As organizations more and more search to help and safe extra distant community connections, many are rethinking the standard VPN. Many VPN alternate options exist to assist safe distant entry — mesh VPNs chief amongst them.
Mesh digital non-public networks (VPNs) use a peer-to-peer structure that may theoretically be cheaper than conventional VPN approaches. VPNs, that are estimated for use by 1.6 billion individuals, don’t carry the identical weight they used to within the security stack, given large security holes, port shadow weaknesses, and broad consensus on their susceptibility to cyberattacks.
Nonetheless, the worldwide VPN market is powerful — and anticipated to virtually triple by 2030 to $137 billion.
In legacy community stacks a VPN was used to entry network-based sources akin to on-prem line of enterprise apps and file shares as for those who have been on the company community. In conventional enterprise networks for those who have been inside the community perimeter you had inherent network-level entry to most the whole lot on the community. Hybrid networks and a push towards zero-trust ideas have the trade transferring away from this mind-set, making the idea of a community perimeter much less of a focus in terms of securing enterprises. In the event you’re working a conventional hub-and-spoke VPN structure, making the swap to mesh VPN is likely to be value contemplating.
Why mesh VPN
Mesh VPN is a comparatively new idea that’s shortly gaining momentum as extra distributors convey their companies to market. At its core, mesh VPN solves a number of weaknesses within the conventional VPN method and basically integrates tightly with present security stacks.
Decreased assault floor
In contrast to a client-server VPN with a hub-and-spoke mannequin, there isn’t a VPN server on the perimeter as a possible assault floor. Conventional VPN servers are regularly simple to establish as there are a finite variety of VPN requirements and even proprietary protocols. This makes discovery a cinch and assault a pure development for dangerous actors. Conversely, members of a mesh VPN can reside behind a company firewall, on a house community, or on a mobile connection, behind NAT and different technical parts that regularly trigger problem with VPNs. The power for nodes to attach to one another comes from a management aircraft that’s usually managed and maintained by the VPN vendor.
Higher help for Edge gadgets
Conventional VPNs primarily are available in two flavors: site-to-site and distant entry. With present networks extending to edge gadgets tasked with enabling enterprise operations many edge deployments require both a software program VPN consumer or a community equipment configured with a site-to-site VPN connection. Mesh VPNs can actually leverage a software program VPN consumer on all the well-liked working techniques however may also be carried out straight into containerized purposes and different cutting-edge deployments that is probably not an amazing match for conventional VPNs.
Centered entry to networked companies
Mesh VPNs by default solely present entry to different members of the mesh VPN, to not your complete community. This might embody servers, workstations, storage gadgets, cloud-based sources, and even software containers. This functionality can usually be additional refined to offer entry solely to the gadgets and companies applicable for a selected person: which means whereas a wide range of techniques and companies are accessible on the mesh VPN, particular person customers solely have entry to the companies to which they’ve a enterprise want for entry. The online results of these capabilities is basically dynamic firewall guidelines between nodes based mostly on the person’s roles and enterprise necessities. From a administration perspective, nodes and companies may be grouped and restricted utilizing ideas which are acquainted to cloud directors akin to useful resource tagging and entry management lists.
Automated administration
Most mesh VPN options additional improve these ideas by providing API-based administration, which means the method of assigning roles and entry may be built-in with different administration and orchestration instruments already being leveraged inside the group. This may very well be within the type of an prolonged detection and response (XDR) resolution, or just script-based automation that interacts with enterprise techniques.
Integration with present security instruments
Mesh VPN options are constructed from the bottom up for hybrid work. As such, security staples like id administration (IDM) and cell system administration (MDM) assist type a cohesive basis for the hybrid workforce. Integration with IDM helps streamline onboarding (and maybe extra importantly offboarding), in addition to dynamic adjustments to system entry based mostly on adjustments to person identities. Mesh VPN options make sense in security gadgets alongside MDM as buyer laptops, tablets, and even cellphones can probably be added as VPN nodes.
Earlier than you bounce
For a mesh VPN service to achieve success within the enterprise there are some non-negotiables. Integration with present authentication companies is an absolute should, and this extends to authenticating gadgets and making certain they meet system administration insurance policies. Moreover, integration with present instruments within the security stack akin to occasion monitoring and EDR (endpoint detection and response) goes to be a tough requirement for gadgets accessing protected companies.
Why not mesh VPN
Mesh VPN options examine quite a lot of packing containers, however as at all times there’s a flip facet of the coin. Companies nonetheless working in additional of an old-school, on-prem structure will probably have higher choices for a few causes.
Structure
Companies nonetheless functioning with the idea of a tough community perimeter and little to no cloud presence could not garner a lot worth from the hybrid id and zero-trust capabilities which mesh VPN can assist introduce. Likewise, if enterprise sources (akin to file servers or line of enterprise apps) are primarily contained inside the community perimeter a centralized VPN server often is the higher funding.
Price
Talking of investments, one probably main draw back to mesh VPN options comes right down to subscription prices. Most mesh VPN choices have a month-to-month subscription price per person, which may add up shortly, notably for among the extra premium capabilities. As increasingly legacy VPN options pivot to subscription-based licensing this concern have to be weighed fastidiously.
How you can: Help connectivity to centralized company sources
VPNs have been used as a method to enable distant customers to entry sources inside the perimeter of the company community. Mesh VPNs are designed as a peer-to-peer community, which means the scope of the community extends by default solely to these gadgets with the VPN consumer put in. This turns into a little bit of a difficulty when making an attempt to offer entry to purposes or companies in a centralized location. Do you put in the VPN consumer on every server? How do you help workloads which are clustered throughout a number of servers, or run in a stack like containerized apps? What about gadgets that merely don’t help software program set up, akin to industrial {hardware} and even printers?
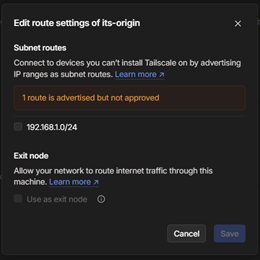
Tailscale presents the idea of subnet routers to operate as a gateway to a number of gadgets on a community section. This characteristic permits customers to put in the Tailscale consumer on a single laptop inside a community, and configure it to offer connectivity to different gadgets on that community. The method to allow a subnet router in Tailscale requires two steps for security functions. First, you should configure the Tailscale node as a subnet router, which on Home windows entails beginning Tailscale from the command line utilizing the --advertise-routes parameter adopted by IPv4 subnets outlined in CIDR notation. For instance, the next command serves your complete 192.168.1.x Class C subnet to the Tailscale community (the tailnet).
tailscale up --advertise-routes=192.168.1.0/24
Particular person endpoints may be shared by specifying the total IP handle adopted by the /32 CIDR subnet masks. A number of subnets (or endpoints) may be outlined by separating them with a comma.
The second step to allow a subnet router entails utilizing the Tailscale admin console to allow particular person routes.
Tim Ferrill
Tim Ferrill
As soon as the route is accredited within the admin console, tailnet members will be capable to entry the purposes and companies on the goal subnet.
How you can: Prohibit entry to sources and companies to approved customers
In a zero-trust world entry to company sources needs to be restricted to the minimal variety of customers required. Having the ability to entry the company community by way of a VPN shouldn’t routinely grant entry to net servers or file shares, even on the community degree. Tailscale presents instruments to restrict what gadgets and customers can attain community sources utilizing entry management lists (ACLs).
ACLs in Tailscale boil right down to a supply and a vacation spot. In contrast to conventional firewall guidelines, Tailscale ACLs at all times end in an ‘enable’ motion; connectivity is barely allowed for those who explicitly outline a rule. Throughout the Tailscale ACL coverage editor, you may leverage customers or gadgets in bulk utilizing teams or tags respectively, or individually utilizing host or usernames. Entry to gadgets or subnets made accessible to the Tailnet utilizing subnet routing may also be allowed by referencing the subnet within the vacation spot portion of the rule:
{
"motion": "settle for",
"src": ["tag:mobile"],
"dst": ["192.168.1.0/24:80,139,443,445"],
},
This rule states that gadgets with the cell tag are allowed to connect with gadgets on the 192.168.1.0/24 subnet, however solely on ports 80, 139, 443, and 445. Asterisks can be utilized as wildcards for each supply and vacation spot, both for the host or the allowed ports.
How you can: Route web visitors from distant shoppers by way of a central community
One widespread VPN use case is to guard delicate web visitors whereas gadgets are linked to public networks. Some industries require web visitors to be monitored and/or filtered. There are a number of methods to attain these necessities, however having all visitors routed by way of a central community has the potential to streamline the method. Tailscale’s exit node characteristic facilitates assembly these wants.
Exit nodes are configured equally to subnet routing. The choice is enabled within the Tailscale consumer on the system designated because the exit node, after which the configuration is accredited by an admin within the admin console. Exit nodes may be configured as really helpful (also referred to as prompt) or necessary, which permits Tailscale to both choose an exit node based mostly on latency or efficiency or to power cell customers to ship all visitors by way of a single exit node. Obligatory exit nodes require Tailscale’s premium or enterprise plan, in addition to an MDM resolution.
How you can: Leverage company DNS servers for Tailscale shoppers
By default, Tailscale makes use of a characteristic termed ‘Magic DNS’ to offer identify decision to tailnet members. This identify decision doesn’t lengthen to gadgets served on subnets and might show problematic when making an attempt to entry companies predicated on DNS akin to Energetic Listing.
Tailscale presents, nonetheless, the power to outline a number of inner DNS servers to make use of for identify decision. These DNS server entries may be configured for break up DNS, offering the power to solely ahead requests for a particular area to the interior DNS server. Combining break up DNS with subnet routing and ACLs presents a compelling mix of performance.
How you can: Obtain separation of duties inside Tailscale
Making a full-featured VPN resolution is nice and all, but it surely’s not the tip of the story in fashionable IT security and compliance necessities. Separation of duties is a key finest apply and a frequent part of compliance checklists. Tailscale presents a number of built-in roles you may shortly use to satisfy these enterprise wants:
- Community admins are the directors for the Tailscale account and have permissions to handle all features of the community configuration. Consumer and system settings are may be considered by community admins, however they’re unable to make adjustments even to their very own gadgets
- IT admins are much less targeted on the networking features of the Tailscale account and extra on customers and gadgets. IT admins can view community particulars, together with ACLs contained within the tailnet coverage file, however can not make any adjustments.
- Billing admins can handle pricing plans and billing info. They do have view entry to all features of the admin console, however can not make adjustments to networks, gadgets, or customers.
- Auditors have learn entry to all features of the admin console, however no potential to make adjustments. This function is especially helpful for compliance or audit causes, and even high quality assurance.
- Members have user-level entry to tailnet. They don’t have any entry to the admin console however can connect with your tailnet and gadgets as allowed by ACLs.
Two extra roles, proprietor and admins, have full entry to all features of the admin console. There can solely be one proprietor, and as a way to delete that account the proprietor function should first be transferred.




