A wave of data breaches impacting firms like Qantas, Allianz Life, LVMH, and Adidas has been linked to the ShinyHunters extortion group, which has been utilizing voice phishing assaults to steal information from Salesforce CRM situations.
In June, Google’s Menace Intelligence Group (GTIG) warned that menace actors tracked as UNC6040 had been concentrating on Salesforce clients in social engineering assaults.
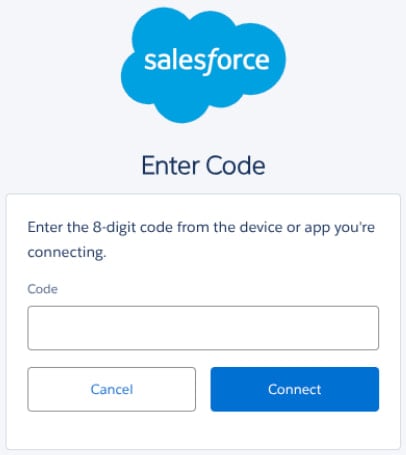
In these assaults, the menace actors impersonated IT help workers in telephone calls to focused staff, trying to influence them into visiting Salesforce’s related app setup web page. On this web page, they had been informed to enter a “connection code”, which linked a malicious model of Salesforce’s Data Loader OAuth app to the goal’s Salesforce surroundings.
In some instances, the Data Loader element was renamed to “My Ticket Portal,” to make it extra convincing within the assaults.
Supply: Google
GTIG says that these assaults had been normally carried out by vishing (voice phishing), however credentials and MFA tokens had been additionally stolen by phishing pages that impersonated Okta login pages.
Across the time of this report, a number of firms reported data breaches involving third-party customer support or cloud-based CRM methods.
LVMH subsidiaries Louis Vuitton, Dior, and Tiffany & Co. every disclosed unauthorized entry to a buyer info database, with Tiffany Korea notifying clients the attackers breached a “vendor platform used for managing buyer information.”
Adidas, Qantas, and Allianz Life additionally reported breaches involving third-party methods, with Allianz confirming it was a third-party buyer relationship administration platform.
“On July 16, 2025, a malicious menace actor gained entry to a third-party, cloud-based CRM system utilized by Allianz Life Insurance coverage Firm of North America (Allianz Life),” an Allianz Life spokesperson informed BleepingComputer.
Whereas BleepingComputer has realized that the Qantas data breach additionally concerned a third-party buyer relationship administration platform, the corporate is not going to verify it’s Salesforce. Nonetheless, earlier reporting from native media claims the info was stolen from Qantas’ Salesforce occasion.
Moreover, court docket paperwork state that the menace actors focused “Accounts” and “Contacts” database tables, each of that are Salesforce objects.
Whereas none of those firms have publicly named Salesforce, BleepingComputer has since confirmed that every one had been focused in the identical marketing campaign detailed by Google.
The assaults haven’t led to public extortion or information leaks but, with BleepingComputer studying that the menace actors try to privately extort firms over e mail, the place they identify themselves as ShinyHunters.
It’s believed that when these extortion makes an attempt fail, the menace actors will launch stolen info in a protracted wave of leaks, just like ShinyHunter’s earlier Snowflake assaults.
Who’s ShinyHunters
The breaches have precipitated confusion among the many cybersecurity group and the media, together with BleepingComputer, with the assaults attributed to Scattered Spider (tracked by Mandiant as UNC3944), as these menace actors had been additionally concentrating on the aviation, retail, and insurance coverage sectors across the similar time and demonstrated comparable ways.
Nonetheless, menace actors related to Scattered Spider are likely to carry out full-blown community breaches, culminating with information theft and, generally, ransomware. ShinyHunters, tracked as UNC6040, alternatively, tends to focus extra on data-theft extortion assaults concentrating on a specific cloud platform or net software.
It’s BleepingComputer’s and a few security researchers’ perception that each UNC6040 and UNC3944 encompass overlapping members that talk throughout the similar on-line communities. The menace group can be believed to overlap with “The Com,” a community of skilled English-speaking cybercriminals.
“In response to Recorded Future intelligence, the overlapping TTPs between recognized Scattered Spider and ShinyHunters assaults point out doubtless some crossover between the 2 teams,” Allan Liska, an Intelligence Analyst for Recorded Future, informed BleepingComputer.
Different researchers have informed BleepingComputer that ShinyHunters and Scattered Spider look like working in lockstep, concentrating on the identical industries on the similar time, making it tougher to attribute assaults.
Some additionally consider that each teams have ties to menace actors from the now-defunct Lapsus$ hacking group, with studies indicating that one of many lately arrested Scattered Spider hackers was additionally in Lapsus$.
One other idea is that ShinyHunters is performing as an extortion-as-a-service, the place they extort firms on behalf of different menace actors in alternate for a income share, just like how ransomware-as-a-service gangs function.
This idea is supported by earlier conversations BleepingComputer has had with ShinyHunters, the place they claimed to not be behind a breach, however simply performing as the vendor of the stolen information.
These breaches embrace PowerSchool, Oracle Cloud, the Snowflake data-theft assaults, AT&T, NitroPDF, Wattpad, MathWay, and plenty of extra.
Supply: BleepingComputer
To muddy the waters additional, there have been quite a few arrests of individuals linked to the identify “ShinyHunters,” together with those that have been arrested for the Snowflake data-theft assaults, breaches at PowerSchool, and the operation of the Breached v2 hacking discussion board.
But even after these arrests, new assaults happen with firms receiving extortion emails stating, “We’re ShinyHunters,” referring to themselves as a “collective.”
Defending Salesforce situations from assaults
In a press release to BleepingComputer, Salesforce emphasised that the platform itself was not compromised, however fairly, clients’ accounts are being breached by way of social engineering.
“Salesforce has not been compromised, and the problems described will not be as a result of any recognized vulnerability in our platform. Whereas Salesforce builds enterprise-grade security into every little thing we do, clients additionally play a crucial function in maintaining their information protected — particularly amid an increase in refined phishing and social engineering assaults,” Salesforce informed BleepingComputer.
“We proceed to encourage all clients to comply with security greatest practices, together with enabling multi-factor authentication (MFA), implementing the precept of least privilege, and punctiliously managing related purposes. For extra info, please go to: https://www.salesforce.com/weblog/protect-against-social-engineering/.”
Salesforce is urging clients to strengthen their security posture by:
- Implementing trusted IP ranges for logins
- Following the precept of least privilege for app permissions
- Enabling multi-factor authentication (MFA)
- Limiting use of related apps and managing entry insurance policies
- Utilizing Salesforce Protect for superior menace detection, occasion monitoring, and transaction insurance policies
- Including a delegated Safety Contact for incident communication
Additional particulars on these mitigations will be present in Salesforce’s steering linked above.

CISOs know that getting board buy-in begins with a transparent, strategic view of how cloud security drives enterprise worth.
This free, editable board report deck helps security leaders current danger, affect, and priorities in clear enterprise phrases. Flip security updates into significant conversations and quicker decision-making within the boardroom.




