Greater than 40,000 Cisco gadgets working the IOS XE working system have been compromised after hackers exploited a lately disclosed most severity vulnerability tracked as CVE-2023-20198.
There is no such thing as a patch or a workaround out there and the one suggestion for purchasers to safe the gadgets is to “disable the HTTP Server function on all internet-facing techniques.”
Networking gear working Cisco IOS XE consists of enterprise switches, industrial routers, entry factors, wi-fi controllers, aggregation, and department routers.
Tens of hundreds of Cisco gadgets uncovered
Preliminary estimates of breached Cisco IOS XE gadgets had been round 10,000 and the quantity began rising as security researchers scanned the web for a extra correct determine.
On Tuesday, the LeakIX engine for indexing providers and internet functions uncovered on the general public internet stated they discovered about 30,000 contaminated gadgets, with out counting the rebooted techniques.
The search relied on the symptoms of compromise (IoCs) that Cisco offered to find out the profitable exploitation of CVE-2023-20198 on an uncovered machine and revealed hundreds of contaminated hosts in the US, the Philippines, and Chile.
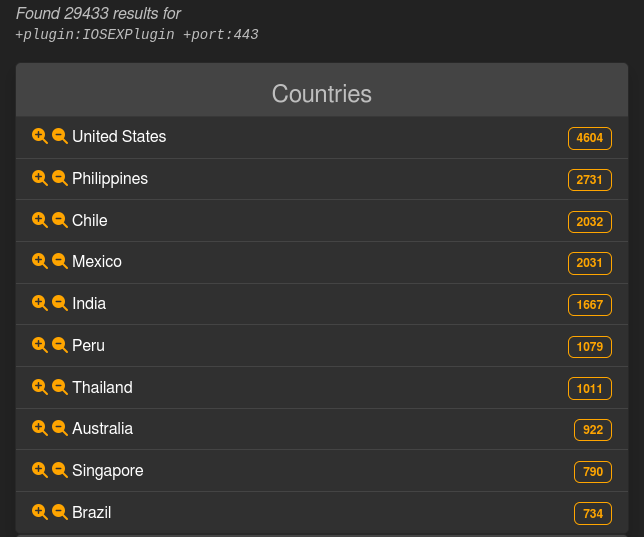
supply: LeakIX
Utilizing the identical verification technique from Cisco, the non-public CERT from Orange introduced on Wednesday that there have been greater than 34,500 Cisco IOS XE IP addresses with a malicious implant on account of exploiting CVE-2023-20198.
CERT Orange additionally revealed a Python script to scan for the presence of a malicious implant on a community machine working Cisco IOS XE.
In an replace on October 18, the Censys search platform for assessing assault floor for internet-connected gadgets stated that the variety of compromised gadgets it discovered elevated to 41,983.
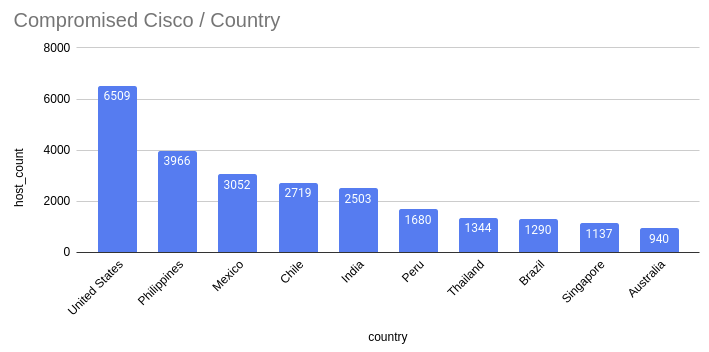
supply: Censys
A exact variety of Cisco IOS XE gadgets reachable over the general public web is tough to acquire however Shodan exhibits slightly over 145,000 hosts, most of them within the U.S.
Beneath is a screenshot with Shodan outcomes for Cisco gadgets which have their Net UI accessible over the web, utilizing a question from Simo Kohonen, the CEO of Aves Netsec cybersecurity firm.
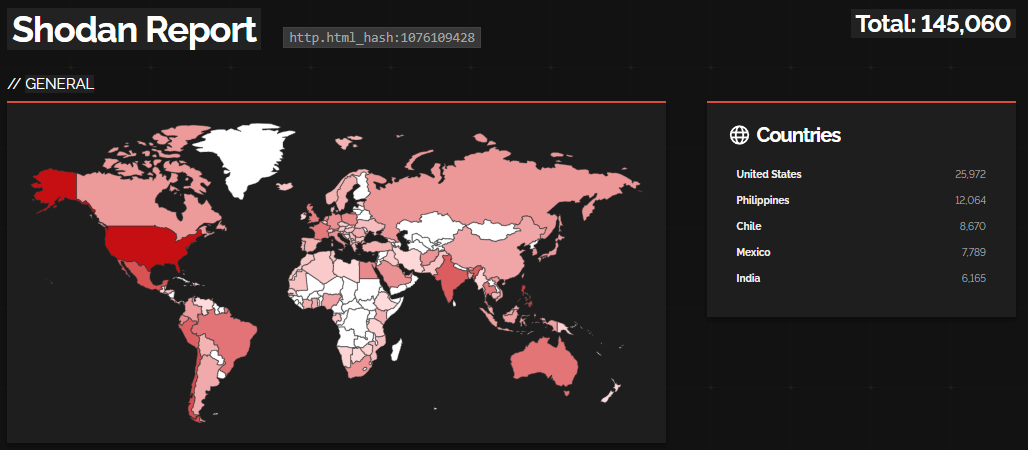
supply: BleepingComputer
Safety researcher Yutaka Sejiyama additionally searched Shodan for Cisco IOS XE gadgets weak to CVE-2023-20198 and located near 90,000 hosts uncovered on the net.
Within the U.S., lots of the gadgets are from communications suppliers reminiscent of Comcast, Verizon, Cox Communications, Frontier, AT&T, Spirit, CenturyLink, Constitution, Cobridge, Windstream, and Google Fiber.
Sejiyama’s listing additionally consists of medical facilities, universities, sheriff’s workplaces, faculty districts, comfort shops, banks, hospitals, and authorities entities with Cisco IOS XE gadgets uncovered on-line.
“There is no such thing as a want to show the IOS XE login display on the Web within the first place,” Sejiyama informed BleepingComputer, echoing Cisco’s recommendation of not exposing the online UI and administration providers to the general public internet or to untrusted networks.
The researcher expressed concern at this practices, saying that “organizations utilizing the gear in such a fashion are prone to be unaware of this vulnerability or breach.”
Danger persists after machine reboot
Cisco disclosed CVE-2023-20198 on Monday however menace actors had been leveraging it earlier than September 28, when it was a zero-day, to create a high-privilege account on affected hosts and take full management of the machine.
Cisco up to date its advisory at present with new attacker IP addresses and usernames, in addition to recent guidelines for the Snort open-source community intrusion detection system and intrusion prevention system.
The researchers be aware that menace actors behind these assaults use a malicious implant, which doesn’t have persistence and is eliminated after rebooting the machine.
Nonetheless, the brand new accounts it helped create proceed to be energetic and “have degree 15 privileges, that means they’ve full administrator entry to the machine.”
Based mostly on Cisco’s evaluation, the menace actor collects particulars in regards to the machine and carries out preliminary reconnaissance exercise. The attacker can also be clearing logs and eradicating customers, in all probability to cover their exercise.
The researchers imagine that behind these assaults is just one menace actor however couldn’t decide the preliminary supply mechanism.
Cisco has not disclosed extra particulars in regards to the assaults however promised to supply extra data when it completes the investigation and when a repair is on the market.




