LUCR-3 overlaps with teams comparable to Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated attacker that leverages the Id Supplier (IDP) as preliminary entry into an setting with the purpose of stealing Mental Property (IP) for extortion. LUCR-3 targets Fortune 2000 corporations throughout numerous sectors, together with however not restricted to Software program, Retail, Hospitality, Manufacturing, and Telecoms.
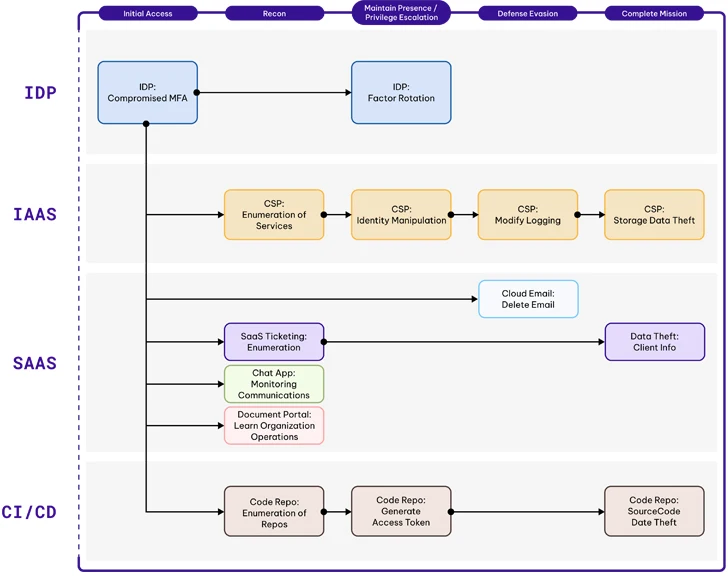
LUCR-3 doesn’t rely closely on malware and even scripts; as an alternative, LUCR-3 expertly makes use of victims’ personal instruments, functions, and assets to attain their targets. At a excessive degree, Preliminary Entry is gained via compromising current identities within the IDP (Okta: Id Cloud, Azure AD / Entra, Ping Id: PingOne). LUCR-3 makes use of SaaS functions comparable to doc portals, ticketing programs, and chat functions to find out how the sufferer group operates and methods to entry delicate info. Utilizing the information they gained from reconnaissance throughout the SaaS functions, they then perform their mission of knowledge theft. Data theft is often centered on IP, Code Signing Certificates, and buyer knowledge.
Attacker Attributes
Highlights
- LUCR-3 attribution is tough. Many people within the Cyber Intelligence neighborhood have even begun to trace the person personas individually. Additional complicated attribution, some LUCR-3 personas look like associates of ALPHV with entry to deploy BlackCat ransomware.
- Very like LUCR-1 (GUI-Vil), LUCR-3 tooling, particularly in Cloud, SaaS, and CI/CD, principally makes use of internet browsers and a few GUI utilities comparable to S3 Browser. Leveraging the native options of functions, similar to any worker would do, to hold out their purpose.
- LUCR-3 closely targets the IDPs for Preliminary Entry. Shopping for creds from widespread marketplaces and bypassing MFA through SIM swapping, social engineering, and push fatigue.
- LUCR-3 does its homework on its preliminary entry victims, selecting identities that can have elevated privileges and even guaranteeing they supply from related geolocation as their sufferer identities to keep away from inconceivable journey (geo disparity) alerts.
- LUCR-3 will make the most of the sufferer organizations software program deployment options, comparable to SCCM, to deploy specified software program to focus on programs.
Mission
LUCR-3 is a financially motivated risk actor that makes use of knowledge theft of delicate knowledge (IP, Buyer knowledge, Code Signing Certificates) to aim extortion. Whereas extortion calls for do differ, they’re usually within the tens of tens of millions of {dollars}. Some personas inside LUCR-3 will usually collaborate with ALPHV to hold out the extortion section of the assault.
Tooling
LUCR-3 makes use of principally Home windows 10 programs operating GUI utilities to hold out their mission within the cloud. Utilizing the native options of SaaS functions comparable to search, LUCR-3 is ready to navigate via a company with out elevating any alarms. In AWS, the risk actor routinely leverages the S3 Browser (model 10.9.9) and the AWS administration console (through an internet browser). LUCR-3 makes use of AWS Cloudshell throughout the AWS administration console to hold out any exercise that requires direct interplay with the AWS API.
Victimology
LUCR-3 usually targets giant (Fortune 2000) organizations which have Mental Property (IP) that’s priceless sufficient that sufferer organizations are more likely to pay an extortion payment. Software program corporations are a standard goal as they purpose to extort a payment associated to the theft of supply code in addition to code signing certificates. LUCR-3 will usually goal organizations that may be leveraged in a provide chain assault in opposition to others. Id Suppliers and their outsourced companies corporations are incessantly focused as a singular compromise of considered one of these entities will enable for entry into a number of different organizations. In latest months, LUCR-3 has expanded its concentrating on into sectors they have not beforehand centered as a lot on, comparable to hospitality, gaming, and retail.
Attacker Lifecycle
 |
| AWS Attacker Lifecycle |
Preliminary Recon
LUCR-3 does their homework when deciding on their goal sufferer identities. They guarantee they’re concentrating on customers that can have the entry they should perform their mission. This contains however is just not restricted to Id Admins, Builders, Engineers, and the Safety group.
They’ve been identified to leverage credentials that have been accessible in widespread deep internet marketplaces.
Preliminary Entry (IA)
LUCR-3’s preliminary entry into an setting is gained via compromised credentials. They don’t seem to be performing noisy actions like password spraying to search out passwords. Once they join, they have already got a reputable password to make use of. The standard method for them is:
1. Establish credentials for the meant sufferer id
- Purchase credentials from widespread deepweb marketplaces
- Smishing victims to gather their credentials
- Social engineering assist desk personnel to realize entry to the credentials
2. Bypass Multi-factor Authentication (MFA)
- SIM Swapping (when SMS OTP is enabled)
- Push Fatigue (when SMS OTP is just not enabled)
- Phishing assaults with redirects to reputable websites the place OTP codes are captured and replayed
- Purchase or social engineer entry from an insider (final resort)
3. Modify MFA settings
- Register a brand new machine
- Add different MFA choices
When LUCR-3 modifies MFA settings, they usually register their very own cellular machine and add secondary MFA choices comparable to emails. Alerts to observe for listed below are:
- When a person registers a tool that’s in a unique ecosystem than their earlier machine (Android to Apple for example)
- When a person registers a brand new machine that’s an older mannequin than their earlier machine
- When a single cellphone (machine ID) is assigned to a number of identities
- When an exterior e mail is added as a multi-factor choice
Recon (R)
R-SaaS
To be able to perform their purpose of knowledge theft, ransom, and extortion, LUCR-3 should perceive the place the necessary knowledge is and methods to get to it. They carry out these duties very like any worker would. Looking out via and viewing paperwork in numerous SaaS functions like SharePoint, OneDrive, data functions, ticketing options, and chat functions permits LUCR-3 to find out about an setting utilizing native functions with out setting off alarm bells. LUCR-3 makes use of search phrases focused at discovering credentials, studying in regards to the software program deployment environments, code signing course of, and delicate knowledge.
R-AWS
In AWS, LUCR-3 performs recon in a number of methods. They are going to merely navigate across the AWS Administration Console into companies like Billing, to grasp what kinds of companies are being leveraged, after which navigate every of these companies within the console. Moreover, LUCR-3 needs to know what packages are operating on the compute programs (EC2 cases) in a company. Leveraging Techniques Supervisor (SSM), LUCR-3 will run the native AWS-GatherSoftwareInventory job in opposition to all EC2 cases, returning the software program operating on the EC2 cases. Lastly, LUCR-3 will leverage the GUI utility S3 Browser together with a long-lived entry key to view accessible S3 buckets.
Privilege Escalation (PE)
LUCR-3 usually chooses preliminary victims who’ve the kind of entry crucial to hold out their mission. They don’t at all times have to make the most of privilege escalation strategies, however we have now noticed them accomplish that every now and then in AWS environments.
PE-AWS
LUCR-3 has utilized three (3) essential strategies for privilege escalation in AWS:
- Coverage manipulation: LUCR-3 has been seen modifying the coverage of current roles assigned to EC2 cases ( ReplaceIamInstanceProfileAssociation ) in addition to creating new ones with a full open coverage.
- UpdateLoginProfile: LUCR-3 will replace the login profile and, every now and then, create one if it would not exist to assign a password to an id to allow them to leverage it for AWS Administration Console logons.
- SecretsManager Harvesting: Many organizations retailer credentials in SecretsManger or Terraform Vault for programmatic entry from their cloud infrastructure. LUCR-3 will leverage AWS CloudShell to scrape all credentials which are accessible in SecretsManager and related options.
Set up Persistence/ Preserve Presence (EP)
LUCR-3, like most attackers, needs to make sure that they’ve a number of methods to enter an setting within the occasion that their preliminary compromised identities are found. In a contemporary cloud world, there are various methods to attain this purpose, and LUCR-3 employs a myriad to take care of its presence.
EP-AzureAD/Okta
After having access to an id within the IDP (AzureAD, Okta, and so on.), LUCR-3 needs to make sure they’ll simply proceed to entry the id. So as to take action, they are going to usually carry out the next actions:
- Reset/Register Issue: LUCR-3 will register their very own machine to ease their capacity for continued entry. As talked about beforehand, look ahead to ecosystem switches for customers in addition to single gadgets which are registered to a number of customers.
- Alternate MFA: Many IDPs enable for alternate MFA choices. LUCR-3 will make the most of these options to register exterior emails as an element. They’re good about selecting a reputation that aligns with the sufferer’s id.
- Robust Authentication Kind: In environments the place the default setting is to not enable for SMS as an element, LUCR-3 will modify this setting if they’re able to. In AzureAD, you possibly can monitor for this by searching for the StrongAuthenticationMethod altering from a 6 (PhoneAppOTP) to a 7 (OneWaySMS)
EP-AWS
To keep up persistence in AWS, LUCR-3 has been noticed performing the next:
- CreateUser: LUCR-3 will try to create IAM Customers when accessible. They select names that align with the sufferer id they’re utilizing for preliminary entry into the setting.
- CreateAccessKey: LUCR-3 will try to create entry keys for newly created IAM Customers in addition to current IAM Customers that they’ll then use programmatically. Like GUI-Vil (LUCR-1), the entry keys which are created are sometimes inputted into the S3 Browser to work together with S3 buckets.
- CreateLoginProfile / UpdateLoginProfile: LUCR-3, when attempting to be extra stealthy or when they don’t have entry to create new IAM customers, will try to create or replace login profiles for current customers. Login profiles are what assign a password to an IAM Person and permit for console entry. This system additionally lets the attacker achieve the privileges of the sufferer’s id.
- Credential Harvesting: As talked about beforehand, LUCR-3 finds nice worth in harvesting credentials from credential vaults comparable to AWS SecretsManager and Terraform Vault. These usually retailer credentials not only for the sufferer organizations but in addition credentials which will enable entry to enterprise companions, expertise integrations, and even shoppers of the sufferer group.
- Useful resource Creation: Lastly, LUCR-3 will create or take over current assets, comparable to EC2 cases that may be leveraged for entry again into the setting in addition to a staging space for instruments and knowledge theft as wanted.
EP-SaaS
LUCR-3 will use all of the functions accessible to them to additional their purpose. In ticketing programs, chat packages, doc shops, and data functions, they are going to usually carry out searches searching for credentials that may be leveraged throughout their assault.
Moreover, many of those functions enable the creation of entry tokens that can be utilized to work together with the SaaS functions API.
EP-CI/CD
LUCR-3 will even generate entry tokens for interacting with the APIs of your code repositories, comparable to GitHub and GitLab.
Protection Evasion (DE)
We’ve noticed that LUCR-3 considerably focuses on protection evasion ways in numerous environments. That is clearly to keep away from detection so long as potential till they’re certain they’ve achieved their mission targets and are able to carry out ransom and extortion actions. They accomplish this via a number of means relying on the kind of setting they’re in.
DE-AWS
LUCR-3 employs principally widespread protection evasion strategies in AWS, with a few distinctive flares.
- Disable GuardDuty: LUCR-3 will carry out the standard deletion of GuardDuty detectors but in addition tries to make it more durable so as to add again to the org degree by deleting invites. That is completed via the next three instructions: DisassociateFromMasterAccount, DeleteInvitations, DeleteDetector
- Cease Logging: LUCR-3 additionally makes an attempt to evade AWS detections by performing DeleteTrail and StopLogging actions.
- Serial Console Entry: This can be giving LUCR-3 an excessive amount of credit score, however we have now noticed them EnableSerialConsoleAccess for AWS accounts they’ve compromised after which try to make use of EC2 Occasion Hook up with SendSerialConsoleSSHPublicKey which can try to ascertain a serial connection to a specified EC2 occasion. This may be leveraged to keep away from community monitoring, as serial connections are hardware-based.
DE-AzureAD/Okta
LUCR-3 clearly understands that one of many extra widespread detections in place for IDPs is to observe and alert on inconceivable journey. To keep away from these inconceivable journey detections, LUCR-3 will make sure that they supply from the same geolocation as their sufferer id. This appears to be principally completed through using residential VPNs.
DE-M365/Google Workspace
A few of LUCR-3’s actions in an setting, comparable to producing tokens and opening up assist desk tickets, trigger emails to be despatched to the victims’ mailboxes. LUCR-3, already sitting in these mailboxes, will delete the emails to keep away from detection. Whereas e mail deletion by itself is a really weak sign, searching for e mail deletions through the net model of Outlook with delicate phrases like OAuth, entry token, and MFA would possibly convey to mild increased constancy indicators to observe.
Full Mission (CM)
LUCR-3 has one purpose: monetary achieve. They do that principally via extortion of delicate knowledge that they’ve collected through the native instruments of the sufferer organizations’ SaaS and CI/CD functions. In AWS, that is completed by knowledge theft in S3 and in database functions comparable to Dynamo and RDS.
Whereas within the SaaS world, they full their mission by looking and downloading paperwork and internet pages through a standard internet browser.
On the CI/CD aspect, LUCR-3 will use the clone, archive, and look at uncooked options of Github and Gitlab to view and obtain supply knowledge.
Indicators
Detections
Permiso shoppers are protected by the next detections:





