Safety researchers at Bishop Fox have revealed full exploitation particulars for the CVE-2024-53704 vulnerability that enables bypassing the authentication mechanism in sure variations of the SonicOS SSLVPN utility.
The seller warned concerning the excessive exploitation chance of the flaw in a bulletin on January 7, urging directors to improve their SonicOS firewalls’ firmware to handle the issue.
“We now have recognized a firewall vulnerability that’s inclined to precise exploitation for patrons with SSL VPN or SSH administration enabled, and that must be mitigated instantly by upgrading to the newest firmware,” warned SonicWall in an e-mail despatched to prospects on the time.
The flaw permits a distant attacker to hijack lively SSL VPN classes with out authentication, granting them unauthorized entry to the sufferer’s community.
On January 22 Bishop Fox researchers introduced that they’d developed an exploit for CVE-2024-53704 after a “important reverse-engineering effort,” confirming SonicWall’s fears concerning the exploitation potential of the vulnerability.
Supply: Bishop Fox
After permitting a while for system directors to use the out there patches, Bishop Fox launched the complete exploitation particulars on Monday.
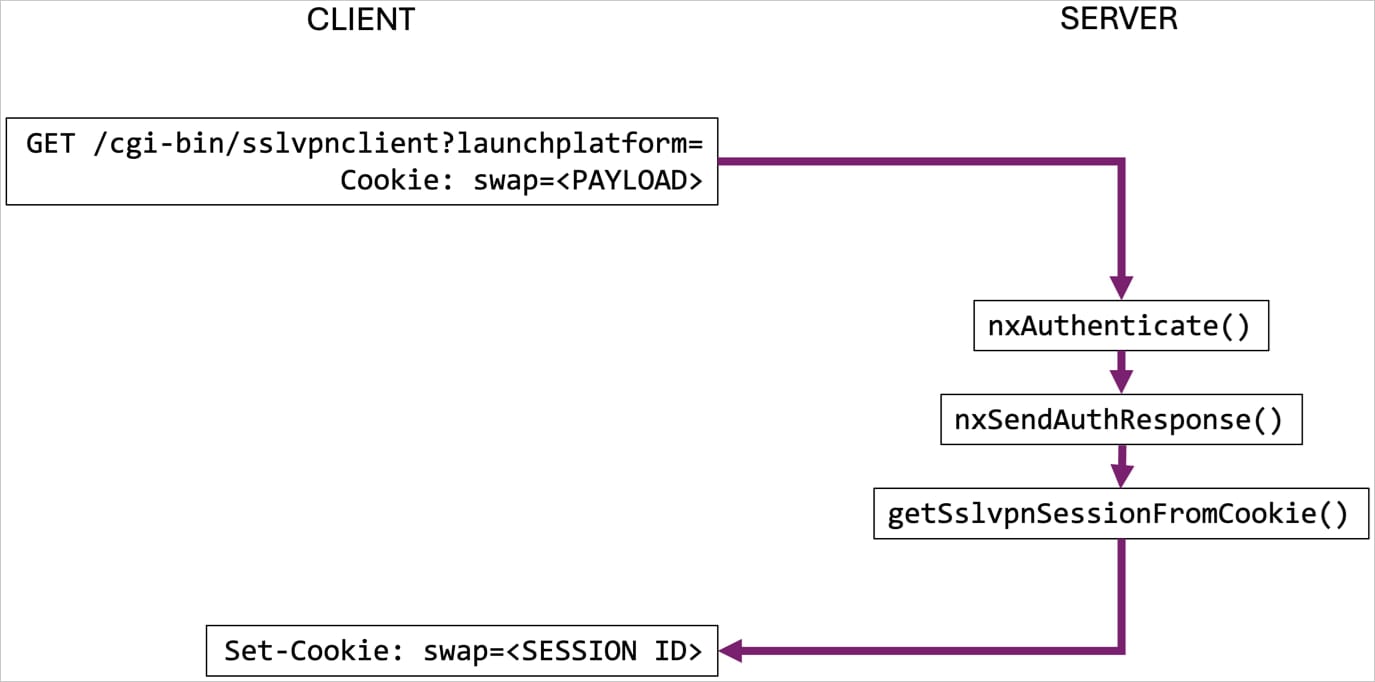
The exploit works by sending a specifically crafted session cookie containing a base64-encoded string of null bytes to the SSL VPN authentication endpoint at ‘/cgi-bin/sslvpnclient.’
This triggers an incorrect validation of the session, because the mechanism assumes that the request is related to an lively VPN session.
This logs out the sufferer and offers the attacker entry to the session, permitting them to learn the consumer’s Digital Workplace bookmarks, acquire VPN shopper configuration settings, open a VPN tunnel to the interior community, and offers entry to non-public community assets.
Supply: Bishop Fox
The researchers put the validity of their evaluation to the check and created a proof-of-concept exploit code to simulate an authentication bypass assault. The response headers confirmed that they’d efficiently hijacked an lively session.
“With that, we have been in a position to establish the username and area of the hijacked session, together with non-public routes the consumer was in a position to entry via the SSL VPN,” the researchers stated.
Safety updates out there
The problem impacts SonicOS variations 7.1.x (as much as 7.1.1-7058), 7.1.2-7019, and eight.0.0-8035. These variations run in a number of fashions of Gen 6 and Gen 7 firewalls, in addition to SOHO sequence units.
Fixes have been made out there in SonicOS 8.0.0-8037 and later, 7.0.1-5165 and better, 7.1.3-7015 and better, and 6.5.5.1-6n and better. For model-specific data, try SonicWall’s bulletin right here.
Bishop Fox says that web scans as of February 7 present roughly 4,500 internet-exposed SonicWall SSL VPN servers with out the security updates fixing CVE-2024-53704.
With a working proof-of-concept exploit now publicly out there, admins ought to apply the updates as quickly as doable as a result of the exploitation danger for CVE-2024-53704 has elevated considerably.




