SquareX, an industry-first Browser Detection and Response (BDR) resolution, leads the way in which in browser security. A couple of week in the past, SquareX reported large-scale assaults concentrating on Chrome Extension builders aimed toward taking on the Chrome Extension from the Chrome Retailer.
On December twenty fifth, 2024, a malicious model of Cyberhaven’s browser extension was revealed on the Chrome Retailer that allowed the attacker to hijack authenticated periods and exfiltrate confidential data. The malicious extension was accessible for obtain for greater than 30 hours earlier than being eliminated by Cyberhaven. The info loss prevention firm declined to touch upon the extent of the impression when approached by the press, however the extension had over 400,000 customers on the Chrome Retailer on the time of the assault.
Sadly, the assault came about as SquareX’s researchers had recognized an analogous assault with a video demonstrating your entire assault pathway only a week earlier than the Cyberhaven breach. The assault begins with a phishing e-mail impersonating Chrome Retailer containing a supposed violation of the platform’s “Developer Settlement”, urging the receiver to simply accept the insurance policies to stop their extension from being faraway from Chrome Retailer. Upon clicking on the coverage button, the person will get prompted to attach their Google account to a “Privateness Coverage Extension”, which grants the attacker entry to edit, replace and publish extensions on the developer’s account.
Fig 1. Phishing e-mail concentrating on extension builders
Cyber NewsWire
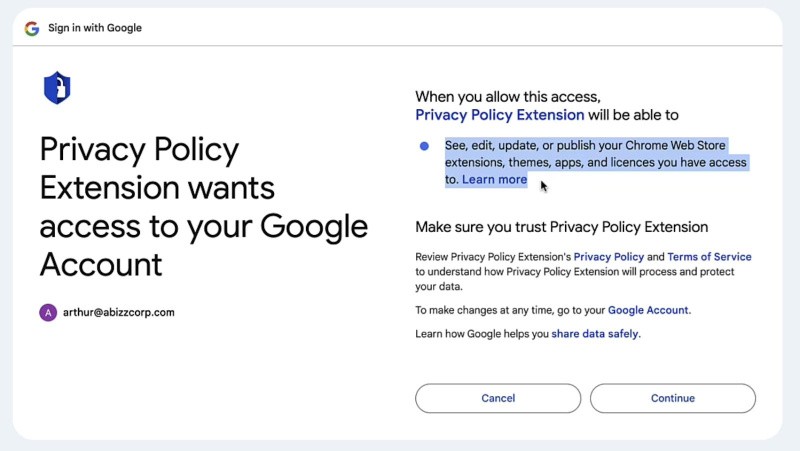
Fig 2. Pretend Privateness Coverage Extension requesting entry to “edit, replace or publish” the developer’s extension
Cyber NewsWire
Extensions have turn out to be an more and more well-liked method for attackers to realize preliminary entry. It’s because most organizations have restricted purview on what browser extensions their workers are utilizing. Even essentially the most rigorous security groups usually don’t monitor subsequent updates as soon as an extension is whitelisted.
SquareX has performed in depth analysis and demonstrated at DEFCON 32, how MV3-compliant extensions can be utilized to steal video stream feeds, add a silent GitHub collaborator, and steal session cookies, amongst others. Attackers can create a seemingly innocent extension and later convert it right into a malicious one post-installation or, as demonstrated within the assault above, deceive the builders behind a trusted extension to realize entry to at least one that already has a whole bunch of 1000’s of customers. In Cyberhaven’s case, attackers had been in a position to steal firm credentials throughout a number of web sites and net apps by the malicious model of the extension.
Provided that developer emails are publicly listed on Chrome Retailer, it’s straightforward for attackers to focus on 1000’s of extension builders directly. These emails are usually used for bug reporting. Thus, even help emails listed for extensions from bigger firms are often routed to builders who might not have the extent of security consciousness required to seek out suspicion in such an assault. As per SquareX’s assault disclosure and the Cyberhaven breach that occurred inside the span of lower than two weeks, the corporate has robust motive to consider that many different browser extension suppliers are being attacked in the identical method. SquareX urges firms and people alike to conduct a cautious inspection earlier than putting in or updating any browser extensions.
Fig 3. Contact particulars of extension builders are publicly accessible on Chrome Retailer
Cyber NewsWire
SquareX group understands that it may be non-trivial to judge and monitor each single browser extension within the workforce amidst all of the competing security priorities, particularly in relation to zero-day assaults. As demonstrated within the video, the pretend privateness coverage app concerned in Cyberhaven’s breach was not even detected by any well-liked menace feeds.
SquareX’s Browser Detection and Response (BDR) resolution takes this complexity off security groups by:
- Blocking OAuth interactions to unauthorized web sites to stop workers from unintentionally giving attackers unauthorized entry to your Chrome Retailer account
- Blocking and/or flagging any suspicious extension updates containing new, dangerous permissions
- Blocking and/or flagging any suspicious extensions with a surge of damaging critiques
- Blocking and/or flagging installations of sideloaded extensions
- Streamline all requests for extension installations exterior the approved record for fast approval primarily based on firm coverage
- Full visibility on all extensions put in and utilized by workers throughout the group
SquareX’s founder Vivek Ramachandran warns: “Identification assaults concentrating on browser extensions just like this OAuth assault will solely turn out to be extra prevalent as workers depend on extra browser-based instruments to be productive at work. Related variants of those assaults have been used previously to steal cloud knowledge from apps like Google Drive and One Drive and we’ll solely see attackers get extra inventive in exploiting browser extensions. Corporations want to stay vigilant and decrease their provide chain threat with out hampering worker productiveness by equipping them with the suitable browser native instruments.”
About SquareX:
SquareX helps organizations detect, mitigate, and threat-hunt client-side net assaults taking place towards their customers in real-time.
SquareX’s industry-first Browser Detection and Response (BDR) resolution, takes an attack-focused strategy to browser security, guaranteeing enterprise customers are protected towards superior threats like malicious QR Codes, Browser-in-the-Browser phishing, macro-based malware, and different net assaults encompassing malicious recordsdata, web sites, scripts, and compromised networks.
With SquareX, enterprises can present contractors and distant staff with safe entry to inside functions, and enterprise SaaS, and convert the browsers on BYOD / unmanaged units into trusted looking periods.
Contact
Head of PR
Junice Liew
SquareX
junice@sqrx.com




