SonicWall is warning {that a} lately fastened entry management flaw tracked as CVE-2024-40766 in SonicOS is now “probably” exploited in assaults, urging admins to use patches as quickly as doable.
“This vulnerability is probably being exploited within the wild. Please apply the patch as quickly as doable for affected merchandise. The most recent patch builds can be found for obtain on mysonicwall.com,” warns the up to date SonicWall advisory.
CVE-2024-40766 is a important (CVSS v3 rating: 9.3) entry management flaw impacting SonicWall Firewall Gen 5 and Gen 6 gadgets, in addition to Gen 7 gadgets.
The software program vendor didn’t disclose a lot details about the flaw apart from its potential for unauthorized useful resource entry and skill to crash the firewall, thus eliminating community protections.
When SonicWall first disclosed the flaw on August 22, 2024, the flaw was solely believed to be within the SonicWall SonicOS administration entry. With right now’s replace, the corporate is warning that CVE-2024-40766 additionally impacts the firewall’s SSLVPN characteristic.
Apply patches as quickly as doable
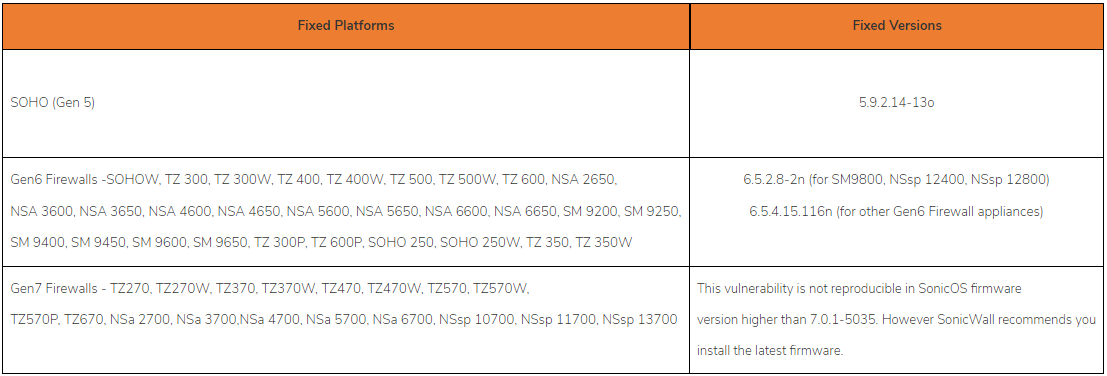
The listing of impacted merchandise and variations, in addition to the releases that tackle CVE-2024-40766, are summarized as follows:
- SonicWall Gen 5 working SonicOS model 5.9.2.14-12o and older – fastened in SonicOS model 5.9.2.14-13o
- SonicWall Gen 6 working SonicOS model 6.5.4.14-109n and older – fastened in 6.5.2.8-2n (for SM9800, NSsp 12400, NSsp 12800) and model 6.5.4.15-116n (for different Gen 6 Firewalls)
- SonicWall Gen 7 working SonicOS model 7.0.1-5035 and older – not reproducible in 7.0.1-5035 and later.
The most recent mitigation suggestions by SonicWall embody:
- Restrict firewall administration to trusted sources and disable web entry to the WAN administration portal if doable.
- Limit SSLVPN entry to trusted sources solely and disable it fully if not wanted.
- For Gen 5 and Gen 6 gadgets, SSLVPN customers with native accounts ought to replace their passwords instantly and directors ought to allow the “Consumer should change password” choice for native customers.
- Allow multi-factor authentication (MFA) for all SSLVPN customers utilizing TOTP or email-based one-time passwords (OTPs). Extra info on how one can configure this measure is accessible right here.
Whereas SonicWall has not shared how the flaw is being actively exploited, comparable flaws have been used previously to realize preliminary entry to company networks.
Risk actors generally goal SonicWall as they’re uncovered to the web to supply distant VPN entry.
In March 2023, suspected Chinese language hackers (UNC4540) focused unpatched SonicWall Safe Cell Entry (SMA) gadgets to put in customized malware that persevered by means of firmware upgrades.
BleepingComputer contacted SonicWall to study extra about how the flaw is being actively exploited in assaults, however a response was not instantly accessible.




