At present, Palo Alto Networks warns that an unpatched important command injection vulnerability in its PAN-OS firewall is being actively exploited in assaults.
“Palo Alto Networks is conscious of a restricted variety of assaults that leverage the exploitation of this vulnerability,” warns the Palo Alto security bulletin.
The flaw, which has been found by Volexity and is tracked as CVE-2024-3400, is a command injection vulnerability that obtained the utmost severity rating of 10.0 because it requires no particular privileges or consumer interplay to use.
The seller clarified that the problem impacts particular variations of PAN-OS software program when each the GlobalProtect gateway and gadget telemetry options are enabled.
“A command injection vulnerability within the GlobalProtect function of Palo Alto Networks PAN-OS software program for particular PAN-OS variations and distinct function configurations could allow an unauthenticated attacker to execute arbitrary code with root privileges on the firewall,” explains the Palo Alto Networks advisory.
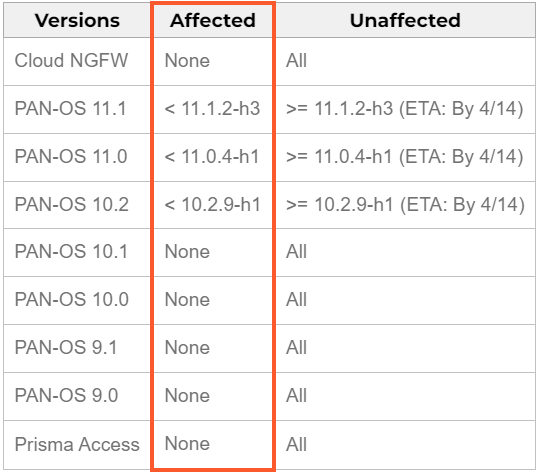
The weak variations are PAN-OS 10.2, 11.0, and 11.1, and fixes for these variations are anticipated by April 14, 2024. The seller will implement hotfixes by Sunday with the discharge of the next variations:
- PAN-OS 10.2.9-h1
- PAN-OS 11.0.4-h1
- PAN-OS 11.1.2-h3
Merchandise like Cloud NGFW, Panorama home equipment, and Prisma Entry are usually not affected. An outline of the impression may be seen within the desk beneath:
Menace researcher Yutaka Sejiyama reported on X that his scans present there are at present 82,000 uncovered gadgets on-line that may be weak to CVE-2024-34000, with 40% residing in the USA.
BleepingComputer contacted Volexity and Palo Alto Networks with questions on how the zero-day is being exploited.
Mitigating CVE-2024-3400
Since CVE-2024-3400 is already beneath lively exploitation, impacted customers should apply mitigations instantly to handle the chance till security updates can be found.
The advisory proposes implementing the next measures:
- Customers with an lively ‘Menace Prevention’ subscription can block assaults by activating ‘Menace ID 95187’ of their system.
- Be sure that vulnerability safety is configured on ‘GlobalProtect Interfaces’ to forestall exploitation. Extra information on that’s out there right here.
- Disable gadget telemetry till fixing patches are utilized. Directions on how you can do that may be discovered on this webpage.
Palo Alto Networks gadgets typically grow to be targets of subtle menace actors resulting from their deployment in company networks.
In August 2022, hackers exploited one other zero-day in PAN-OS to hold out amplified TCP denial-of-service (DoS) assaults.
This time, the problem is way more extreme, and its exploitation can be way more damaging to the targets, so admins should take immediate motion to safe their methods.




