Safety researchers at Bitdefender have found 4 vulnerabilities impacting a number of variations of WebOS, the working system utilized in LG sensible TVs.
The failings allow various levels of unauthorized entry and management over affected fashions, together with authorization bypasses, privilege escalation, and command injection.
The potential assaults hinge on the flexibility to create arbitrary accounts on the system utilizing a service that runs on ports 3000/3001, which is out there for smartphone connectivity, utilizing a PIN.
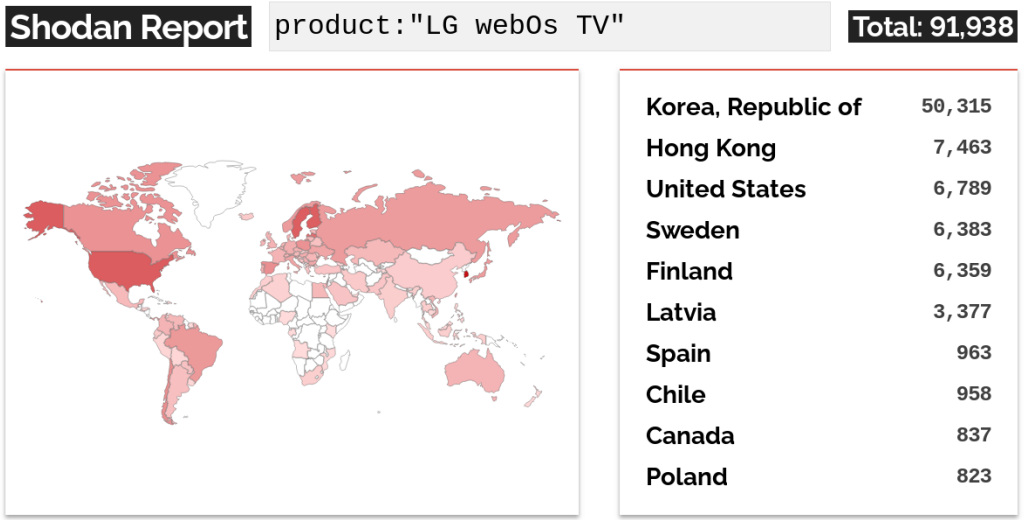
Bitdefender explains that though the susceptible LG WebOS service is meant for use solely in native space networks (LAN) settings, Shodan web scans present 91,000 uncovered units which can be doubtlessly susceptible to the failings.
The 4 flaws are summarized as follows:
- CVE-2023-6317 permits attackers to bypass the TV’s authorization mechanism by exploiting a variable setting, enabling the addition of an additional person to the TV set with out correct authorization.
- CVE-2023-6318 is an elevation of privilege vulnerability that permits attackers to achieve root entry following the preliminary unauthorized entry supplied by CVE-2023-6317.
- CVE-2023-6319 includes working system command injection through manipulation of a library answerable for displaying music lyrics, permitting execution of arbitrary instructions.
- CVE-2023-6320 permits authenticated command injection by exploiting the com.webos.service.connectionmanager/television/setVlanStaticAddress API endpoint, enabling command execution because the dbus person, which has related permissions to the basis person.
The vulnerabilities influence webOS 4.9.7 – 5.30.40 on LG43UM7000PLA, webOS 04.50.51 – 5.5.0 on OLED55CXPUA, webOS 0.36.50 – 6.3.3-442 on OLED48C1PUB, and webOS 03.33.85 – 7.3.1-43 on OLED55A23LA.
Bitdefender reported its findings to LG on November 1, 2023, however it took the seller till March 22, 2024, to launch the associated security updates.
Although LG TVs alert customers when vital WebOS updates can be found, these will be postponed indefinitely. Due to this fact, impacted customers ought to apply the replace by going to the TV’s Settings > Help > Software program Replace, and choosing “Verify for Replace.”
Making use of WebOS updates routinely when out there will be enabled from the identical menu.
Although TVs are much less important by way of security, the severity of distant command execution stays doubtlessly important on this case because it may give attackers a pivot level to succeed in different, extra delicate units linked to the identical community.
Furthermore, sensible TVs usually have functions that require accounts, like streaming companies, which the attacker may doubtlessly steal to take management of these accounts.
Lastly, susceptible TVs will be compromised by malware botnets that enlist them in distributed denial of service (DDoS) assaults or used for cryptomining.




