Picture: Midjourney
Non-profit healthcare service supplier Group Well being Cooperative of South Central Wisconsin (GHC-SCW) has disclosed {that a} ransomware gang breached its community in January and stole paperwork containing the non-public and medical info of over 500,000 people.
Nevertheless, the attackers could not encrypt the compromised units, which allowed GHC-SCW to safe its methods with the assistance of exterior cyber incident response consultants and produce them again on-line after they have been remoted to comprise the breach.
“Within the early morning hours of January twenty fifth, 2024, GHC-SCW recognized unauthorized entry to their community. Their Info Expertise (IT) Division purposefully remoted and secured their community, inflicting a number of of their methods to be quickly unavailable,” the healthcare group mentioned in a press launch revealed on Tuesday.
“On February 9, 2024, throughout our investigation, we found indications that the attacker had copied a few of GHC-SCW’s information, which included protected well being info (PHI). Our discovery was confirmed when the attacker, a overseas ransomware gang, contacted GHC-SCW claiming accountability for the assault and stealing our information.”
Well being information stolen in the course of the January ransomware assault consists of affected people’ names, addresses, phone numbers, e-mail addresses, dates of start and/or deaths, social security numbers, member numbers, and Medicare and/or Medicaid numbers.
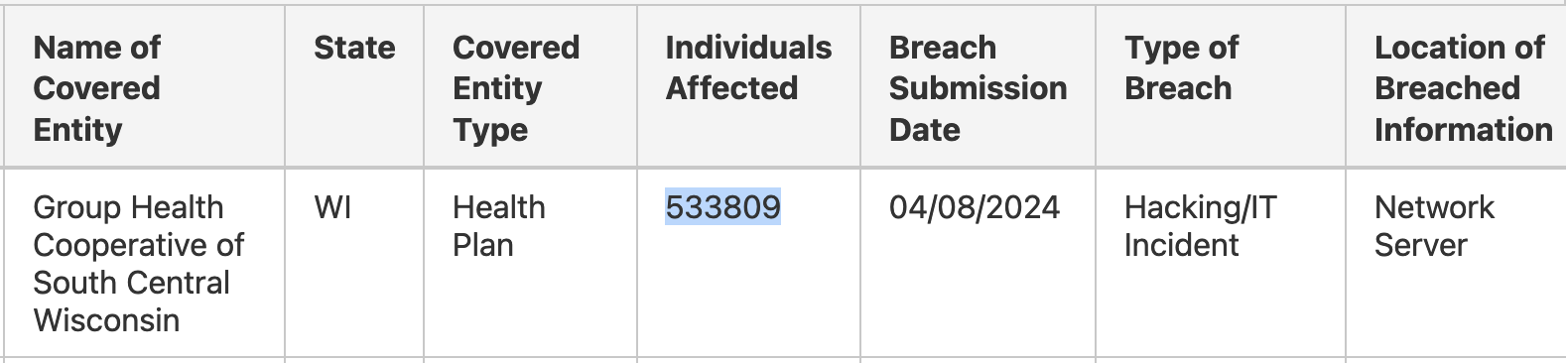
Though it did not present the precise variety of affected folks, extra info shared with the U.S. Division of Well being and Human Companies reveals that the data breach impacted 533,809 people.
In response to the incident, GHC-SCW says it took security measures to forestall such breaches from occurring once more, together with strengthening current controls, information backup, and person coaching.
Impacted people are suggested to observe all communications from healthcare suppliers, together with digital messages, billing statements, and different communications, and to report any suspicious exercise to GHC-SCW instantly.
GHC-SCW has but to seek out proof of the stolen info getting used for malicious functions.
Claimed by BlackSuit ransomware
Whereas the Wisconsin-based healthcare non-profit did not reveal the title of the menace group behind the January breach, the BlackSuit ransomware gang claimed the assault in March.
In line with the attackers’ claims, the stolen information additionally comprise affected sufferers’ monetary info, workers’ information, enterprise contracts, and e-mail correspondence.

Despite the fact that BlackSuit’s darkish internet leak web site was first noticed final Might and has since been up to date with dozens of latest victims, little is understood concerning the group behind this ransomware operation.
In June, the extremely lively Royal ransomware gang—believed to be the direct successor of the infamous Conti cybercrime group—started testing a brand new encryptor referred to as BlackSuit after rumors of a rebrand started surfacing in April.
Since then, Royal has rebranded into BlackSuit and reorganized right into a extra centralized operation, just like the mannequin they used once they have been a part of the Conti syndicate as Group 2 (Conti2).
The FBI and CISA revealed in a November joint advisory that the Royal ransomware gang had breached the networks of no less than 350 organizations worldwide since September 2022 and linked the operation to greater than $275 million in ransom calls for.




