The third day of Pwn2Own Eire 2024 continued to showcase the experience of white hat hackers as they uncovered 11 zero-day vulnerabilities, including $124,750 to the whole prize pool, which now stands at $874,875.
Pwn2Own, a world hacking competitors, challenges prime security researchers to take advantage of a spread of software program and {hardware} gadgets, with the final word purpose of incomes the celebrated “Grasp of Pwn” title and claiming as much as $1 million in rewards.
On Day 1, members uncovered 52 zero-day vulnerabilities, and on Day 2, one other 51 zero-days had been added.
Yesterday, the competitors noticed spectacular performances from groups representing Viettel Cyber Safety, DEVCORE, and PHP Hooligans/Midnight Blue, amongst others.
The day kicked off with success for Ha The Lengthy and Ha Anh Hoang from Viettel Cyber Safety, who exploited the QNAP TS-464 NAS utilizing a single command injection vulnerability. This profitable assault earned them $10,000 and 4 Grasp of Pwn factors.
Pumpkin Chang and Orange Tsai from the DEVCORE Analysis Workforce mixed three exploits—a CRLF injection, an authentication bypass, and a SQL injection—to take management of the Synology BeeStation. Their advanced exploit rewarded them with $20,000 and 4 factors.
PHP Hooligans / Midnight Blue used an out-of-bounds write and a reminiscence corruption bug to carry out a “SOHO Smashup.” They managed to go from the QNAP QHora-322 router to a Lexmark printer, finally printing their very own “banknotes,” incomes the group $25,000 and 10 Grasp of Pwn factors.

Supply: Zero Day Initiative
Later within the day, Viettel Cyber Safety delivered one other success, exploiting the Lexmark CX331adwe printer utilizing a sort confusion vulnerability, including $20,000 and a pair of extra factors to their tally.
Collisions and failed makes an attempt
Nonetheless, not all exploit makes an attempt went easily, and the third day had its share of collisions, the place a number of groups used the identical vulnerabilities to compromise gadgets.
STEALIEN Inc. efficiently compromised a Lorex digital camera, however the bug they leveraged had already been used, lowering their payout to $3,750 and awarding only one.5 factors.
Viettel Cyber Safety additionally encountered a collision after they exploited a Canon printer utilizing a stack-based buffer overflow, which had been beforehand demonstrated. This earned them $5,000 and 1 level.
Viettel Cyber Safety and ANHTUD confronted challenges when time ran out earlier than they might full their exploits, each whereas trying to breach the Ubiquiti AI Bullet inside the allotted time.
With simply 15 makes an attempt remaining within the schedule for Day 4, members have practically exhausted the prize pool, however there are nonetheless over $125,000 in awards up for grabs.
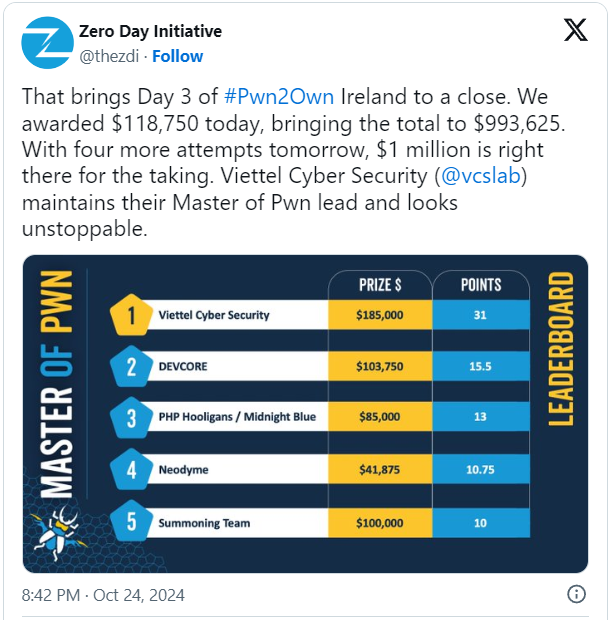
As the competition enters its closing section, Viettel Cyber Safety is comfortably main within the standings, having over twice the quantity of factors contenders DEVCORE, Neodyme, Summoning Workforce, and Ret2 Programs have gathered to this point.
On the finish of Day 3, the occasion revealed 114 zero-day vulnerabilities, showcasing the essential function of such competitions in strengthening the security of shopper gadgets.




