Synology has addressed a critical-severity distant code execution (RCE) vulnerability in BeeStation merchandise that was demonstrated on the latest Pwn2Own hacking competitors.
The security challenge (CVE-2025-12686) is described as a ‘buffer copy with out checking the scale of enter’ drawback, and will be exploited to permit arbitrary code execution.
It impacts a number of variations of BeeStation OS, the software program powering Synology’s network-attached storage (NAS) units marketed as a consumer-oriented “private cloud.”

There are not any mitigations out there, so the seller recommends that customers improve to the next variations, which handle :
- BeeStation OS model 1.3.2-65648 or above
- BeeStation OS model 1.3.2-65648 or above
- BeeStation OS model 1.3.2-65648 or above
- BeeStation OS model 1.3.2-65648 or above
Researchers Tek and anyfun at French cybersecurity firm Synacktiv exploited the flaw in an illustration in the course of the Pwn2Own Eire 2025 contest on October twenty first. For his or her profitable exploitation, the 2 researchers acquired a $40,000 reward.
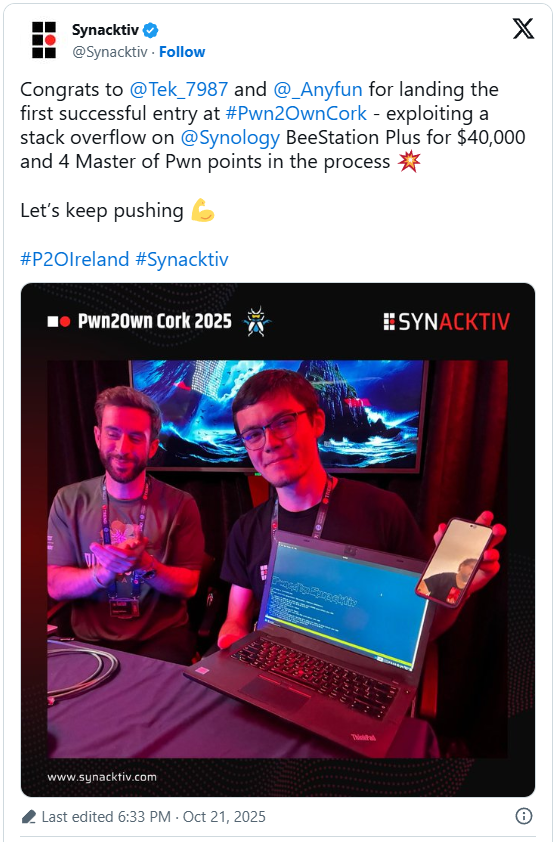
A 3-day hacking competitors organized by Development Micro and the Zero Day Initiative (ZDI), Pwn2Own provides security researchers the chance to hack standard client units utilizing zero-day vulnerabilities.
The newest occasion held in Eire had researchers demonstrating 73 zero-day flaws throughout a broad vary of merchandise and successful greater than $1 million.
Final week, one other main NAS vendor, QNAP, mounted a complete of seven zero-day vulnerabilities in a number of units from the corporate, which white-hat hackers had proven at Pwn2Own Eire this 12 months.
ZDI has a disclosure settlement with corporations collaborating in Pwn2Own and holds off publishing the technical particulars of the security points till patches can be found and customers have had ample time to use the updates.
Extra particulars about these flaws will likely be disclosed within the coming months on ZDI’s bulletin board and, in some circumstances, on private weblog areas of the researchers themselves.

As MCP (Mannequin Context Protocol) turns into the usual for connecting LLMs to instruments and information, security groups are shifting quick to maintain these new companies protected.
This free cheat sheet outlines 7 greatest practices you can begin utilizing in the present day.




