Palo Alto Networks warns {that a} file learn vulnerability (CVE-2025-0111) is now being chained in assaults with two different flaws (CVE-2025-0108 with CVE-2024-9474) to breach PAN-OS firewalls in lively assaults.
The seller first disclosed the authentication bypass vulnerability tracked as CVE-2025-0108 on February 12, 2025, releasing patches to repair the vulnerability. That very same day, Assetnote researchers revealed a proof-of-concept exploit demonstrating how CVE-2025-0108 and CVE-2024-9474 could possibly be chained collectively to achieve root privileges on unpatched PAN-OS firewalls.
A day later, community menace intel agency GreyNoise reported that menace actors had begun actively exploiting the failings, with makes an attempt coming from two IP addresses.
CVE-2024-9474 is a privilege escalation flaw in PAN-OS fastened in November 2024 that enables a PAN-OS administrator to execute instructions on firewalls with root privileges. Palo Alto Networks warned on the disclosure that the vulnerability was exploited as a zero-day.
CVE-2025-0111 is a file learn vulnerability in PAN-OS, permitting authenticated attackers with community entry to the administration net interface to learn recordsdata which can be readable by the “no one” person.
The CVE-2025-0111 flaw was additionally fastened on February 12, 2025, however the vendor up to date its bulletin right now to warn that additionally it is now being utilized in an exploit chain with the opposite two vulnerabilities in lively assaults.
“Palo Alto Networks has noticed exploit makes an attempt chaining CVE-2025-0108 with CVE-2024-9474 and CVE-2025-0111 on unpatched and unsecured PAN-OS net administration interfaces,” reads the up to date bulletin.
Whereas Palo Alto Networks has not shared how the exploit chain is being abused, BleepingComputer has been advised they could possibly be chained collectively to obtain configuration recordsdata and different delicate data.
Exploitation exercise will increase
Not solely has the scope broadened, however an replace on GreyNoise’s bulletin signifies that the exploitation exercise has additionally elevated tempo.
GreyNoise stories now seeing 25 IP addresses concentrating on CVE-2025-0108, whereas its preliminary report from February 13 solely logged two.
The highest sources of the assaults are america, Germany, and the Netherlands, though this doesn’t imply the attackers are literally based mostly in these places.
Macnica researcher Yutaka Sejiyama advised BleepingComputer that his scans returned hundreds of PAN-OS units that expose their net administration interface to the web.
“For the newly patched CVE-2025-0108 and CVE-2025-0111, the vast majority of servers that publicly expose their net administration interface are nonetheless unpatched,” Sejiyama advised BleepingComputer.
“Out of three,490 servers going through the web, only some dozen have utilized the patch.”
Of those uncovered units, 1,168 haven’t patched CVE-2025-0108 and CVE-2025-0111 however have patched CVE-2024-9474.
The researcher stated that when contemplating all three flaws chained within the assaults, 65% (2,262 units) stay susceptible to all of them.
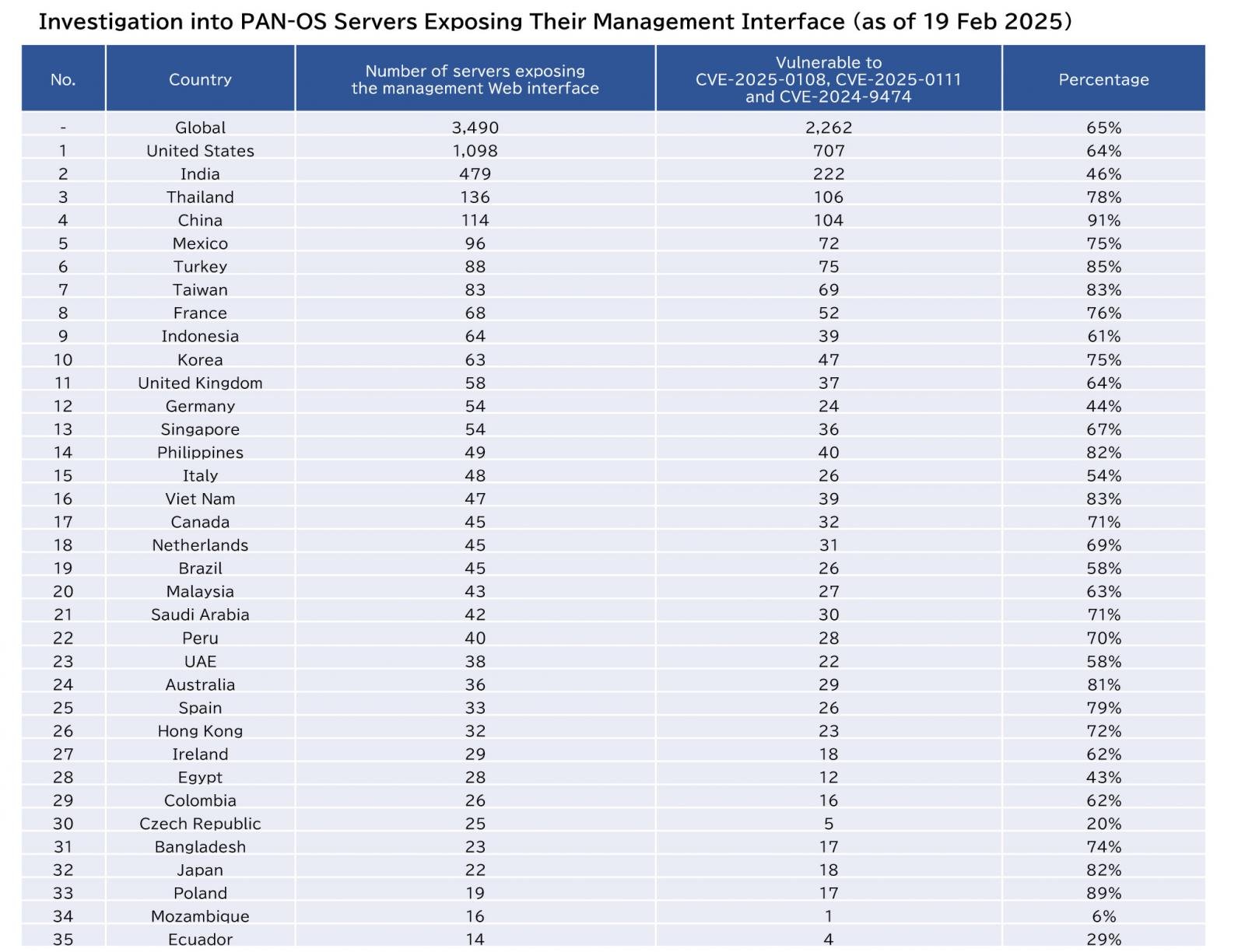
Supply: Sejiyama
Amidst this example and lively exploitation, the U.S. Cybersecurity & Infrastructure Safety Company (CISA) has added CVE-2025-0108 to its ‘Identified Exploited Vulnerabilities’ (KEV) catalog.
The group has given federal companies till March 11, 2025, to use the out there updates/mitigations or cease utilizing the product.
Replace 2/21 – Palo Alot Networks despatched BleepingComputer the next remark relating to the above:
Palo Alto Networks is urging clients to right away patch two vulnerabilities within the PAN-OS net administration interface – CVE-2025-0108 and CVE-2025-0111 . These vulnerabilities may enable unauthorized entry to the administration interface of affected firewalls, doubtlessly resulting in system compromise. Exploitation makes an attempt for CVE-2025-0108, which has a publicly out there proof-of-concept exploit, have been noticed chaining it with CVE-2024-9474 and CVE-2025-0111 on unpatched and unsecured PAN-OS net administration interfaces. We proceed to observe the state of affairs and leverage the at the moment operational mechanisms to detect buyer compromises in telemetry and TSFs and assist them by the EFR remediations
Prospects with any internet-facing PAN-OS administration interfaces are strongly urged to take instant motion to mitigate these vulnerabilities. Securing external-facing administration interfaces is a elementary security finest observe, and we strongly encourage all organizations to evaluation their configurations to attenuate danger.




