Elevated hacker exercise has been noticed in makes an attempt to compromise poorly maintained gadgets which might be susceptible to older security points from 2022 and 2023.
Risk monitoring platform GreyNoise is reporting spikes in actors leveraging CVE-2022-47945 and CVE-2023-49103 that have an effect on ThinkPHP Framework and the open-source ownCloud resolution for file sharing and syncing.
Each vulnerabilities have vital severity and will be exploited to execute arbitrary working system instructions or to acquire delicate information (e.g. admin password, mail server credentials, license key).
The primary vulnerability is a native file inclusion (LFI) subject within the language parameter of ThinkPHP Framework earlier than 6.0.14. An unauthenticated distant attacker can leverage it to execute arbitrary working system instructions in deployments the place the language pack function is enabled.
Akamai reported final summer season that Chinese language risk actors have been leveraging the flaw since October 2023 in narrow-scope operations.
In response to risk monitoring platform GreyNoise, CVE-2022-47945 is beneath high-volume exploitation proper now, with assaults launched from a rising variety of supply IPs.
“GreyNoise has noticed 572 distinctive IPs trying to take advantage of this vulnerability, with exercise rising in latest days,” warns the bulletin.
That is regardless of its low Exploit Prediction Scoring System (EPSS) ranking of seven% and the flaw not being included in CISA’s Identified Exploited Vulnerabilities (KEV) catalog.
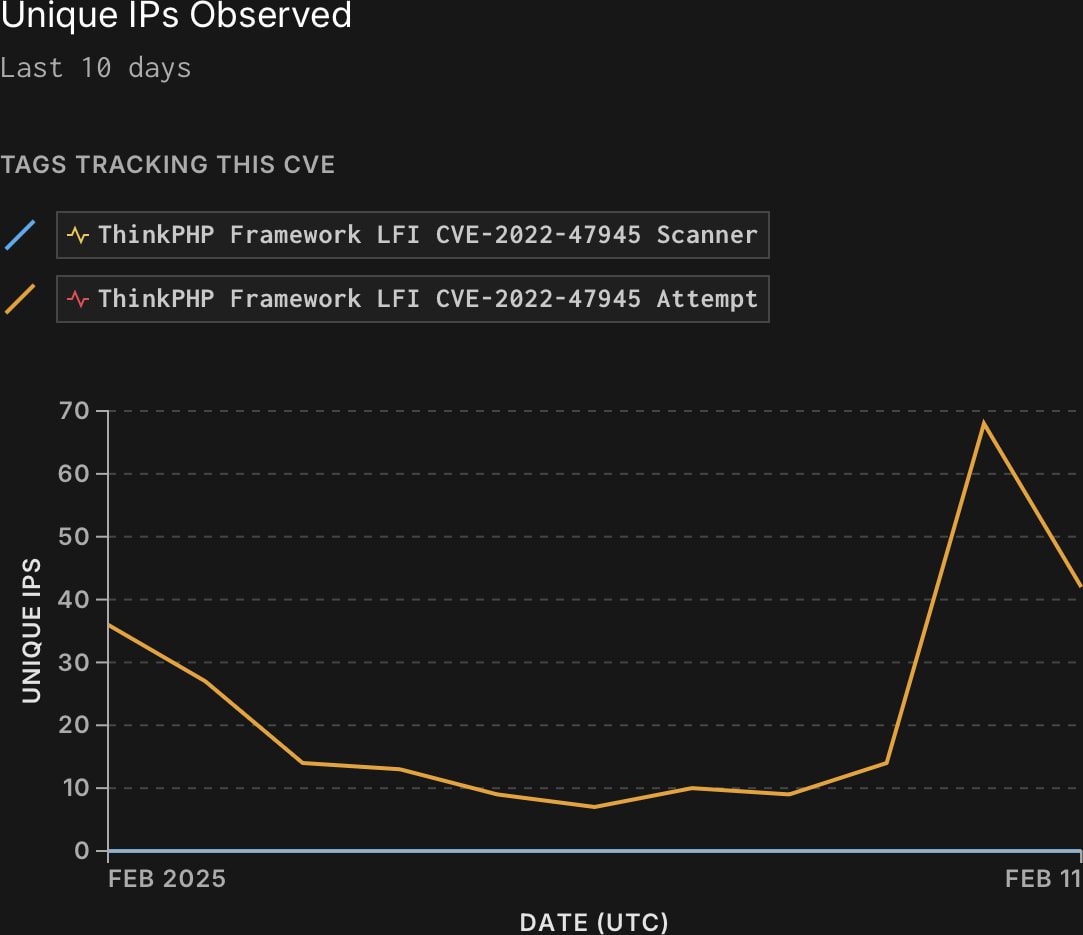
Supply: Greynoise
The second vulnerability impacts the favored open-source file-sharing software program and arises from the app’s dependency on a third-party library that exposes PHP atmosphere particulars by a URL.
Quickly after the vulnerability’s preliminary disclosure from the builders in November 2023, hackers began exploiting it to steal delicate data from unpatched programs.
A yr later, CVE-2023-49103 was listed by the FBI, CISA, and NSA, among the many 15 most exploited vulnerabilities of 2023.
Regardless of over 2 years having handed because the vendor launched an replace that addresses the security subject, many situations stay unpatched and uncovered to assaults.
GreyNoise noticed elevated exploitation of CVE-2023-49103 lately, with malicious exercise originating from 484 distinctive IPs.
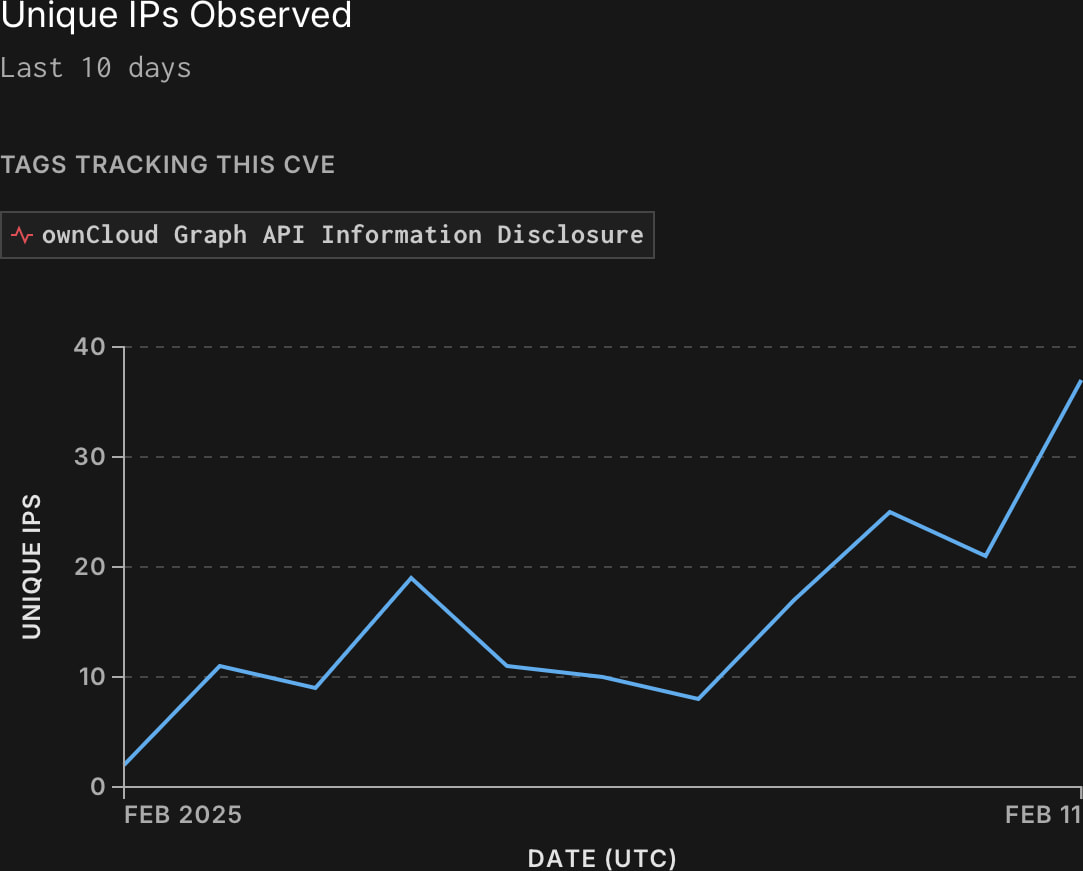
Supply: Greynoise
To safeguard programs in opposition to lively exploitation customers are suggested to improve to ThinkPHP 6.0.14 or later, and ownCloud GraphAPI to 0.3.1 and newer.
It is usually beneficial that probably susceptible situations are taken offline or positioned behind a firewall to scale back the assault floor.




