Readers assist help Home windows Report. We could get a fee in case you purchase by way of our hyperlinks.
Learn our disclosure web page to seek out out how will you assist Home windows Report maintain the editorial staff. Learn extra
After we’ve simply realized a couple of huge botnet assault concentrating on Microsoft 365 customers, we’ve received one other unhealthy information. A brand new approach has been uncovered that permits cybercriminals to slide previous Microsoft Outlook’s spam filters, delivering harmful ISO information straight to folks’s inboxes. In case your group makes use of the native Outlook spam filters, you could be vulnerable to falling sufferer to classy phishing assaults.
The trick entails hiding malicious hyperlinks behind what seem like innocent URLs. By utilizing a hyperlink obfuscation methodology, attackers can ship disk picture information containing malware immediately into victims’ electronic mail inboxes with out triggering any alarms.
In accordance with a report from Afine, security consultants are warning that this method weakens electronic mail security, particularly for firms that rely closely on Outlook’s built-in spam filtering. It’s like sneaking by way of the entrance door as a substitute of attempting to interrupt in by way of the home windows.
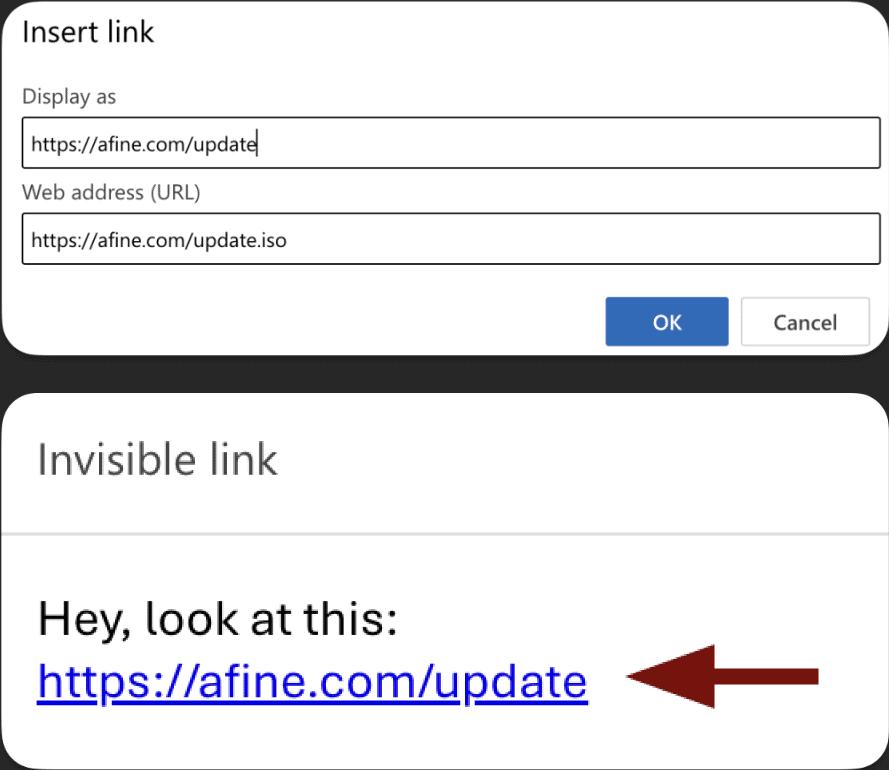
This discovery comes on the heels of stories exhibiting how attackers have additionally used ISO information to bypass Microsoft Defender SmartScreen, a software designed to cease untrusted packages from operating. In earlier campaigns, unhealthy actors relied on social engineering ways—tricking customers into manually extracting and operating malware from downloaded ISO information.
However now, the sport has modified. The brand new methodology focuses on evading email-level defenses solely, that means these dangerous information can land in customers’ main inboxes with out being detected.
ISO information stay a favourite software for attackers as a result of they usually fly beneath the radar of conventional security programs. Not like executable (.exe) information, which usually tend to elevate crimson flags, disk photographs aren’t routinely seen as suspicious. This makes it simpler for hackers to cover scripts, ransomware, or adware inside them, turning what appears to be like like an harmless file into a possible menace.
Nevertheless, we remind you that as with every different phishing assault, this one additionally wants your enter. You really should click on on the modified hyperlink to get the malicious ISO and infect your system. Subsequently, as all the time, we suggest to all the time be on alert about suspicious emails, even when the spam filters fail to flag them. We’ve realized about this from GBhackers.
His abrupt curiosity in computer systems began when he noticed the primary Dwelling Pc as a child. Nevertheless, his ardour for Home windows and all the pieces associated turned apparent when he turned a sys admin in a pc science highschool.
With 14 years of expertise in writing about all the pieces there’s to learn about science and expertise, Claudiu additionally likes rock music, chilling within the backyard, and Star Wars. Could the power be with you, all the time!




