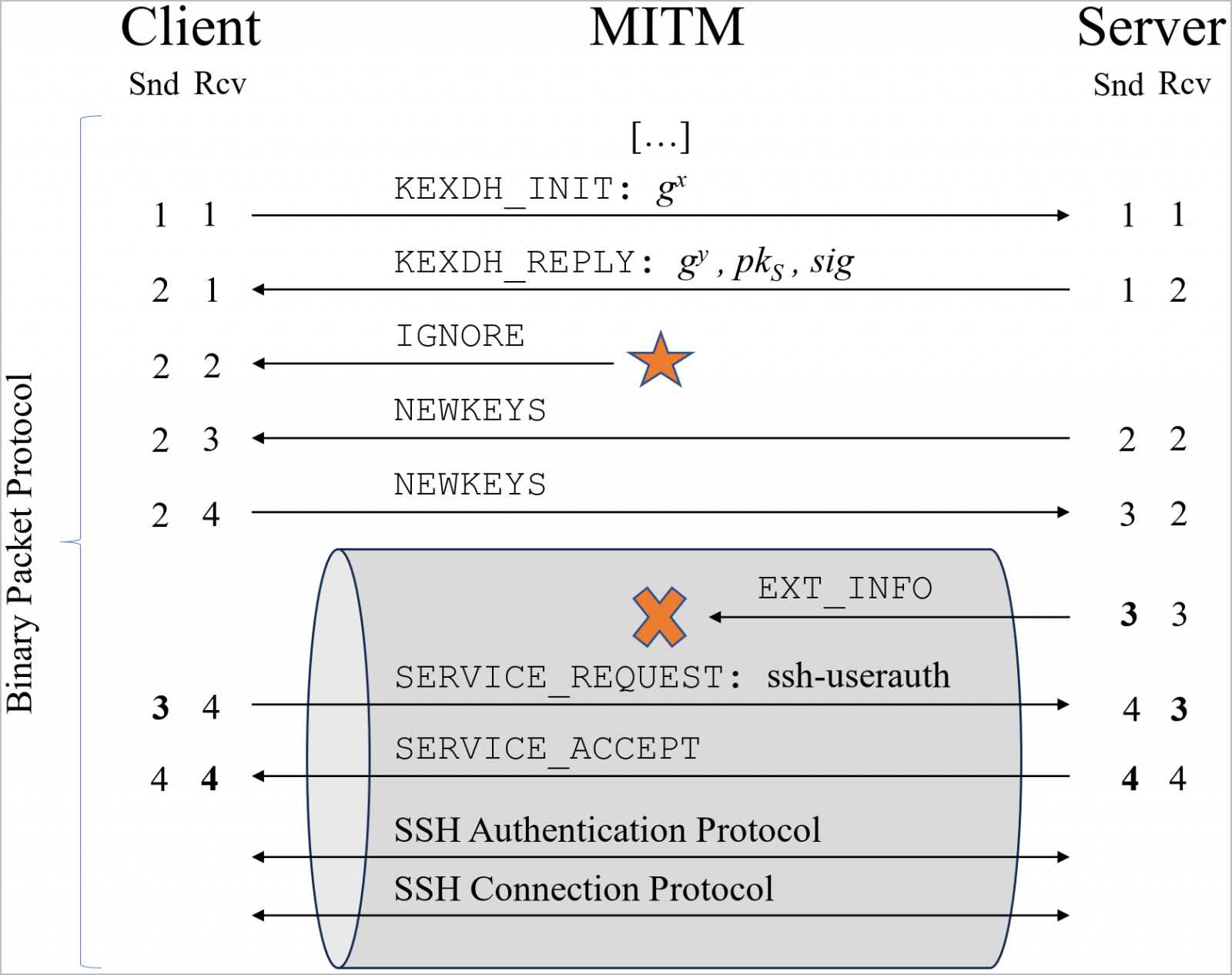
Educational researchers developed a brand new assault referred to as Terrapin that manipulates sequence numbers throughout the handshake course of to breaks the SSH channel integrity when sure widely-used encryption modes are used.
This manipulation lets attackers take away or modify messages exchanged by means of the communication channel, which ends up in downgrading the general public key algorithms used for person authentication or disabling defenses towards keystroke timing assaults in OpenSSH 9.5.
“The Terrapin assault exploits weaknesses within the SSH transport layer protocol together with newer cryptographic algorithms and encryption modes launched by OpenSSH over 10 years in the past.”
A Terrapin assault lowers the security of the established connection by truncating essential negotiation messages with out the shopper or server noticing it.
Researchers from the Ruhr College Bochum developed the Terrapin assault and in addition found exploitable implementation flaws in AsyncSSH.
The weaknesses and flaws related to the assault are bow recognized as CVE-2023-48795, CVE-2023-46445 and CVE-2023-46446.
One factor to notice about Terrapin is that the attackers should be in an adversary-in-the-middle (MiTM) place on the community layer to intercept and modify the handshake change, and the connection have to be secured by both ChaCha20-Poly1305 or CBC with Encrypt-then-MAC.
The information within the messages exchanged after the completion of the handshake determines the severity of the assault’s repercussions.
Regardless of the particular necessities for Terrapin, the in depth adoption of the talked about encryption modes (scans present 77%) makes the assault possible in a real-world situation.
“The Terrapin assault exploits weaknesses within the SSH transport layer protocol together with newer cryptographic algorithms and encryption modes launched by OpenSSH over 10 years in the past,” say the researchers, including that “these have been adopted by a variety of SSH implementations, due to this fact affecting a majority of present implementations.”
A number of distributors are progressively mitigating the security downside. One answer is to implement a strict key change that makes bundle injection throughout the handshake unattainable.
Nonetheless, it is going to take some time for such a difficulty to be addressed universally and the researchers notice that the strict key change countermeasure is simply efficient when carried out on each the shopper and the server.
The workforce has printed a Terrapin vulnerability scanner on GitHub, which admins can use to find out if an SSH shopper or server is susceptible to the assault.
Terrapin just isn’t a easy software program bug that may be mounted with an replace to a single library or element. As a substitute, purchasers and servers should be up to date to guard the connection towards prefix truncation assaults. – Ruhr College Bochum
Proper now, the largest mitigation issue for the assault is the MiTM requirement, which makes Terrapin a much less extreme risk. For that reason, patching CVE-2023-48795 might not be a precedence in lots of circumstances.
Extra particulars concerning the Terrapin assault can be found within the technical whitepaper launched by the German researchers.




