Readers assist help Home windows Report. While you make a purchase order utilizing hyperlinks on our web site, we could earn an affiliate fee.
Learn the affiliate disclosure web page to search out out how are you going to assist Home windows Report effortlessly and with out spending any cash. Learn extra
Again in 2021, we reported about Distant Entry Trojans (RAT) malware assaults delivered by electronic mail phishing assaults and it looks like it’s occurring once more. This time, the attackers who appear to be Russian, set off different channels like Zoom, Skype and Google Meet.
From the Zscaler’s ThreatLabz security report, the menace actor spreads SpyNote RAT to Android customers and NjRAT and DCRat to Home windows customers.
The RAT is downloaded from pretend web sites
Based on the security agency examine, this example began in December 2023 and it’s ongoing so you actually must be cautious on what apps and recordsdata you obtain.
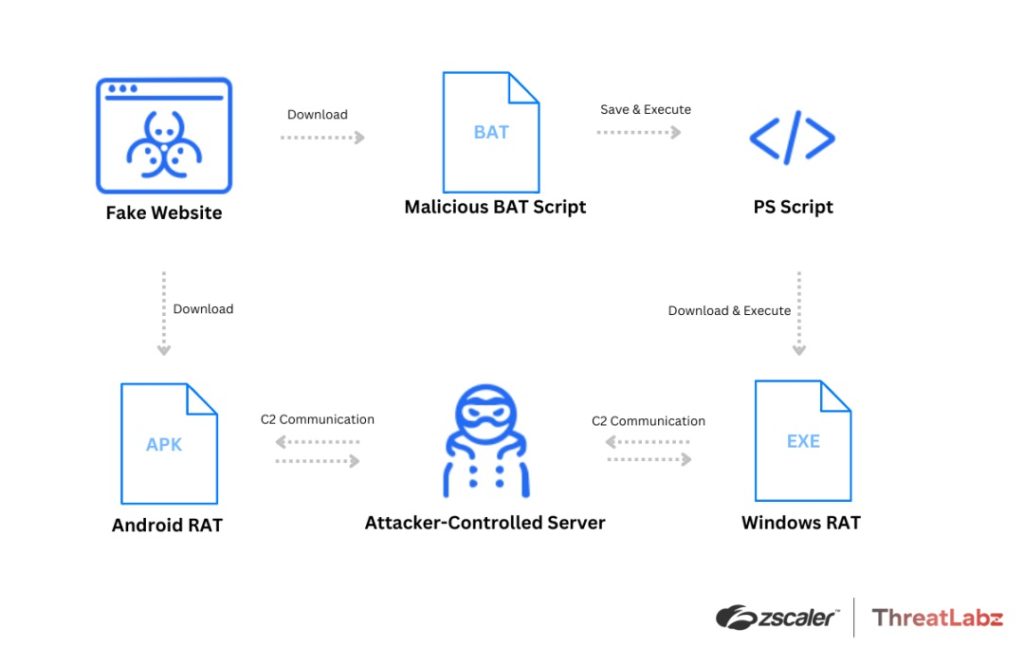
Zscaler’s diagram explains how the rip-off unfolds. All of it begins with visiting a pretend obtain web page for the aforementioned communication instruments. While you click on the obtain button for Android, you get a malicious APK, and if you click on the obtain for Home windows button, you get an contaminated BAT file.
In the event you execute the recordsdata in your telephone or PC, you ultimately obtain the RAT payload.
For example, the pretend join-skype[.]data web site was created in early December for Skype malicious obtain whereas the online-cloudmeeting[.]professional pretend web site is mimicking the Google Meet obtain web page.
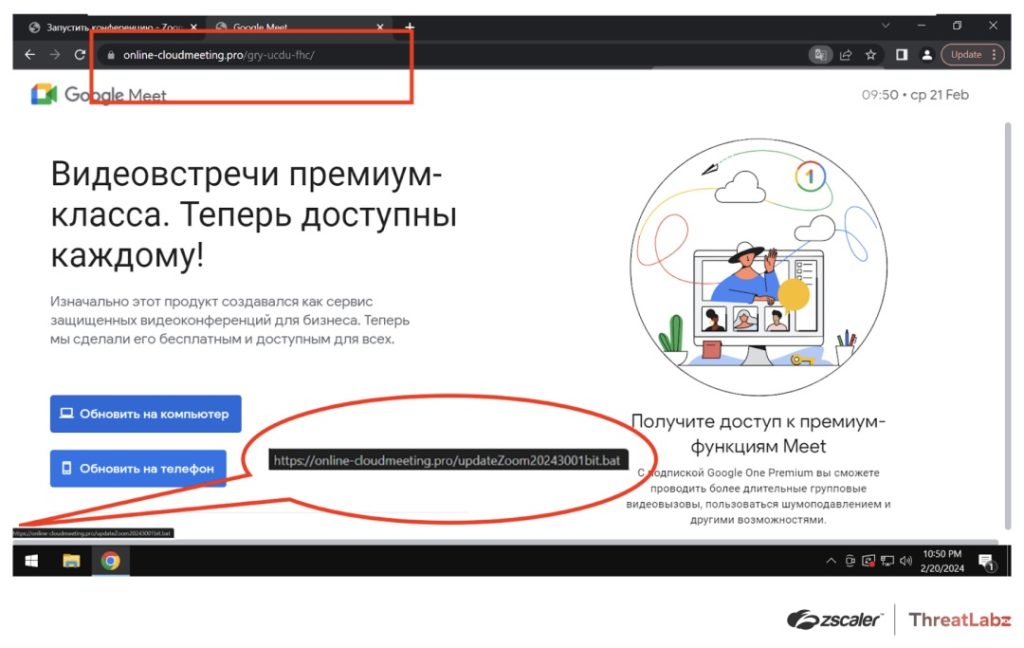
In the identical approach, if you happen to downloaded a file known as updateZoom20243001bit.bat to put in Zoom, your PC lastly acquired a malicious payload within the type of ZoomDirectUpdate.exe, a WinRAR archive that accommodates the DCRat payload.
What occurs if my system acquired contaminated with a RAT?
Finally, the malicious batch script will run a PowerShell script, which, in flip, downloads and executes the distant entry trojan.
That implies that the attacker can have entry to your system and can be capable to steal passwords, accounts, credential, presumably attending to your bank card information and steal cash out of your accounts.
As you see, it’s very harmful and it is best to examine the legitimacy of the web site you’re downloading an app from. We must also talk about how you bought to the pretend web site within the first place. Possibly you will have clicked on a hyperlink in a pretend electronic mail that appeared like coming from Zoom, Skype or Google Meet providing you advantages or promoting a false replace.
In case your system is already contaminated, use a robust antivirus or reset your system to manufacturing unit settings to take away the menace. In the event you didn’t obtain it but, be careful for the story tail indicators to find if the web site is actual or pretend and all the time use the unique supply to get the app you want.
Did you obtain any of the apps above currently? Inform us all about that within the feedback part under.




