An intensive security audit of QNAP QTS, the working system for the corporate’s NAS merchandise, has uncovered fifteen vulnerabilities of various severity, with eleven remaining unfixed.
Amongst them is CVE-2024-27130, an unpatched stack buffer overflow vulnerability within the ‘No_Support_ACL’ perform of ‘share.cgi,’ which might allow an attacker to carry out distant code execution when particular stipulations are met.
The seller responded to the vulnerability reviews submitted between December 12, 2023, and January 23, 2024, with a number of delays and has fastened solely 4 of the fifteen flaws.
The vulnerabilities had been found by WatchTowr Labs, who revealed the entire particulars of their findings and a proof of idea (PoC) exploit for CVE-2024-27130 on Friday.
The QTS vulnerabilities
The failings uncovered by WatchTowr analysts are primarily associated to code execution, buffer overflows, reminiscence corruption, authentication bypass, and XSS points, impacting the security of Community Connected Storage (NAS) gadgets throughout totally different deployment environments.
WatchTowr lists a complete of fifteen flaws, summarized as follows:
- CVE-2023-50361: Unsafe use of sprintf in getQpkgDir invoked from userConfig.cgi.
- CVE-2023-50362: Unsafe use of SQLite capabilities accessible through parameter addPersonalSmtp to userConfig.cgi.
- CVE-2023-50363: Lacking authentication permits two-factor authentication to be disabled for arbitrary customers.
- CVE-2023-50364: Heap overflow through lengthy listing identify when file itemizing is seen by get_dirs perform of privWizard.cgi.
- CVE-2024-21902: Lacking authentication permits all customers to view or clear system logs and carry out extra actions.
- CVE-2024-27127: A double-free in utilRequest.cgi through the delete_share perform.
- CVE-2024-27128: Stack overflow in check_email perform, reachable through the share_file and send_share_mail actions of utilRequest.cgi.
- CVE-2024-27129: Unsafe use of strcpy in get_tree perform of utilRequest.cgi.
- CVE-2024-27130: Unsafe use of strcpy in No_Support_ACL accessible by get_file_size perform of share.cgi.
- CVE-2024-27131: Log spoofing through x-forwarded-for permits customers to trigger downloads to be recorded as requested from arbitrary supply areas.
- WT-2023-0050: Beneath prolonged embargo attributable to an unexpectedly complicated problem.
- WT-2024-0004: Saved XSS through distant syslog messages.
- WT-2024-0005: Saved XSS through distant gadget discovery.
- WT-2024-0006: Lack of rate-limiting on authentication API.
- WT-2024-00XX: Beneath 90-day embargo as per VDP.
The above bugs influence QTS, the NAS working system on QNAP gadgets, QuTScloud, the VM-optimized model of QTS, and QTS hero, a specialised model targeted on excessive efficiency.
QNAP has addressed CVE-2023-50361 by means of CVE-2023-50364 in a security replace launched in April 2024, in variations QTS 5.1.6.2722 construct 20240402 and later, and QuTS hero h5.1.6.2734 construct 20240414 and later.
Nonetheless, all the opposite vulnerabilities found by WatchTowr stay unaddressed.
PoC for zero-day RCE
The QNAP CVE-2024-27130 vulnerability is precipitated by the unsafe use of the ‘strcpy’ perform within the No_Support_ACL perform. This perform is utilized by the get_file_size request within the share.cgi script, used when sharing media with exterior customers.
An attacker can craft a malicious request with a specifically crafted ‘identify’ parameter, inflicting the buffer overflow resulting in distant code execution.
To use CVE-2024-27130, the attacker wants a legitimate ‘ssid’ parameter, which is generated when a NAS person shares a file from their QNAP gadget.
This parameter is included within the URL of the ‘share’ hyperlink created on a tool, so an attacker could be required to use some social engineering to realize entry to it. Nonetheless, BleepingComputer discovered that customers generally share these hyperlinks on-line, permitting them to be listed and retrieved from a easy Google search.
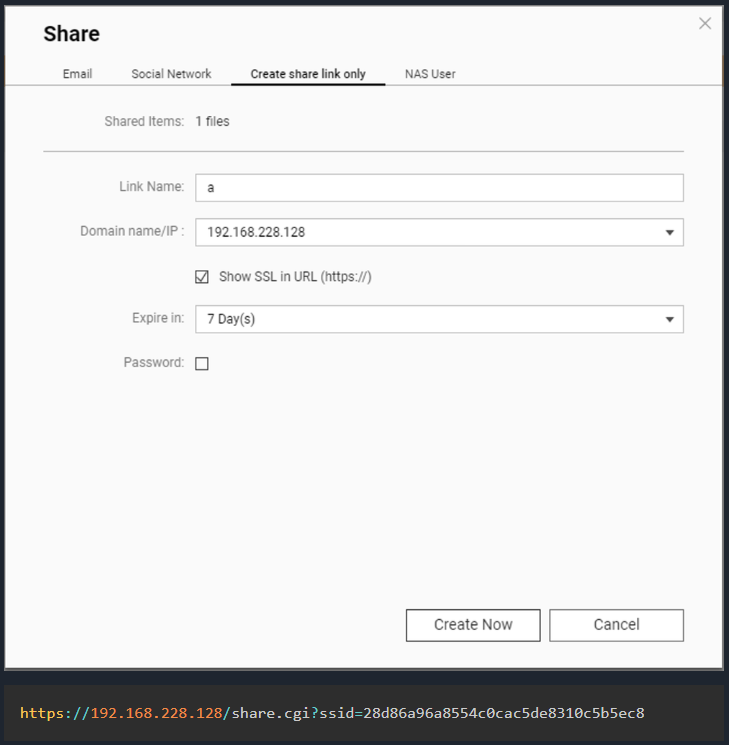
Supply: WatchTowr
In abstract, CVE-2024-27130 is not easy to take advantage of, but the SSID prerequisite may be met for decided actors.
WatchTowr revealed an exploit on GitHub, by which they exhibit methods to craft a payload that creates a ‘watchtowr’ account to a QNAP gadget and provides them to the sudoers for elevated privileges.
BleepingComputer has contacted QNAP for an announcement on the disclosed flaws, however a remark wasn’t instantly obtainable.




