This new product gives SaaS discovery and danger evaluation coupled with a free consumer entry assessment in a novel “freemium” mannequin
Securing staff’ SaaS utilization is turning into more and more essential for many cloud-based organizations. Whereas quite a few instruments can be found to handle this want, they usually make use of completely different approaches and applied sciences, resulting in pointless confusion and complexity. Enter Wing Safety’s new “Important SSPM” (SaaS Safety Posture Administration) software, which goals to simplify the method of securing SaaS utilization throughout the group. Its enterprise strategy is straightforward: self-onboard, strive the product, and if impressed, improve to unlock extra very important security capabilities.
What’s important SaaS security?
In line with Wing, three primary but basic capabilities are obligatory for organizations aiming to safe their SaaS: discovery, evaluation, and management. These align with regulatory security requirements equivalent to ISO 27001 and SOC, which emphasize vendor and third-party danger evaluation applications, in addition to controlling consumer entry to important enterprise instruments.
1. Uncover: You’ll be able to’t safe what you possibly can’t see
Shadow IT shouldn’t be a novel situation however relatively an evolving one. With the continual enhance in SaaS utilization and the flexibility for customers to bypass security insurance policies like MFA and SSO when onboarding SaaS functions, the brand new face of shadow IT is SaaS-based. The method is straightforward: staff want to finish a enterprise job and infrequently require a software to facilitate it. They seek for an answer on-line, utilizing firm credentials to log in, significantly when most providers do not require bank card data to get began. SaaS, being the fashionable provide chain, clearly requires a security answer on account of its decentralized and ungoverned nature.
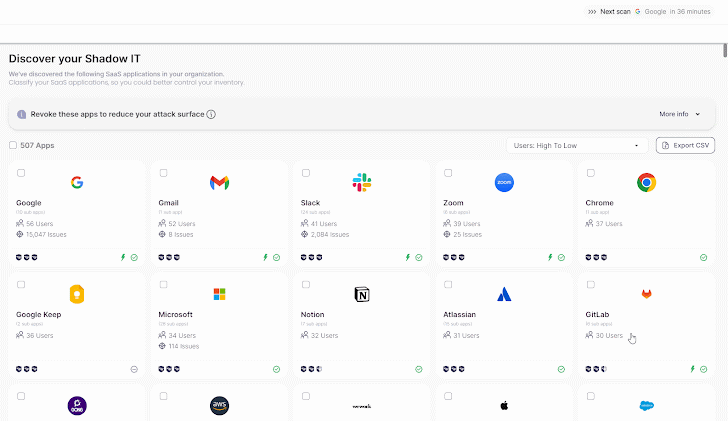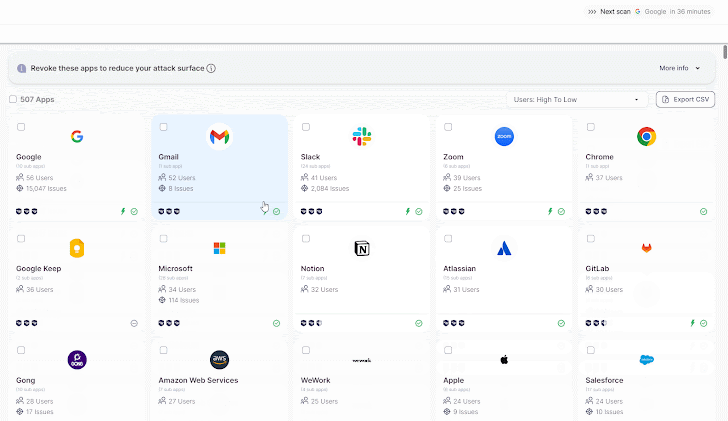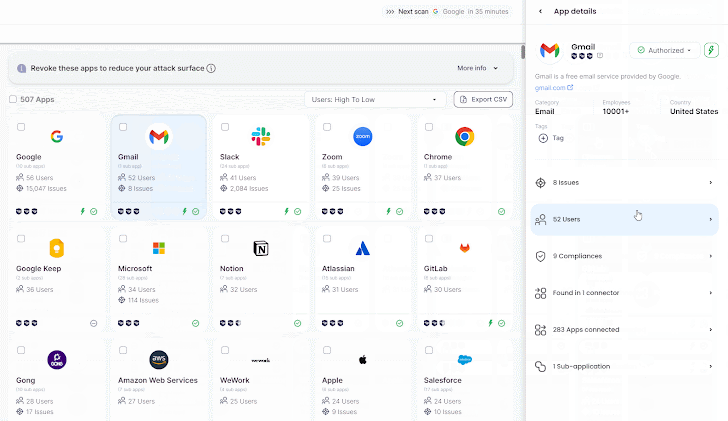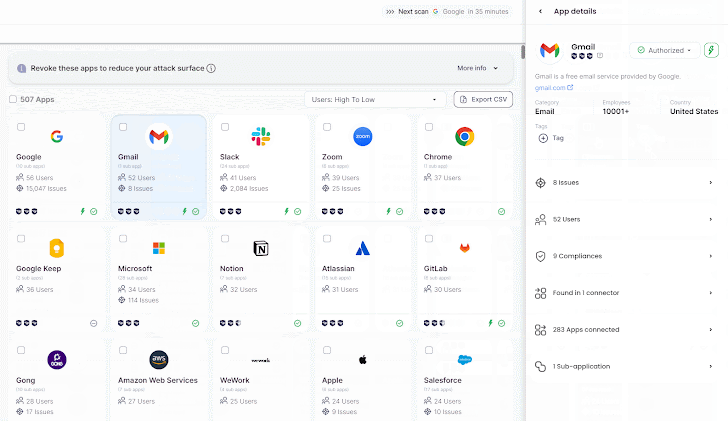 |
| Wing’s SaaS discovery |
2. Assess danger: Not all dangers are equal, save useful time
As soon as the shadow aspect is resolved, organizations are left with an intensive record of functions, usually numbering within the 1000’s. This begs the query: what now? With out an automatic methodology for evaluating the dangers related to all of the SaaS functions linked to the group, uncovering shadow SaaS could be extra complicated and burdensome than useful. This highlights the significance of assessing the security standing of those functions and figuring out a threshold that requires consideration.
SaaS discovery should go hand in hand with some extent of vendor or third-party danger evaluation. Wing’s new product tier combines SaaS discovery with an automatic processes for figuring out an utility’s SaaS security rating. This danger data is extracted from an unlimited SaaS database of over 280,000 SaaS on file, cross-checked with the info from lots of of Wing’s customers and their SaaS environments. Paying prospects profit from broader and deeper SaaS danger assessments, together with near-real-time menace intelligence alerts.
3. Management: Guarantee customers solely have obligatory entry
Discovering all SaaS in use (and never in use) and understanding their dangers is barely half the battle; the opposite half entails SaaS customers. They grant functions entry and permissions to firm information, making selections relating to learn/write permissions for the quite a few functions they use. On common, every worker makes use of 28 SaaS functions at any given time, which interprets to lots of, if not 1000’s, of SaaS functions with entry to firm information.
Conducting periodic consumer entry opinions throughout important enterprise functions isn’t just a regulatory requirement but additionally extremely really helpful for sustaining a safe posture. Controlling who has entry to which utility can stop delicate information from falling into the mistaken arms and considerably cut back the potential assault floor, as staff are sometimes the primary targets for malicious actors. An extended record of customers and their permissions and roles throughout varied functions could be overwhelming, which is why Wing aids in prioritizing customers based mostly on their permissions, their roles and by encouraging the least privilege idea. This ensures that every one customers, besides accredited admins, have solely primary entry to SaaS functions.
 |
| Wing’s Consumer Entry Assessment |
In abstract – These three capabilities are important for beginning a correct SaaS security program, however they do not assure full protection or management. Mature security organizations would require extra. Data security options, automated remediation paths and extra management over consumer privileges and behaviors are solely potential with Wing’s full answer. That mentioned, these are an essential place to begin for these organizations who do not but have SaaS security in place or are considering which instruments and approaches to get began with.
How is that this completely different from a POC or interactive demo?
This new “strive first, pay later” strategy differs from the typical POC primarily in its utterly no-touch nature. Customers can self-onboard the product by agreeing to Wing’s authorized situations, with out the necessity to work together with a human consultant or gross sales personnel, except they select to. Whereas the free product is deliberately restricted in options and capabilities, it offers a place to begin for these inquisitive about or in search of SaaS security. In contrast to on-line demos, this course of entails the precise processing of your information and may genuinely improve your security posture by offering visibility into your organization’s actual SaaS utilization and by permitting you to judge the magnitude of your SaaS assault floor. A freemium strategy in security-related merchandise is unusual, making this a chance for many who want to take a look at the product earlier than committing.




