Cloud internet hosting supplier Rackspace suffered a data breach exposing “restricted” buyer monitoring information after menace actors exploited a zero-day vulnerability in a third-party instrument utilized by the ScienceLogic SL1 platform.
ScienceLogic confirmed to BleepingComputer that they rapidly developed a patch to deal with the chance and distributed it to all impacted clients whereas nonetheless offering help the place wanted.
“We recognized a zero-day distant code execution vulnerability inside a non-ScienceLogic third-party utility that’s delivered with the SL1 package deal,” defined a press release from Jessica Lindberg, Vice President at ScienceLogic.
“Upon identification, we quickly developed a patch to remediate the incident and have made it accessible to all clients globally.”
ScienceLogic declined to call the third-party utility to keep away from offering hints to different hackers, because it may be used on a number of different merchandise.
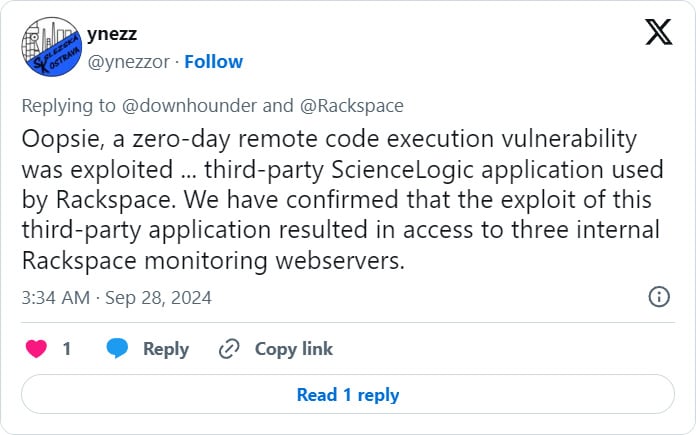
The assault was first disclosed by a person on X who warned {that a} Rackspace outage from September 24 was resulting from lively exploitation within the internet hosting supplier’s ScienceLogic EM7.
“Oopsie, a zero-day distant code execution vulnerability was exploited … third-party ScienceLogic utility utilized by Rackspace,” an account named ynezz shared on X.
“Now we have confirmed that the exploit of this third-party utility resulted in entry to 3 inside Rackspace monitoring webservers.”
ScienceLogic SL1 (previously EM7) is an IT operations platform for monitoring, analyzing, and automating a company’s infrastructure, together with cloud, networks, and purposes.
It gives real-time visibility, occasion correlation, and automatic workflows to assist handle and optimize IT environments effectively.
Rackspace, a managed cloud computing (internet hosting, storage, IT assist) firm, makes use of ScienceLogic SL1 to watch its IT infrastructure and providers.
In response to the invention of the malicious exercise, Rackspace disabled monitoring graphs on its MyRack portal till they might push an replace to remediate the chance.
Nevertheless, the scenario was worse than what a brief Rackspace service standing replace mirrored.
As first reported by The Register, Rackspace’s SL1 answer was hacked by way of the zero-day and a few buyer data was stolen.
In an e-mail despatched to clients and seen by The Register, Rackspace warned that the hackers exploited the zero-day to achieve entry to net servers and steal restricted buyer monitoring information, together with buyer account names and numbers, buyer usernames, Rackspace internally generated system IDs, system title and knowledge, IP addresses, and AES256 encrypted Rackspace inside system agent credentials.
Rackspace rotated these credentials as a precaution, regardless of them being strongly encrypted, and knowledgeable clients they wanted to take no additional motion to guard from the malicious exercise, which had been stopped.
Whereas the information is proscribed, it’s common for firms to cover their units’ IP addresses behind content material supply techniques and DDoS mitigation platforms. Risk actors may use the uncovered IP addresses to focus on firm’s units in DDoS assaults or additional exploitation makes an attempt.
It’s unknown what number of clients have been impacted by this breach.
BleepingComputer contacted RackSpace with additional questions however didn’t obtain a response.