Final week when a security researcher mentioned he might simply acquire the exact location from any one of many hundreds of thousands of customers of a extensively used phone-tracking app, we needed to see it for ourselves.
Eric Daigle, a pc science and economics pupil on the College of British Columbia in Vancouver, discovered the vulnerabilities within the monitoring app iSharing as a part of an investigation into the security of location-tracking apps. iSharing is among the extra fashionable location monitoring apps, claiming greater than 35 million customers so far.
Daigle mentioned the bugs allowed anybody utilizing the app to entry anybody else’s coordinates, even when the consumer wasn’t actively sharing their location information with anyone else. The bugs additionally uncovered the consumer’s title, profile photograph, and the e-mail deal with and cellphone quantity used to log in to the app.
The bugs meant that iSharing’s servers weren’t correctly checking that app customers had been solely allowed to entry their location information or another person’s location information shared with them.
Location monitoring apps — together with stealthy “stalkerware” apps — have a historical past of security mishaps that threat leaking or exposing customers’ exact location.
On this case, it took Daigle just a few seconds to find this reporter down to a couple ft. Utilizing an Android cellphone with the iSharing app put in and a brand new consumer account, we requested the researcher if he might pull our exact location utilizing the bugs.
“770 Broadway in Manhattan?” Daigle responded, together with the exact coordinates of reports.killnetswitch’s workplace in New York from the place the cellphone was pinging out its location.
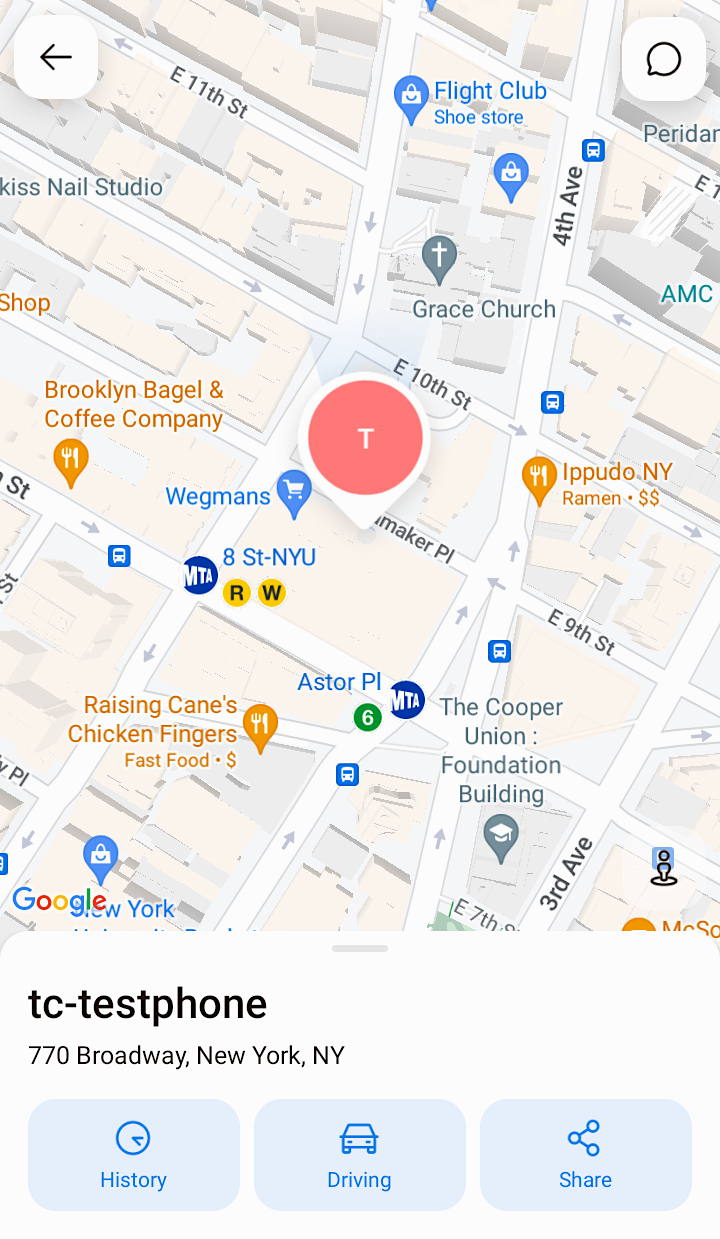
The security researcher pulled our exact location information from iSharing’s servers, regardless that the app was not sharing our location with anyone else. Picture Credit: information.killnetswitch (screenshot)
Daigle shared particulars of the vulnerability with iSharing some two weeks earlier however had not heard something again. That’s when Daigle requested information.killnetswitch for assist in contacting the app makers. iSharing fastened the bugs quickly after or through the weekend of April 20-21.
iSharing blamed the vulnerability on a characteristic it calls teams, which permits customers to share their location with different customers. Chuh advised information.killnetswitch that the corporate’s logs confirmed there was no proof that the bugs had been discovered previous to Daigle’s discovery. Chuh conceded that there “might have been oversight on our finish,” as a result of its servers had been failing to examine if customers had been allowed to hitch a bunch of different customers.
information.killnetswitch held the publication of this story till Daigle confirmed the repair.
“Discovering the preliminary flaw in whole was in all probability an hour or so from opening the app, determining the type of the requests, and seeing that creating a bunch on one other consumer and becoming a member of it labored,” Daigle advised information.killnetswitch.
From there, he spent just a few extra hours constructing a proof-of-concept script to display the security bug.
Daigle, who described the vulnerabilities in additional element on his weblog, mentioned he plans to proceed analysis within the stalkerware and location-tracking space.
Learn extra on information.killnetswitch:
To contact this reporter, get in contact on Sign and WhatsApp at +1 646-755-8849, or by e-mail. You can even ship information and paperwork by way of SecureDrop.



