After Sandworm and APT28 (referred to as Fancy Bear), one other state-sponsored Russian hacker group, APT29, is leveraging the CVE-2023-38831 vulnerability in WinRAR for cyberattacks.
APT29 is tracked underneath totally different names (UNC3524,/NobleBaron/Darkish Halo/NOBELIUM/Cozy Bear/CozyDuke, SolarStorm) and has been concentrating on embassy entities with a BMW automobile sale lure.
The CVE-2023-38831 security flaw impacts WinRAR variations earlier than 6.23 and permits crafting .RAR and .ZIP archives that may execute within the background code ready by the attacker for malicious functions.
The vulnerability has been exploited as a zero-day since April by menace actors concentrating on cryptocurrency and inventory buying and selling boards.
Ngrok static area for canopy comms
In a report this week, the Ukrainian Nationwide Safety and Protection Council (NDSC) says that APT29 has been utilizing a malicious ZIP archive that runs a script within the background to indicate a PDF lure and to obtain PowerShell code that downloads and executes a payload.
The malicious archive is known as “DIPLOMATIC-CAR-FOR-SALE-BMW.pdf” and focused a number of nations on the European continent, together with Azerbaijan, Greece, Romania, and Italy.
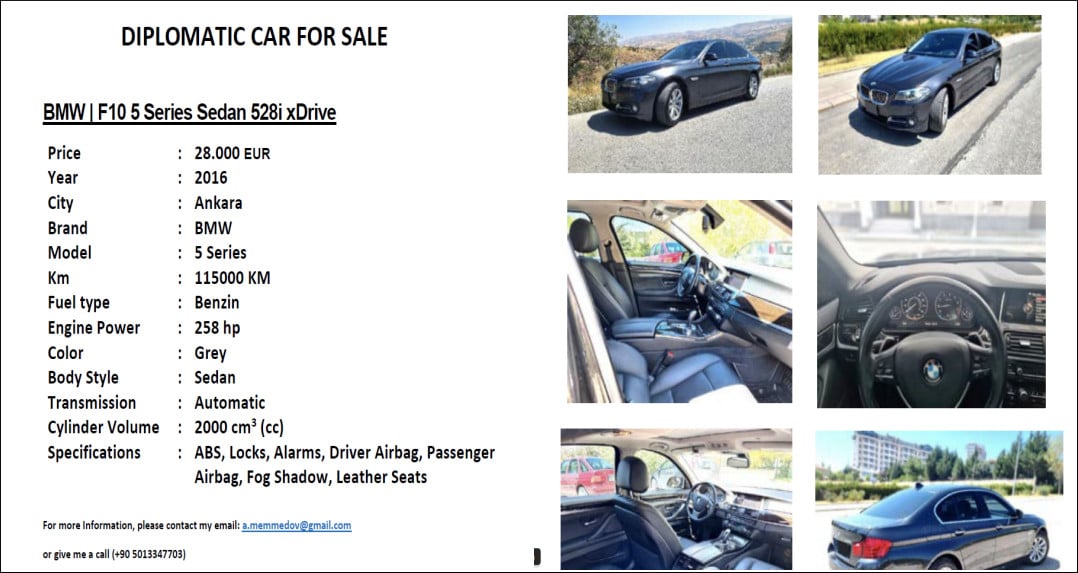
supply: Ukrainian Nationwide Safety and Protection Council
APT29 has used the BMW automobile advert phishing lure earlier than to goal diplomats in Ukraine throughout a marketing campaign in Might that delivered ISO payloads by the HTML smuggling approach.
In these assaults, the Ukrainian NDSC says that APT29 mixed the outdated phishing tactic with a novel approach to allow communication with the malicious server.
NDSC says that the Russian hackers used a Ngrok free static area (a brand new function Ngrok introduced on August 16) to entry the command and management (C2) server hosted on their Ngrok occasion.
“On this nefarious tactic, they make the most of Ngrok’s companies by using free static domains offered by Ngrok, sometimes within the type of a subdomain underneath “ngrok-free.app.” These subdomains act as discrete and inconspicuous rendezvous factors for his or her malicious payloads” – Nationwide Safety and Protection Council of Ukraine
By utilizing this methodology, the attackers managed to cover their exercise and talk with compromised methods with out being the danger of being detected.
Since researchers at cybersecurity firm Group-IB reported that the CVE-2023-38831 vulnerability in WinRAR was exploited as a zero-day, superior menace actors began to include it into their assaults.
Safety researchers at ESET noticed assaults in August attributed to the Russian APT28 hacker group that exploited the vulnerability in a spearphishing marketing campaign that focused political entities within the EU and Ukraine utilizing the European Parliament agenda as a lure.
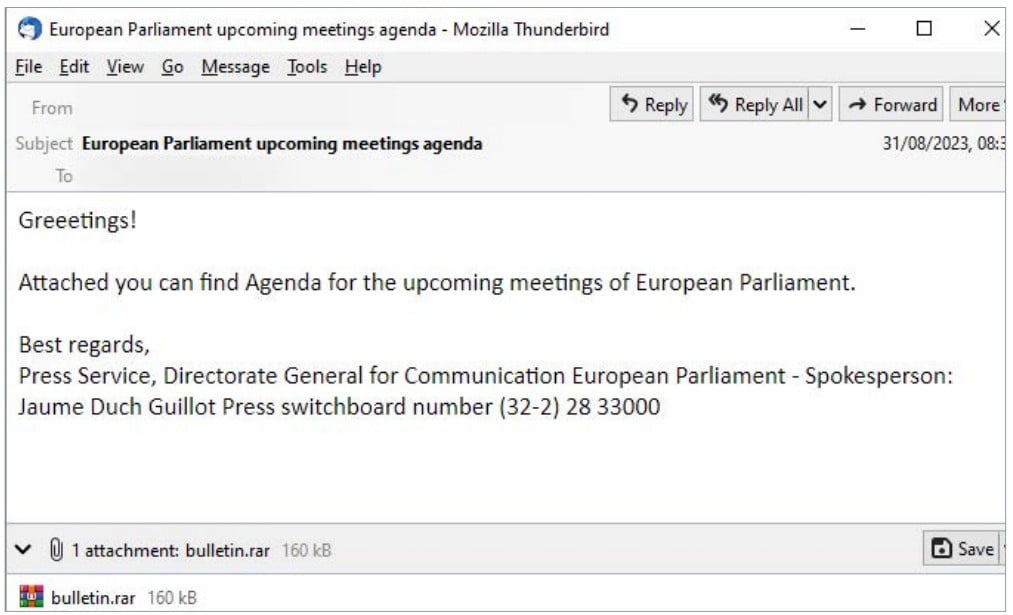
supply: ESET
A report from Google in October notes that the security difficulty was exploited by Russian and Chinese language state hackers to steal credentials and different delicate information, in addition to to determine persistence on course methods.
The Ukrainian NDSC says that the noticed marketing campaign from APT29 stands out as a result of it mixes outdated and new methods corresponding to using the WinRAR vulnerability to ship payloads and Ngrok companies to cover communication with the C2.
The report from the Ukrainian company offers a set of indicators of compromise (IoCs) consisting of filenames and corresponding hashes for PowerShell scripts and an electronic mail file, together with domains and electronic mail addresses.




