A hitherto undocumented menace actor working for almost a decade and codenamed MoustachedBouncer has been attributed to cyber espionage assaults geared toward international embassies in Belarus.
“Since 2020, MoustachedBouncer has most definitely been in a position to carry out adversary-in-the-middle (AitM) assaults on the ISP degree, inside Belarus, with a purpose to compromise its targets,” ESET security researcher Matthieu Faou mentioned, describing the group as expert and superior.
The adversary, energetic since at the least 2014, is assessed to be aligned with Belarusian pursuits, seemingly using a lawful interception system reminiscent of SORM to conduct its AitM assaults in addition to deploy disparate instruments referred to as NightClub and Disco.
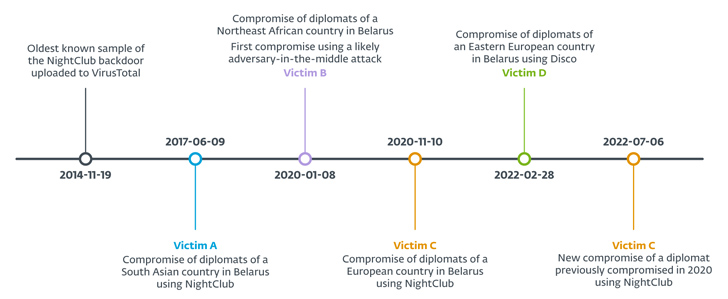
Each the Home windows malware frameworks assist extra spying plugins together with a screenshotter, an audio recorder, and a file stealer. The oldest pattern of NightClub dates again to November 19, 2014, when it was uploaded to VirusTotal from Ukraine.
Embassy workers from 4 totally different international locations have been focused since June 2017: two from Europe, one from South Asia, and one from Northeast Africa. One of many European diplomats was compromised twice in November 2020 and July 2022. The names of the international locations weren’t revealed.
MoustachedBouncer can also be believed to work carefully with one other superior persistent menace (APT) actor often known as Winter Vivern (aka TA473 or UAC-0114), which has a observe document of putting authorities officers in Europe and the U.S.
The precise preliminary an infection vector used to ship NightClub is presently unknown. The distribution of Disco, alternatively, is achieved by way of an AitM assault.
“To compromise their targets, MoustachedBouncer operators tamper with their victims’ web entry, in all probability on the ISP degree, to make Home windows imagine it is behind a captive portal,” Faou mentioned. “For IP ranges focused by MoustachedBouncer, the community visitors is tampered on the ISP degree, and the latter URL redirects to a seemingly respectable, however pretend, Home windows Replace URL.”
“Whereas the compromise of routers with a purpose to conduct AitM on embassy networks can’t be totally discarded, the presence of lawful interception capabilities in Belarus suggests the visitors mangling is going on on the ISP degree reasonably than on the targets’ routers,” Fou mentioned.
Two Belarusian web service suppliers (ISPs), viz Unitary Enterprise A1 and Beltelecom, are suspected to be concerned within the marketing campaign, per the Slovak cybersecurity firm.
Victims who land on the bogus web page are greeted with a message urging them to put in important security updates by clicking on a button. In doing so, a rogue Go-based “Home windows Replace” installer is downloaded to the machine that, when executed, units up a scheduled job to run one other downloader binary chargeable for fetching extra plugins.
The add-ons increase on Disco’s performance by capturing screenshots each 15 seconds, executing PowerShell scripts, and organising a reverse proxy.
A big side of the plugins is the usage of the Server Message Block (SMB) protocol for knowledge exfiltration to command-and-control servers which can be inaccessible over the web, making the menace actor’s infrastructure extremely resilient.
Additionally used within the January 2020 assault geared toward diplomats of a Northeast African nation in Belarus is a C# dropper known as SharpDisco, which facilitates the deployment of two plugins by way of a reverse shell with a purpose to enumerate related drives and exfiltrate recordsdata.
The NightClub framework additionally includes a dropper that, in flip, launches an orchestrator part to reap recordsdata of curiosity and transmit them over the Easy Mail Switch Protocol (SMTP). Subsequent iterations of NightClub unearthed in 2017 and 2020 additionally incorporate a keylogger, audio recorder, screenshotter, and a DNS-tunneling backdoor.
“The DNS-tunneling backdoor (ParametersParserer.dll) makes use of a customized protocol to ship and obtain knowledge from a malicious DNS server,” Faou defined. “The plugin provides the information to exfiltrate as a part of the subdomain identify of the area that’s used within the DNS request.”
The instructions supported by the modular implant enable the menace actor to seek for recordsdata matching a particular sample, learn, copy, and take away recordsdata, write to recordsdata, copy directories, and create arbitrary processes.
It is believed that NightClub is utilized in eventualities the place visitors interception on the ISP degree is not attainable due to anonymity-boosting mitigations reminiscent of the usage of an end-to-end encrypted VPN the place web visitors is routed exterior of Belarus.
“The principle takeaway is that organizations in international international locations the place the web can’t be trusted ought to use an end-to-end encrypted VPN tunnel to a trusted location for all their web visitors with a purpose to circumvent any community inspection units,” Faou mentioned.




