A security researcher has launched a partial proof of idea exploit for a vulnerability within the FortiWeb internet software firewall that enables a distant attacker to bypass authentication.
The flaw was reported responsibly to Fortinet and is now tracked as CVE-2025-52970. Fortinet launched a repair on August 12.
Safety researcher Aviv Y named the vulnerability FortMajeure and describes it as a “silent failure that wasn’t meant to occur.” Technically, it’s an out-of-bounds learn in FortiWeb’s cookie parsing that lets an attacker set the Period parameter to an sudden worth.
This causes the server to make use of an all-zero secret key for session encryption and HMAC signing, making solid authentication cookies trivial to create.
Exploitation ends in a full authentication bypass, letting the attacker impersonate any energetic person, together with an administrator.
To take advantage of CVE-2025-52970 efficiently, the goal person will need to have an energetic session through the assault, and the adversary should brute-force a small numeric discipline within the cookie.
The brute-forcing requirement comes from a discipline within the signed cookie that’s validated by the perform refresh_total_logins() (in libncfg.so).
This discipline is an unknown quantity that the attacker should guess, however the researcher notes that the vary is normally not above 30, makingg it a tiny search area of roughly 30 requests.
As a result of the exploit makes use of the all-zero key (as a result of Period bug), every guess may be examined immediately by checking if the solid cookie is accepted.
The difficulty impacts FortiWeb 7.0 to 7.6, and was mounted within the under variations:
- FortiWeb 7.6.4 and later
- FortiWeb 7.4.8 and later
- FortiWeb 7.2.11 and later
- FortiWeb 7.0.11 and later
Fortinet says within the bulletin that FortiWeb 8.0 releases aren’t impacted by this challenge, so there’s no motion that must be taken there.
The security bulletin lists no workarounds or mitigation recommendation, so upgrading to a protected model is the one beneficial efficient motion.
Fortinet’s CVSS severity rating of seven.7 may be misleading, because it derives from “excessive assault complexity” as a result of brute-forcing requirement. In follow although, the brute-forcing half is easy and fast to carry out.
The researcher shared a PoC output, displaying admin impersonation on a REST endpoint. Nevertheless, he withheld the whole exploit that additionally covers connecting to the FortiWeb CLI through /ws/cli/open.
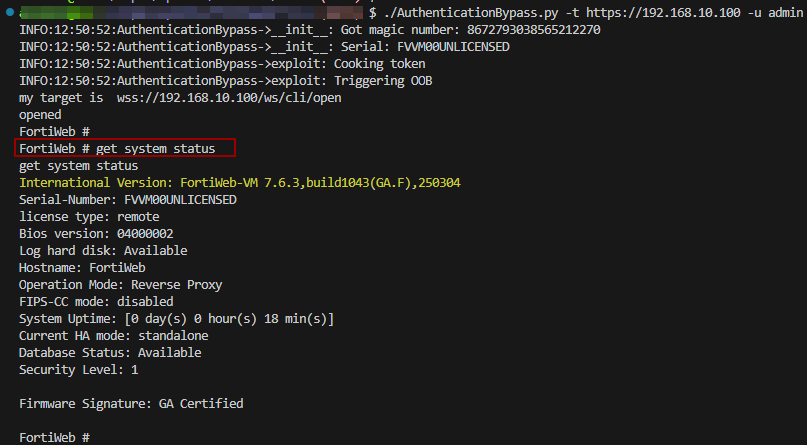
Supply: Aviv Y
Nevertheless, Aviv Y promised to publish the whole exploitation particulars later, as the seller’s advisory has been launched solely just lately. The researcher made this decistion to permit system directors extra time to use the repair.
The printed particulars reveal the core of the difficulty however aren’t sufficient even for educated attackers to deduce the remaining and develop a full weaponized chain, the researcher instructed BleepingComputer.
He defined that attackers must reverse engineer the format of the fields within the session, which is impractical provided that Fortinet has its personal information constructions.
Regardless of that, fast motion have to be taken to mitigate the difficulty as hackers observe these bulletins carefully and prepare to drag the set off when full PoCs are out.
Aviv Y instructed BleepingComputer he has not selected the date for publishing the exploit however plans to offer defenders time to answer the danger.

46% of environments had passwords cracked, practically doubling from 25% final 12 months.
Get the Picus Blue Report 2025 now for a complete take a look at extra findings on prevention, detection, and information exfiltration traits.




