The evaluation of practically 20 million information-stealing malware logs bought on the darkish internet and Telegram channels revealed that they’d achieved vital infiltration into enterprise environments.
Data stealers are malware that steals knowledge saved in purposes similar to internet browsers, e mail shoppers, instantaneous messengers, cryptocurrency wallets, FTP shoppers, and gaming providers. The stolen info is packaged into archives known as ‘logs,’ that are then uploaded again to the risk actor to be used in assaults or bought on cybercrime marketplaces.
Probably the most outstanding information-stealing households are Redline, Raccoon, Titan, Aurora, and Vidar, supplied to cyber criminals on a subscription-based mannequin, permitting them to conduct malware campaigns that steal knowledge from contaminated gadgets.
Whereas info stealers primarily goal careless web customers who obtain software program, similar to cracks, warez, recreation cheats, and pretend software program from doubtful sources, it has additionally been discovered to have an enormous impression on company environments.
It’s because workers use private gadgets for work or entry private stuff from work computer systems, leading to many info-stealer infections stealing enterprise credentials and authentication cookies.
Extra particularly, as cybersecurity agency Flare explains in a new report shared with BleepingComputer, there are roughly 375,000 logs containing entry to enterprise purposes similar to Salesforce, Hubspot, Quickbooks, AWS, GCP, Okta, and DocuSign.
Extra particularly, Flare discovered the next within the examined stealer logs:
- 179,000 AWS Console credentials
- 2,300 Google Cloud credentials
- 64,500 DocuSign credentials
- 15,500 QuickBooks credentials
- 23,000 Salesforce credentials
- 66,000 CRM credentials
Along with the above, there are about 48,000 logs that embody entry to “okta.com,” an enterprise-grade id administration service utilized by organizations for cloud and on-premise consumer authentication.
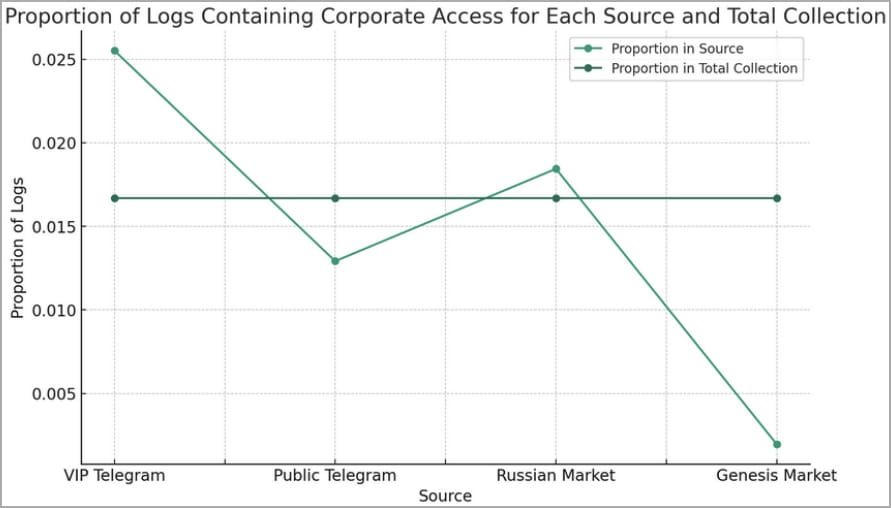
Most of those logs (74%) had been posted on Telegram channels, whereas 25% had been seen on Russian-speaking marketplaces, just like the ‘Russian Market.’
“Logs containing company entry had been over-represented on Russian Market and VIP Telegram channels, indicating that the strategies attackers use to reap logs could by the way or deliberately have extra company focusing on,” describes the Flare report.
“Moreover, public Telegram channels could intentionally submit decrease worth logs, saving high-value logs for paying clients.”
Flare additionally discovered greater than 200,000 stealer logs containing OpenAI credentials, which is double the quantity that Group-IB reported lately and constitutes a threat for leaking proprietary info, inner enterprise methods, supply code, and extra.
Company credentials are thought of “tier-1” logs, making them notably high-valued within the cybercrime underground, the place they’re bought on personal Telegram channels or boards like Exploit and XSS.
That worth is derived from the potential revenue cybercriminals could make by leveraging compromised credentials to entry CRMs, RDP, VPNs, and SaaS purposes after which utilizing that entry to deploy stealthy backdoors, ransomware, and different payloads.
“Primarily based on proof from the darkish internet discussion board Exploit in, we price it as extremely possible that preliminary entry brokers are utilizing stealer logs as a principal supply to achieve an preliminary foothold to company environments that may then be auctioned off on top-tier darkish internet boards,” explains Flare researcher Eric Clay.
It is suggested that companies decrease the chance of info-stealer malware infections by imposing the usage of password managers, implementing multi-factor authentication, and setting strict controls on private gadget use.
Moreover, workers must be educated to establish and keep away from widespread an infection channels similar to malicious Google Advertisements, YouTube movies, and Fb posts.




