SonicWall’s SonicOS is weak to a essential entry management flaw that might permit attackers to realize entry unauthorized entry to sources or trigger the firewall to crash.
The flaw has obtained the identifier CVE-2024-40766 and a severity rating of 9.3 in response to the CVSS v3 customary, primarily based on its network-based assault vector, low complexity, no authentication, and no consumer interplay necessities.
“An improper entry management vulnerability has been recognized within the SonicWall SonicOS administration entry, doubtlessly resulting in unauthorized useful resource entry and in particular circumstances, inflicting the firewall to crash,” reads SonicWall’s bulletin.
“This problem impacts SonicWall Firewall Gen 5 and Gen 6 units, in addition to Gen 7 units working SonicOS 7.0.1-5035 and older variations.”
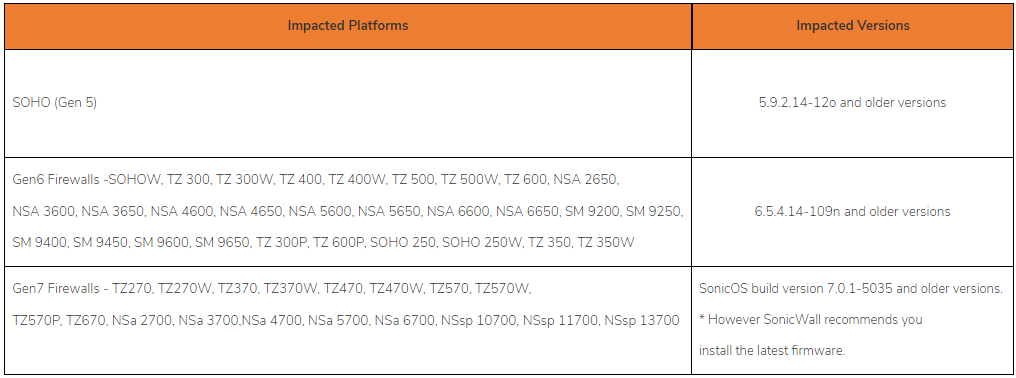
Particular fashions impacted are:
- Gen 5: SOHO units working model 5.9.2.14-12o and older
- Gen 6: Numerous TZ, NSA, and SM fashions working variations 6.5.4.14-109n and older
- Gen 7: TZ and NSA fashions working SonicOS construct model 7.0.1-5035 and older
Supply: SonicWall
It is strongly recommended that system directors transfer to the under variations, which handle CVE-2024-40766:
- For Gen 5: Model 5.9.2.14-13o
- For Gen 6: Model 6.5.4.15.116n
- For SM9800, NSsp 12400, and NSsp 12800, model 6.5.2.8-2n is secure
- For Gen 7: Any SonicOS firmware model larger than 7.0.1-5035
The security updates have been made obtainable for obtain via mysonicwall.com.
Those that can’t apply the fixes instantly are beneficial to limit firewall administration entry to trusted sources or disable WAN administration entry from the web. Extra info on how to do that could be discovered on SonicWall’s assist web page.
SonicWall firewalls are extensively utilized in a broad vary of mission-critical industries and company environments and are generally focused by risk actors to realize preliminary entry to company networks.
In March 2023, suspected Chinese language hackers tracked as UNC4540 attacked SonicWall Safe Cellular Entry (SMA) home equipment with customized malware that might persist via firmware upgrades.
The US Cybersecurity & Infrastructure Safety Company (CISA) has warned about energetic exploitation of flaws impacting SonicWall home equipment since 2022.




