Over 3,300 Citrix NetScaler gadgets stay unpatched in opposition to a essential vulnerability that enables attackers to bypass authentication by hijacking person periods, almost two months after patches have been launched.
Tracked as CVE-2025-5777 and known as CitrixBleed 2, this out-of-bounds reminiscence learn vulnerability outcomes from inadequate enter validation, enabling unauthenticated attackers to entry restricted reminiscence areas remotely on gadgets configured as a Gateway (VPN digital server, ICA Proxy, CVPN, RDP Proxy) or AAA digital server.
Efficiently exploiting this security flaw might allow risk actors to steal session tokens, credentials, and different delicate information from public-facing gateways and digital servers, permitting them to hijack person periods and bypass multi-factor authentication (MFA).
Proof-of-concept (PoC) exploits focusing on CVE-2025-5777 have been launched lower than two weeks after the flaw was disclosed, whereas energetic exploitation in zero-day assaults was detected weeks earlier than the discharge of those PoC exploits.
An identical Citrix security flaw, often called “CitrixBleed,” was exploited two years in the past to hack NetScaler gadgets and transfer laterally throughout compromised networks in ransomware assaults and breaches focusing on authorities entities.
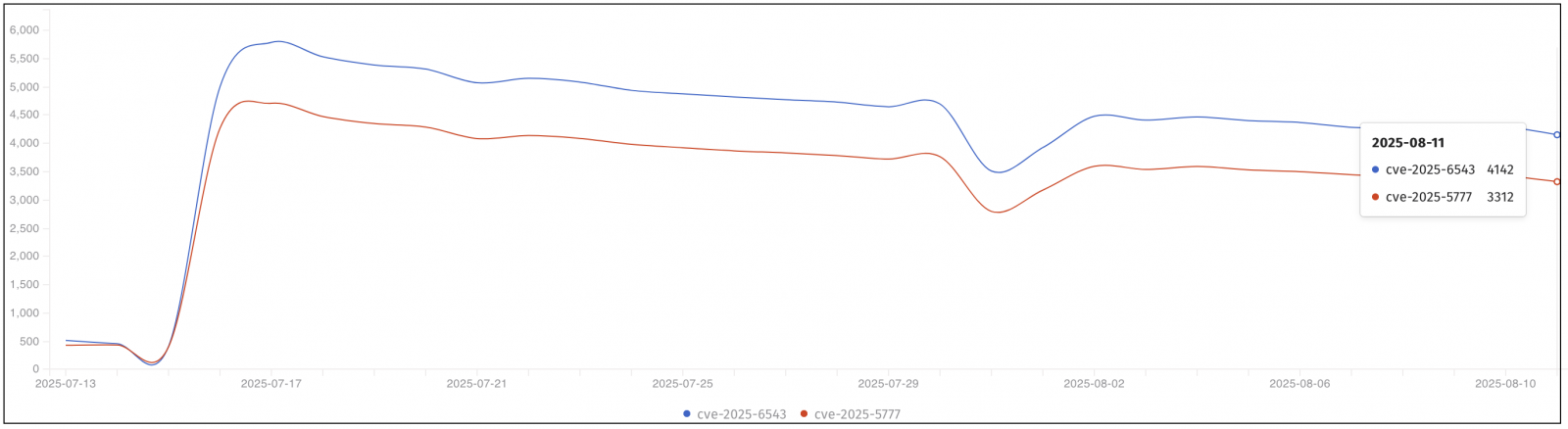
On Monday, security analysts from the web security nonprofit Shadowserver Basis reported that 3,312 Citrix NetScaler home equipment have been nonetheless susceptible to ongoing CVE-2025-5777 assaults.
Shadowserver additionally noticed 4,142 such gadgets left unpatched in opposition to one other essential vulnerability (CVE-2025-6543), which Citrix has tagged as actively exploited in denial-of-service (DoS) assaults.
Whereas Citrix states that CVE-2025-6543 is a reminiscence overflow vulnerability that may result in unintended management stream and denial of service, the Netherlands’ Nationwide Cyber Safety Centre (NCSC) warned on Monday that attackers have exploited this flaw as a zero-day since no less than early Might to breach a number of essential organizations within the nation.
“The NCSC has decided that a number of essential organizations within the Netherlands have been efficiently attacked through a vulnerability recognized as CVE-2025-6543 in Citrix NetScaler,” the NCSC mentioned..
“The NCSC assesses the assaults because the work of a number of actors with a complicated modus operandi. The vulnerability was exploited as a zero-day, and traces have been actively eliminated to hide compromise at affected organizations.”
Though the company didn’t title any of the affected organizations, the Openbaar Ministerie (the Netherlands’ Public Prosecution Service) disclosed a breach on July 18th following an NCSC alert. On account of the assault, the Openbaar Ministerie skilled vital operational disruption and solely lately restored its e-mail servers.
The U.S. Cybersecurity and Infrastructure Safety Company (CISA) has additionally added the 2 vulnerabilities to its catalog of actively exploited vulnerabilities, ordering federal businesses to safe their programs in opposition to CVE-2025-5777 assaults inside a day and in opposition to CVE-2025-6543 exploitation by July twenty first.

46% of environments had passwords cracked, almost doubling from 25% final 12 months.
Get the Picus Blue Report 2025 now for a complete take a look at extra findings on prevention, detection, and information exfiltration developments.




