The D-Hyperlink EXO AX4800 (DIR-X4860) router is susceptible to distant unauthenticated command execution that might result in full machine takeovers by attackers with entry to the HNAP port.
The D-Hyperlink DIR-X4860 router is a high-performance Wi-Fi 6 router able to speeds of as much as 4800 Mbps and superior options like OFDMA, MU-MIMO, and BSS Coloring that improve effectivity and cut back interference.
The machine is significantly common in Canada, and it is offered within the international market in response to D-Hyperlink’s web site, and nonetheless actively supported by the seller.
At present, the SSD Safe Disclosure group of researchers introduced that they found flaws in DIR-X4860 gadgets operating the most recent firmware model, DIRX4860A1_FWV1.04B03, which allows unauthenticated distant command execution (RCE).
“Safety vulnerabilities in DIR-X4860 permit distant unauthenticated attackers that may entry the HNAP port to realize elevated privileges and run instructions as root,” reads SSD’s disclosure.
“By combining an authentication bypass with command execution the machine may be fully compromised.”
Accessing the Residence Community Administration Protocol (HNAP) port on the D-Hyperlink DIR-X4860 router is comparatively simple typically, because it’s normally HTTP (port 80) or HTTPS (port 443) accessible via the router’s distant administration interface.
Exploitation course of
The SSD analysts have shared step-by-step exploitation directions for the problems they found, making a proof-of-concept (PoC) exploit now publicly obtainable.
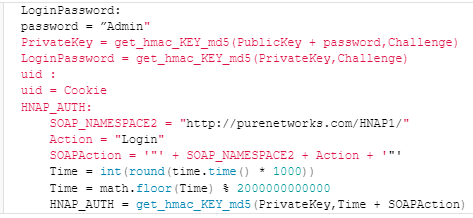
The assault begins with a specifically crafted HNAP login request to the router’s administration interface, which features a parameter named ‘PrivateLogin’ set to “Username” and a username of “Admin”.
The router responds with a problem, a cookie, and a public key, and these values are used to generate a sound login password for the “Admin” account.
A follow-up login request with the HNAP_AUTH header and the generated LoginPassword is distributed to the goal machine, primarily bypassing authentication.
Supply: SSD Safe Disclosure
With authenticated entry, the attacker then exploits a command injection vulnerability within the ‘SetVirtualServerSettings’ perform through a specifically crafted request.
The susceptible ‘SetVirtualServerSettings’ perform processes the ‘LocalIPAddress’ parameter with out correct sanitization, permitting the injected command to execute within the context of the router’s working system.
SSD says it has contacted D-Hyperlink 3 times to share its findings with the router maker over the previous 30 days, however all makes an attempt to inform them have been unsuccessful, leaving the failings at present unfixed.
BleepingComputer has additionally reached out to D-Hyperlink with a associated request, and we’re nonetheless ready for a remark.
Till a security firmware replace is made obtainable, customers of the DIR-X4860 ought to disable the machine’s distant entry administration interface to forestall exploitation.




