypervisors in the course of the incident.
Bloomberg reported that the identical group additionally breached Caesars Leisure’s community, offering a powerful trace in a Kind 8-Ok SEC submitting that they paid the attackers to forestall a leak of consumers’ stolen information.
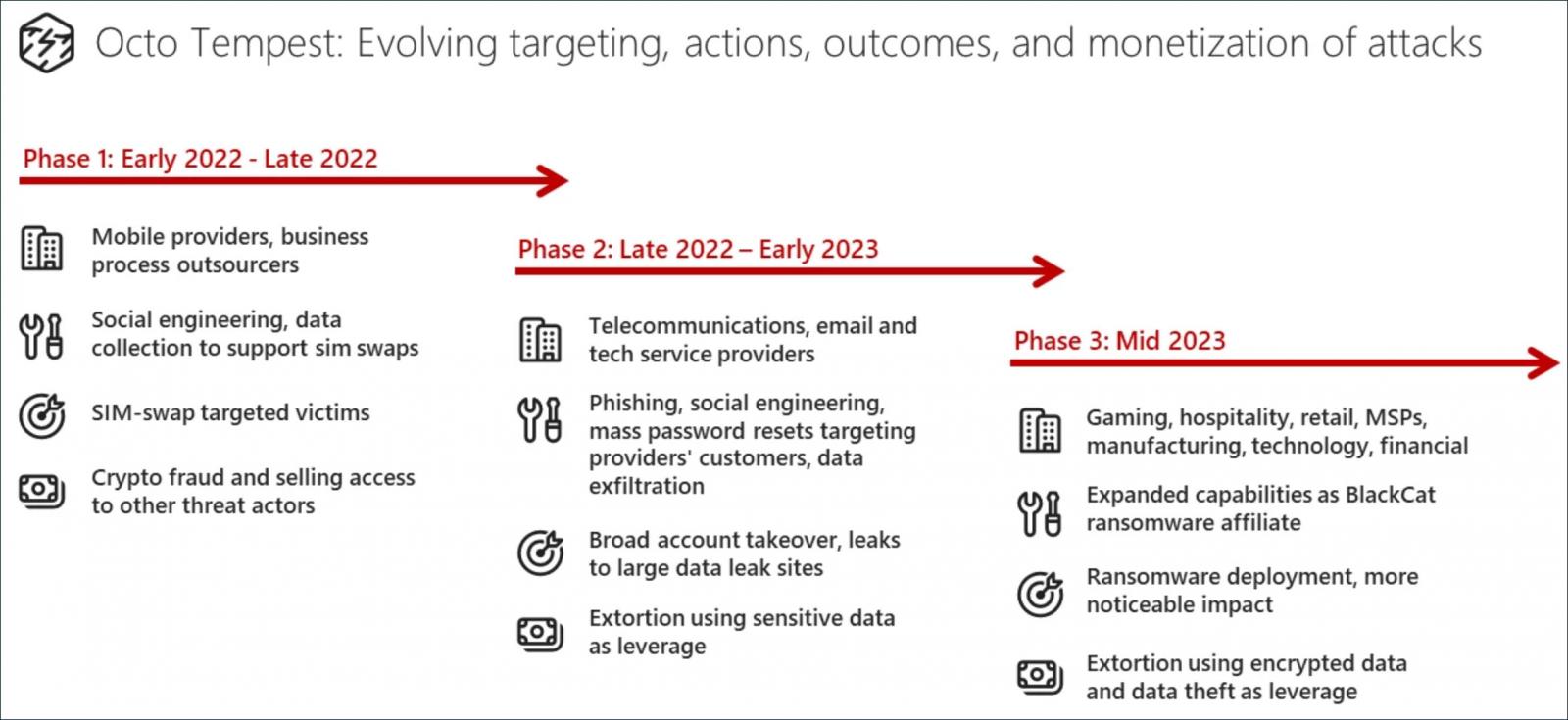
Whereas the assault was important, it additionally introduced vast consideration to a loose-knit group of hackers often called Scattered Spider.
Scattered Spider, also called 0ktapus, Starfraud, UNC3944, and Muddled Libra, is adept at social engineering and depends on phishing, multi-factor authentication (MFA) bombing (focused MFA fatigue), and SIM swapping to realize preliminary community entry on massive organizations.
Supply: Microsoft
Members of this collective are associates of the BlackCat ransomware gang and embody younger English-speaking members with numerous talent units who frequent the identical hacking boards and Telegram channels.
Whereas many consider it is a cohesive gang, the group is a community of people, with completely different menace actors collaborating in every assault. This fluid construction is what makes it difficult to trace them.
In November, the FBI launched an advisory highlighting the group’s ways, methods, and procedures (TTPs).
Scattered Spider is behind earlier assaults on Reddit, MailChimp, Twilio, DoorDash, and Riot Video games.
6. Hackers compromise 3CX desktop app in a provide chain assault
3CX was breached by the North Korean Lazarus hacking group to push malware by a provide chain assault utilizing the corporate’s Voice Over Web Protocol (VOIP) desktop consumer.
3CX is a VoIP IPBX software program growth firm whose 3CX Cellphone System is utilized by greater than 350,000 corporations worldwide and has over 12 million every day customers.
3CX was breached after an worker put in a trojanized model of Buying and selling Applied sciences’ X_TRADER software program, which allowed the menace actors to steal company credentials and breach the community.
The attackers pushed out a malicious software program replace that put in a beforehand unknown information-stealing malware to steal information and credentials saved in Chrome, Edge, Courageous, and Firefox person profiles.
5. Barracuda says hacked ESG home equipment have to be changed instantly
In Could, Barracuda disclosed that a few of their E mail Safety Gateway (ESG) home equipment had been hacked utilizing a zero-day vulnerability to put in malware and steal information.
We later realized that the assaults had been linked to Chinese language menace actors, who used the vulnerability since 2022 to contaminate ESG units with new malware named ‘Saltwater,’ ‘Seaspy,’ and ‘Seaside.’
CISA later disclosed that Submarine and Whirlpool malware had been additionally used within the assaults to backdoor ESG units.
What stood out from these assaults is that as an alternative of utilizing a software program repair for impacted ESG units, Barracuda warned prospects they should exchange their E mail Safety Gateway (ESG) home equipment, which was accomplished freed from cost.
“Impacted ESG home equipment have to be instantly changed no matter patch model degree,” the corporate warned on the time.
“Barracuda’s remediation suggestion presently is full substitute of the impacted ESG.”
This uncommon request led many to consider that the menace actors compromised the units at a low degree, making it unattainable to make sure they had been fully clear.
Mandiant, who was a part of the incident response in these assaults, instructed BleepingComputer that this was really helpful out of warning, as Barracuda couldn’t guarantee the entire elimination of malware.
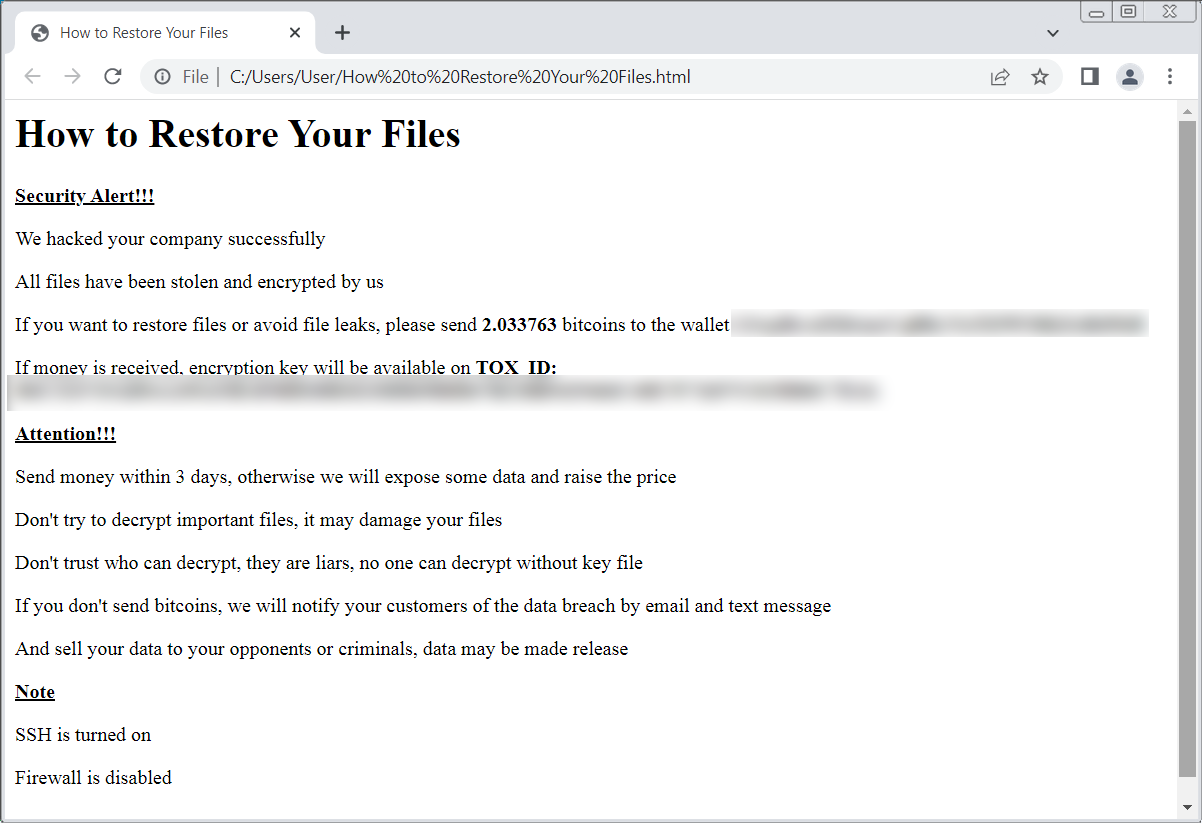
4. Huge ESXiArgs ransomware assault targets VMware ESXi servers worldwide
In February 2023, an enormous ransomware marketing campaign focused uncovered VMware ESXi servers worldwide, rapidly encrypting the digital machines for 1000’s of corporations.
Simply hours after the assault, victims started reporting within the BleepingComputer’s discussion board that recordsdata with vmxf, .vmx, .vmdk, .vmsd, and .nvram, all recordsdata related to VMware ESXi digital machines, had been encrypted.
The ransomware marketing campaign was dubbed ESXiArgs on account of an .args file being created for each encrypted file.
The VMware ESXi console house web page was modified to point out a ransom word demanding 2.0781 bitcoins, value roughly $49,000 on the time.
Supply: BleepingComputer
3. Brazil seizing Flipper Zero shipments to forestall use in crime
One in all BleepingComputer’s most-read tales of the yr was the information that the Brazilian Nationwide Telecommunications Company seized incoming Flipper Zero purchases for his or her potential for use in felony exercise.
Brazilians who bought the Flipper Zero reported that their shipments had been redirected to Brazil’s telecommunications company, Anatel, on account of an absence of certification with the nation’s Radio Frequencies division.
From emails seen by BleepingComputer, Anatel flagged the system as a device used for felony functions.
2. The Operation Triangulation iPhone assaults
In June, researchers from Kaspersky first disclosed a brand new zero-click iOS assault referred to as “Operation Triangulation” used to put in the TriangleDB spyware and adware on iPhones.
Kaspersky found the assault on units inside its personal community, and Russia’s FSB intelligence service accused Apple of offering the NSA with a backdoor. Nevertheless, the true origins of the assault stay unknown, and there’s no proof that the U.S. authorities is behind the assaults.
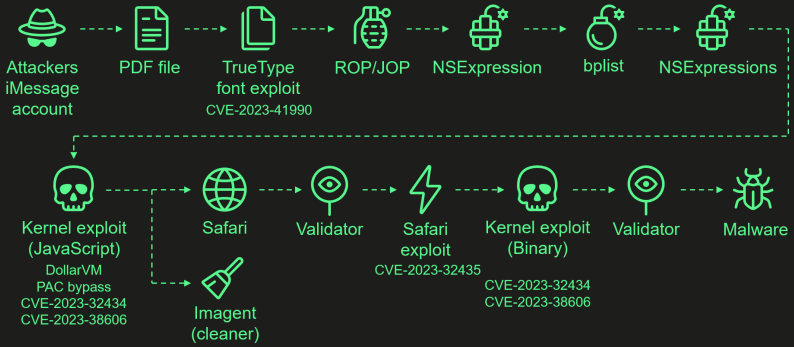
The assaults begin with the hackers sending a malicious iMessage attachment that, when processed by iOS, robotically triggers a zero-click exploit chain. A zero-click exploit means it doesn’t require interplay from the person to be triggered.
The assaults chained collectively 4 zero-day iOS vulnerabilities listed beneath to put in the spyware and adware:
- CVE-2023-41990: A vulnerability within the ADJUST TrueType font instruction permitting distant code execution by a malicious iMessage attachment.
- CVE-2023-32434: An integer overflow situation in XNU’s reminiscence mapping syscalls, granting attackers in depth learn/write entry to the system’s bodily reminiscence.
- CVE-2023-32435: Used within the Safari exploit to execute shellcode as a part of the multi-stage assault.
- CVE-2023-38606: A vulnerability utilizing {hardware} MMIO registers to bypass the Web page Safety Layer (PPL), overriding hardware-based security protections.
Final week, Kaspersky disclosed that the ultimate zero-day vulnerability, CVE-2023-38606, abused an undocumented characteristic in Apple chips to bypass hardware-based security protections.
Whereas the Operation Triangulation assaults didn’t affect many units, it could possibly be one of the subtle iOS assaults seen thus far.
Supply: Kaspersky
Whereas it is nonetheless unknown who’s behind the assaults, their sophistication has led cybersecurity researchers to consider {that a} government-sponsored hacking group is behind them.
1. The MOVEit Switch information theft assaults
BleepingComputer was the primary to report the widespread data-theft assaults exploiting a zero-day vulnerability within the MOVEit Switch safe file switch platform.
MOVEit Switch is a managed file switch (MFT) answer developed by Ipswitch, a subsidiary of US-based Progress Software program Company, that enables the enterprise to securely switch recordsdata between enterprise companions and prospects utilizing SFTP, SCP, and HTTP-based uploads.
This vulnerability allowed the menace actors to breach MOVEit Switch servers and obtain the saved information.
The assaults had been quickly claimed by the Clop ransomware gang, who beforehand launched related assaults by zero-day vulnerabilities in Accellion FTA and GoAnywhere.
Based on Emsisoft, 2,706 organizations had been breached utilizing this vulnerability, exposing the private information of over 93 million folks.




