Russian menace actors have been probably linked to what’s been described because the “largest cyber assault towards Danish important infrastructure,” during which 22 firms related to the operation of the nation’s vitality sector had been focused in Could 2023.
“22 simultaneous, profitable cyberattacks towards Danish important infrastructure will not be commonplace,” Denmark’s SektorCERT mentioned [PDF]. “The attackers knew upfront who they had been going to focus on and obtained it proper each time. Not as soon as did a shot miss the goal.”
The company mentioned it discovered proof connecting a number of assaults to Russia’s GRU army intelligence company, which can also be tracked beneath the title Sandworm and has a observe file of orchestrating disruptive cyber assaults on industrial management methods. This evaluation relies on artifacts speaking with IP addresses which have been traced to the hacking crew.
The unprecedented and coordinated cyber assaults befell on Could 11 by exploiting CVE-2023-28771 (CVSS rating: 9.8), a important command injection flaw impacting Zyxel firewalls that was disclosed in late April 2023.
On the 11 firms that had been efficiently infiltrated, the menace actors executed malicious code to conduct reconnaissance of the firewall configurations and decide the subsequent plan of action.
“This type of coordination requires planning and sources,” SektorCERT mentioned in an in depth timeline of occasions. “The benefit of attacking concurrently is that the details about one assault can’t unfold to the opposite targets earlier than it’s too late.”
“This places the facility of data sharing out of play as a result of nobody could be warned upfront in regards to the ongoing assault since everyone seems to be attacked on the similar time. It’s uncommon – and intensely efficient.”
A second wave of assaults focusing on extra organizations was subsequently recorded from Could 22 to 25 by an assault group with beforehand unseen cyber weapons, elevating the chance that two completely different menace actors had been concerned within the marketing campaign.
That mentioned, it is presently unclear if the teams collaborated with one another, labored for a similar employer, or had been performing independently.
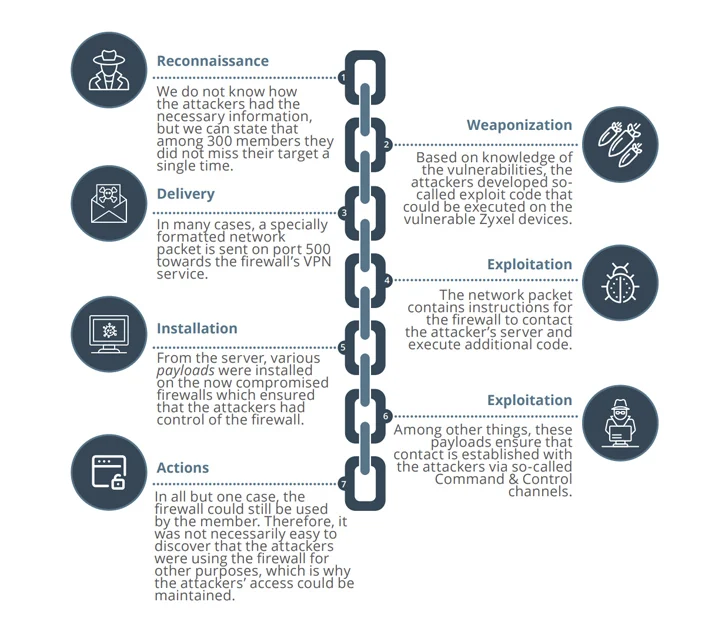
These assaults are suspected to have weaponized two extra important bugs in Zyxel gear (CVE-2023-33009 and CVE-2023-33010, CVSS scores: 9.8) as zero-days to co-opt the firewalls into Mirai and MooBot botnets, provided that patches for them had been launched by the corporate on Could 24, 2023.
The compromised gadgets, in some circumstances, had been used to conduct distributed denial-of-service (DDoS) assaults towards unnamed firms within the U.S. and Hong Kong.
“After the exploit code for among the vulnerabilities grew to become publicly identified round 30/5, assault makes an attempt towards the Danish important infrastructure exploded – particularly from IP addresses in Poland and Ukraine,” SektorCERT defined.
The onslaught of assaults prompted the affected entities to disconnect from the web and go into island mode, the company additional added.
However it’s not solely nation-state actors. The vitality sector can also be more and more turning into a spotlight for ransomware teams, with preliminary entry brokers (IABs) actively selling unauthorized entry to nuclear vitality companies, in accordance with a report from Resecurity earlier this week.
The event comes as Censys found six hosts belonging to NTC Vulkan, a Moscow-based IT contractor that is alleged to have equipped offensive cyber instruments to Russian intelligence companies, together with Sandworm.
Moreover, the analysis uncovered a connection to a bunch referred to as Raccoon Safety through an NTC Vulkan certificates.
“Racoon Safety is a model of NTC Vulkan and that it’s doable that Raccoon Safety’s actions embody both earlier or present participation within the previously-mentioned leaked initiatives contracted by the GRU,” Matt Lembright, director of Federal Purposes at Censys, mentioned.




