A brand new large-scale botnet referred to as RondoDox is focusing on 56 vulnerabilities in additional than 30 distinct units, together with flaws first disclosed throughout Pwn2Own hacking competitions.
The attacker focuses on a variety of uncovered units, together with DVRs, NVRs, CCTV methods, and net servers and have been energetic since June.
The RondoDox botnet leverages what Development Micro researchers name an “exploit shotgun” technique, the place quite a few exploits are used concurrently to maximise the infections, even when the exercise may be very noisy.
Since FortiGuard Labs found RondoDox, the botnet seems to have expanded the listing of exploited vulnerabilities, which included CVE-2024-3721 and CVE-2024-12856.
Mass n-day exploitation
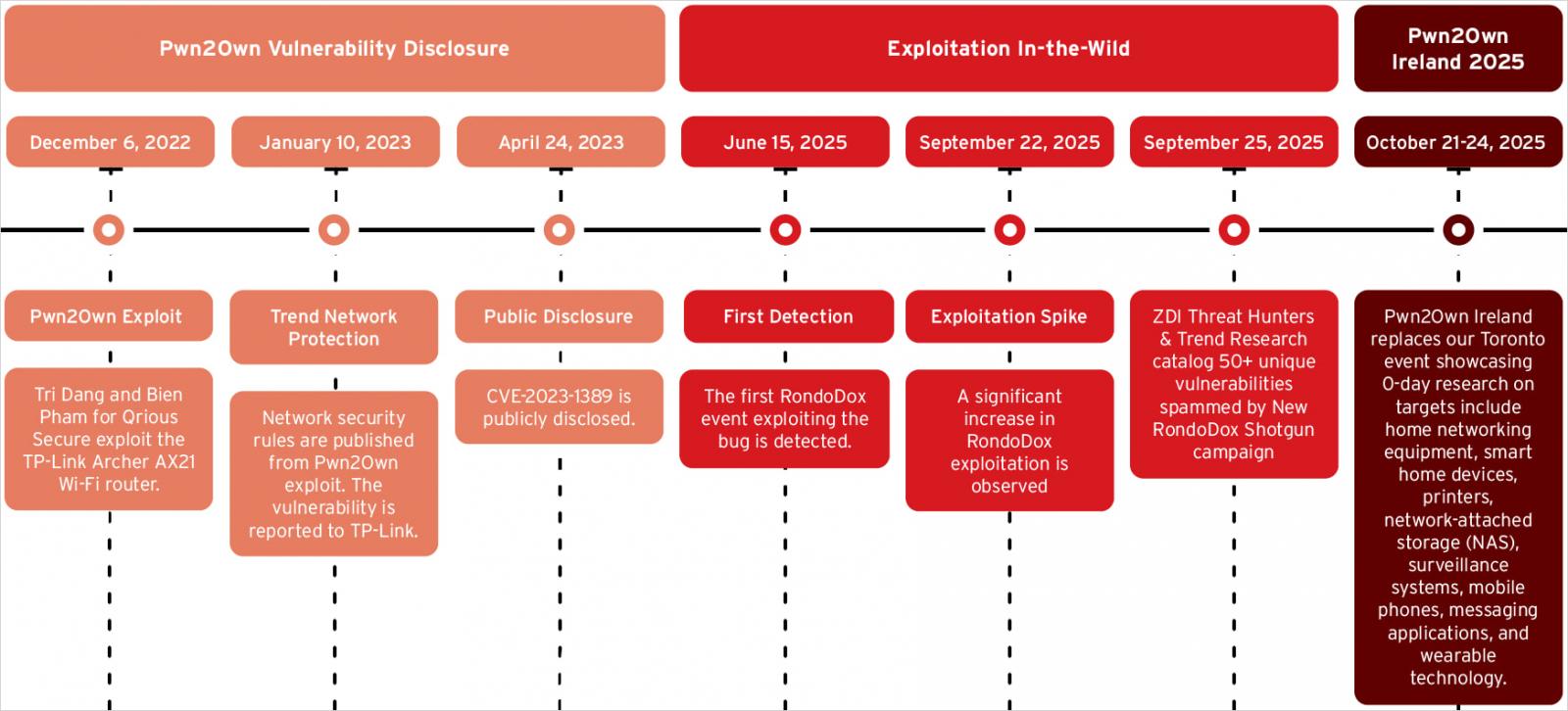
In a report in the present day, Development Micro says that RondoDox exploits CVE-2023-1389, a flaw within the TP-Hyperlink Archer AX21 Wi-Fi router that was initially demonstrated at Pwn2Own Toronto 2022.
Pwn2Own is a hacking competitors organized twice a 12 months by Development Micro’s Zero Day Initiative (ZDI), the place white-hat groups show exploits for zero-day vulnerabilities in extensively used merchandise.
Supply: Development Micro
The security researchers notice that the botnet developer pay shut consideration to exploits demonstrated throughout Pwn2Own occasions, and transfer rapidly to weaponize them, as Mirai did with CVE-2023-1389 in 2023.
Beneath is a listing of post-2023 n-day flaws RondoDox consists of in its arsenal:
- Digiever – CVE-2023-52163
- QNAP – CVE-2023-47565
- LB-LINK – CVE-2023-26801
- TRENDnet – CVE-2023-51833
- D-Hyperlink – CVE-2024-10914
- TBK – CVE-2024-3721
- 4-Religion – CVE-2024-12856
- Netgear – CVE-2024-12847
- AVTECH – CVE-2024-7029
- TOTOLINK – CVE-2024-1781
- Tenda – CVE-2025-7414
- TOTOLINK – CVE-2025-1829
- Meteobridge – CVE-2025-4008
- Edimax – CVE-2025-22905
- Linksys – CVE-2025-34037
- TOTOLINK – CVE-2025-5504
- TP-Hyperlink – CVE-2023-1389
Older flaws, particularly in units that reached finish of life, are a major danger as they’re extra more likely to stay unpatched. More moderen ones in supported {hardware} are equally harmful since many customers are likely to ignore firmware updates after organising the units.
Development Micro additionally discovered that RondoDox incorporates exploits for 18 command injection flaws that haven’t been assigned a vulnerability ID (CVE). They affect D-Hyperlink NAS items, TVT and LILIN DVRs, Fiberhome, ASMAX, and Linksys routers, Brickcom cameras, and different unidentified endpoints.
To guard towards RondoDox and different botnet assaults, apply the most recent out there firmware updates on your machine and substitute EoL gear. It is usually really helpful to phase your community to isolate important information from internet-facing IoTs, or from visitor connections, and substitute default credentials with safe passwords.
Be a part of the Breach and Attack Simulation Summit and expertise the way forward for security validation. Hear from prime specialists and see how AI-powered BAS is reworking breach and assault simulation.
Do not miss the occasion that may form the way forward for your security technique





